2017-04-25 09:24:51 +02:00
|
|
|
// Copyright 2017 The Gitea Authors. All rights reserved.
|
2022-11-27 19:20:29 +01:00
|
|
|
// SPDX-License-Identifier: MIT
|
2017-04-25 09:24:51 +02:00
|
|
|
|
2021-06-09 01:33:54 +02:00
|
|
|
package web
|
2017-04-25 09:24:51 +02:00
|
|
|
|
|
|
|
|
import (
|
2022-02-05 19:26:12 +01:00
|
|
|
gocontext "context"
|
2021-01-26 16:36:53 +01:00
|
|
|
"net/http"
|
2023-09-12 08:15:16 +02:00
|
|
|
"strings"
|
2017-04-25 09:24:51 +02:00
|
|
|
|
2023-09-18 01:32:56 +02:00
|
|
|
auth_model "code.gitea.io/gitea/models/auth"
|
2023-10-11 06:24:07 +02:00
|
|
|
"code.gitea.io/gitea/models/db"
|
2022-03-30 10:42:47 +02:00
|
|
|
"code.gitea.io/gitea/models/perm"
|
2021-11-09 20:57:58 +01:00
|
|
|
"code.gitea.io/gitea/models/unit"
|
2017-04-25 09:24:51 +02:00
|
|
|
"code.gitea.io/gitea/modules/context"
|
|
|
|
|
"code.gitea.io/gitea/modules/log"
|
2021-01-26 16:36:53 +01:00
|
|
|
"code.gitea.io/gitea/modules/metrics"
|
|
|
|
|
"code.gitea.io/gitea/modules/public"
|
2017-04-25 09:24:51 +02:00
|
|
|
"code.gitea.io/gitea/modules/setting"
|
2021-01-26 16:36:53 +01:00
|
|
|
"code.gitea.io/gitea/modules/storage"
|
2022-04-07 20:59:56 +02:00
|
|
|
"code.gitea.io/gitea/modules/structs"
|
2022-08-28 11:43:25 +02:00
|
|
|
"code.gitea.io/gitea/modules/templates"
|
2017-04-25 09:24:51 +02:00
|
|
|
"code.gitea.io/gitea/modules/validation"
|
2021-01-26 16:36:53 +01:00
|
|
|
"code.gitea.io/gitea/modules/web"
|
2023-09-12 08:15:16 +02:00
|
|
|
"code.gitea.io/gitea/modules/web/middleware"
|
2022-01-20 12:41:25 +01:00
|
|
|
"code.gitea.io/gitea/modules/web/routing"
|
2023-04-27 08:06:45 +02:00
|
|
|
"code.gitea.io/gitea/routers/common"
|
2021-06-09 01:33:54 +02:00
|
|
|
"code.gitea.io/gitea/routers/web/admin"
|
2022-01-02 14:12:35 +01:00
|
|
|
"code.gitea.io/gitea/routers/web/auth"
|
2023-04-03 12:06:57 +02:00
|
|
|
"code.gitea.io/gitea/routers/web/devtest"
|
2021-06-09 01:33:54 +02:00
|
|
|
"code.gitea.io/gitea/routers/web/events"
|
|
|
|
|
"code.gitea.io/gitea/routers/web/explore"
|
2022-03-26 10:04:22 +01:00
|
|
|
"code.gitea.io/gitea/routers/web/feed"
|
2022-05-04 13:56:20 +02:00
|
|
|
"code.gitea.io/gitea/routers/web/healthcheck"
|
2022-04-08 06:22:10 +02:00
|
|
|
"code.gitea.io/gitea/routers/web/misc"
|
2021-06-09 01:33:54 +02:00
|
|
|
"code.gitea.io/gitea/routers/web/org"
|
2023-04-28 02:08:47 +02:00
|
|
|
org_setting "code.gitea.io/gitea/routers/web/org/setting"
|
2021-06-09 01:33:54 +02:00
|
|
|
"code.gitea.io/gitea/routers/web/repo"
|

Implement actions (#21937)
Close #13539.
Co-authored by: @lunny @appleboy @fuxiaohei and others.
Related projects:
- https://gitea.com/gitea/actions-proto-def
- https://gitea.com/gitea/actions-proto-go
- https://gitea.com/gitea/act
- https://gitea.com/gitea/act_runner
### Summary
The target of this PR is to bring a basic implementation of "Actions",
an internal CI/CD system of Gitea. That means even though it has been
merged, the state of the feature is **EXPERIMENTAL**, and please note
that:
- It is disabled by default;
- It shouldn't be used in a production environment currently;
- It shouldn't be used in a public Gitea instance currently;
- Breaking changes may be made before it's stable.
**Please comment on #13539 if you have any different product design
ideas**, all decisions reached there will be adopted here. But in this
PR, we don't talk about **naming, feature-creep or alternatives**.
### ⚠️ Breaking
`gitea-actions` will become a reserved user name. If a user with the
name already exists in the database, it is recommended to rename it.
### Some important reviews
- What is `DEFAULT_ACTIONS_URL` in `app.ini` for?
- https://github.com/go-gitea/gitea/pull/21937#discussion_r1055954954
- Why the api for runners is not under the normal `/api/v1` prefix?
- https://github.com/go-gitea/gitea/pull/21937#discussion_r1061173592
- Why DBFS?
- https://github.com/go-gitea/gitea/pull/21937#discussion_r1061301178
- Why ignore events triggered by `gitea-actions` bot?
- https://github.com/go-gitea/gitea/pull/21937#discussion_r1063254103
- Why there's no permission control for actions?
- https://github.com/go-gitea/gitea/pull/21937#discussion_r1090229868
### What it looks like
<details>
#### Manage runners
<img width="1792" alt="image"
src="https://user-images.githubusercontent.com/9418365/205870657-c72f590e-2e08-4cd4-be7f-2e0abb299bbf.png">
#### List runs
<img width="1792" alt="image"
src="https://user-images.githubusercontent.com/9418365/205872794-50fde990-2b45-48c1-a178-908e4ec5b627.png">
#### View logs
<img width="1792" alt="image"
src="https://user-images.githubusercontent.com/9418365/205872501-9b7b9000-9542-4991-8f55-18ccdada77c3.png">
</details>
### How to try it
<details>
#### 1. Start Gitea
Clone this branch and [install from
source](https://docs.gitea.io/en-us/install-from-source).
Add additional configurations in `app.ini` to enable Actions:
```ini
[actions]
ENABLED = true
```
Start it.
If all is well, you'll see the management page of runners:
<img width="1792" alt="image"
src="https://user-images.githubusercontent.com/9418365/205877365-8e30a780-9b10-4154-b3e8-ee6c3cb35a59.png">
#### 2. Start runner
Clone the [act_runner](https://gitea.com/gitea/act_runner), and follow
the
[README](https://gitea.com/gitea/act_runner/src/branch/main/README.md)
to start it.
If all is well, you'll see a new runner has been added:
<img width="1792" alt="image"
src="https://user-images.githubusercontent.com/9418365/205878000-216f5937-e696-470d-b66c-8473987d91c3.png">
#### 3. Enable actions for a repo
Create a new repo or open an existing one, check the `Actions` checkbox
in settings and submit.
<img width="1792" alt="image"
src="https://user-images.githubusercontent.com/9418365/205879705-53e09208-73c0-4b3e-a123-2dcf9aba4b9c.png">
<img width="1792" alt="image"
src="https://user-images.githubusercontent.com/9418365/205879383-23f3d08f-1a85-41dd-a8b3-54e2ee6453e8.png">
If all is well, you'll see a new tab "Actions":
<img width="1792" alt="image"
src="https://user-images.githubusercontent.com/9418365/205881648-a8072d8c-5803-4d76-b8a8-9b2fb49516c1.png">
#### 4. Upload workflow files
Upload some workflow files to `.gitea/workflows/xxx.yaml`, you can
follow the [quickstart](https://docs.github.com/en/actions/quickstart)
of GitHub Actions. Yes, Gitea Actions is compatible with GitHub Actions
in most cases, you can use the same demo:
```yaml
name: GitHub Actions Demo
run-name: ${{ github.actor }} is testing out GitHub Actions 🚀
on: [push]
jobs:
Explore-GitHub-Actions:
runs-on: ubuntu-latest
steps:
- run: echo "🎉 The job was automatically triggered by a ${{ github.event_name }} event."
- run: echo "🐧 This job is now running on a ${{ runner.os }} server hosted by GitHub!"
- run: echo "🔎 The name of your branch is ${{ github.ref }} and your repository is ${{ github.repository }}."
- name: Check out repository code
uses: actions/checkout@v3
- run: echo "💡 The ${{ github.repository }} repository has been cloned to the runner."
- run: echo "🖥️ The workflow is now ready to test your code on the runner."
- name: List files in the repository
run: |
ls ${{ github.workspace }}
- run: echo "🍏 This job's status is ${{ job.status }}."
```
If all is well, you'll see a new run in `Actions` tab:
<img width="1792" alt="image"
src="https://user-images.githubusercontent.com/9418365/205884473-79a874bc-171b-4aaf-acd5-0241a45c3b53.png">
#### 5. Check the logs of jobs
Click a run and you'll see the logs:
<img width="1792" alt="image"
src="https://user-images.githubusercontent.com/9418365/205884800-994b0374-67f7-48ff-be9a-4c53f3141547.png">
#### 6. Go on
You can try more examples in [the
documents](https://docs.github.com/en/actions/using-workflows/workflow-syntax-for-github-actions)
of GitHub Actions, then you might find a lot of bugs.
Come on, PRs are welcome.
</details>
See also: [Feature Preview: Gitea
Actions](https://blog.gitea.io/2022/12/feature-preview-gitea-actions/)
---------
Co-authored-by: a1012112796 <1012112796@qq.com>
Co-authored-by: Lunny Xiao <xiaolunwen@gmail.com>
Co-authored-by: delvh <dev.lh@web.de>
Co-authored-by: ChristopherHX <christopher.homberger@web.de>
Co-authored-by: John Olheiser <john.olheiser@gmail.com>
2023-01-31 02:45:19 +01:00
|
|
|
"code.gitea.io/gitea/routers/web/repo/actions"
|
2023-04-28 02:08:47 +02:00
|
|
|
repo_setting "code.gitea.io/gitea/routers/web/repo/setting"
|
2021-06-09 01:33:54 +02:00
|
|
|
"code.gitea.io/gitea/routers/web/user"
|
2022-01-02 14:12:35 +01:00
|
|
|
user_setting "code.gitea.io/gitea/routers/web/user/setting"
|
|
|
|
|
"code.gitea.io/gitea/routers/web/user/setting/security"
|
|
|
|
|
auth_service "code.gitea.io/gitea/services/auth"
|
2022-03-26 10:04:22 +01:00
|
|
|
context_service "code.gitea.io/gitea/services/context"
|
2021-04-06 21:44:05 +02:00
|
|
|
"code.gitea.io/gitea/services/forms"
|
2021-04-09 00:25:57 +02:00
|
|
|
"code.gitea.io/gitea/services/lfs"
|
2017-04-25 09:24:51 +02:00
|
|
|
|
2021-11-17 13:34:35 +01:00
|
|
|
_ "code.gitea.io/gitea/modules/session" // to registers all internal adapters
|
2019-07-17 03:04:37 +02:00
|
|
|
|
2021-01-26 16:36:53 +01:00
|
|
|
"gitea.com/go-chi/captcha"
|
|
|
|
|
"github.com/NYTimes/gziphandler"
|
2023-09-12 08:15:16 +02:00
|
|
|
chi_middleware "github.com/go-chi/chi/v5/middleware"
|
2021-03-04 02:25:30 +01:00
|
|
|
"github.com/go-chi/cors"
|
2021-01-26 16:36:53 +01:00
|
|
|
"github.com/prometheus/client_golang/prometheus"
|
2017-04-25 09:24:51 +02:00
|
|
|
)
|
|
|
|
|
|
2021-01-26 16:36:53 +01:00
|
|
|
const (
|
|
|
|
|
// GzipMinSize represents min size to compress for the body size of response
|
|
|
|
|
GzipMinSize = 1400
|
|
|
|
|
)
|
2020-11-13 13:51:07 +01:00
|
|
|
|
2021-06-09 01:33:54 +02:00
|
|
|
// CorsHandler return a http handler who set CORS options if enabled by config
|
|
|
|
|
func CorsHandler() func(next http.Handler) http.Handler {
|
2021-05-30 12:25:11 +02:00
|
|
|
if setting.CORSConfig.Enabled {
|
2021-06-09 01:33:54 +02:00
|
|
|
return cors.Handler(cors.Options{
|
2022-01-20 18:46:10 +01:00
|
|
|
// Scheme: setting.CORSConfig.Scheme, // FIXME: the cors middleware needs scheme option
|
2021-05-30 12:25:11 +02:00
|
|
|
AllowedOrigins: setting.CORSConfig.AllowDomain,
|
2022-01-20 18:46:10 +01:00
|
|
|
// setting.CORSConfig.AllowSubdomain // FIXME: the cors middleware needs allowSubdomain option
|
2021-05-30 12:25:11 +02:00
|
|
|
AllowedMethods: setting.CORSConfig.Methods,
|
|
|
|
|
AllowCredentials: setting.CORSConfig.AllowCredentials,
|
2022-11-11 07:39:27 +01:00
|
|
|
AllowedHeaders: setting.CORSConfig.Headers,
|
2021-05-30 12:25:11 +02:00
|
|
|
MaxAge: int(setting.CORSConfig.MaxAge.Seconds()),
|
|
|
|
|
})
|
|
|
|
|
}
|
|
|
|
|
|
2021-06-09 01:33:54 +02:00
|
|
|
return func(next http.Handler) http.Handler {
|
|
|
|
|
return next
|
|
|
|
|
}
|
2021-01-26 16:36:53 +01:00
|
|
|
}
|
2017-04-25 09:24:51 +02:00
|
|
|
|
2022-03-28 06:46:28 +02:00
|
|
|
// The OAuth2 plugin is expected to be executed first, as it must ignore the user id stored
|
|
|
|
|
// in the session (if there is a user id stored in session other plugins might return the user
|
|
|
|
|
// object for that id).
|
|
|
|
|
//
|
|
|
|
|
// The Session plugin is expected to be executed second, in order to skip authentication
|
|
|
|
|
// for users that have already signed in.
|
|
|
|
|
func buildAuthGroup() *auth_service.Group {
|
|
|
|
|
group := auth_service.NewGroup(
|
Fix various typos (#20338)
* Fix various typos
Found via `codespell -q 3 -S ./options/locale,./options/license,./public/vendor -L actived,allways,attachements,ba,befores,commiter,pullrequest,pullrequests,readby,splitted,te,unknwon`
Co-authored-by: zeripath <art27@cantab.net>
2022-07-12 23:32:37 +02:00
|
|
|
&auth_service.OAuth2{}, // FIXME: this should be removed and only applied in download and oauth related routers
|
2022-03-28 06:46:28 +02:00
|
|
|
&auth_service.Basic{}, // FIXME: this should be removed and only applied in download and git/lfs routers
|
2022-04-08 06:22:10 +02:00
|
|
|
&auth_service.Session{},
|
2022-03-28 06:46:28 +02:00
|
|
|
)
|
|
|
|
|
if setting.Service.EnableReverseProxyAuth {
|
|
|
|
|
group.Add(&auth_service.ReverseProxy{})
|
|
|
|
|
}
|
2023-09-18 01:32:56 +02:00
|
|
|
|
2023-10-11 06:24:07 +02:00
|
|
|
if setting.IsWindows && auth_model.IsSSPIEnabled(db.DefaultContext) {
|
2023-09-18 01:32:56 +02:00
|
|
|
group.Add(&auth_service.SSPI{}) // it MUST be the last, see the comment of SSPI
|
|
|
|
|
}
|
2022-03-28 06:46:28 +02:00
|
|
|
|
|
|
|
|
return group
|
|
|
|
|
}
|
|
|
|
|
|
2023-09-12 08:15:16 +02:00
|
|
|
func webAuth(authMethod auth_service.Method) func(*context.Context) {
|
|
|
|
|
return func(ctx *context.Context) {
|
|
|
|
|
ar, err := common.AuthShared(ctx.Base, ctx.Session, authMethod)
|
|
|
|
|
if err != nil {
|
|
|
|
|
log.Error("Failed to verify user: %v", err)
|
|
|
|
|
ctx.Error(http.StatusUnauthorized, "Verify")
|
|
|
|
|
return
|
|
|
|
|
}
|
|
|
|
|
ctx.Doer = ar.Doer
|
|
|
|
|
ctx.IsSigned = ar.Doer != nil
|
|
|
|
|
ctx.IsBasicAuth = ar.IsBasicAuth
|
|
|
|
|
if ctx.Doer == nil {
|
|
|
|
|
// ensure the session uid is deleted
|
|
|
|
|
_ = ctx.Session.Delete("uid")
|
|
|
|
|
}
|
|
|
|
|
}
|
|
|
|
|
}
|
|
|
|
|
|
|
|
|
|
// verifyAuthWithOptions checks authentication according to options
|
|
|
|
|
func verifyAuthWithOptions(options *common.VerifyOptions) func(ctx *context.Context) {
|
|
|
|
|
return func(ctx *context.Context) {
|
|
|
|
|
// Check prohibit login users.
|
|
|
|
|
if ctx.IsSigned {
|
|
|
|
|
if !ctx.Doer.IsActive && setting.Service.RegisterEmailConfirm {
|
|
|
|
|
ctx.Data["Title"] = ctx.Tr("auth.active_your_account")
|
|
|
|
|
ctx.HTML(http.StatusOK, "user/auth/activate")
|
|
|
|
|
return
|
|
|
|
|
}
|
|
|
|
|
if !ctx.Doer.IsActive || ctx.Doer.ProhibitLogin {
|
|
|
|
|
log.Info("Failed authentication attempt for %s from %s", ctx.Doer.Name, ctx.RemoteAddr())
|
|
|
|
|
ctx.Data["Title"] = ctx.Tr("auth.prohibit_login")
|
|
|
|
|
ctx.HTML(http.StatusOK, "user/auth/prohibit_login")
|
|
|
|
|
return
|
|
|
|
|
}
|
|
|
|
|
|
|
|
|
|
if ctx.Doer.MustChangePassword {
|
|
|
|
|
if ctx.Req.URL.Path != "/user/settings/change_password" {
|
|
|
|
|
if strings.HasPrefix(ctx.Req.UserAgent(), "git") {
|
|
|
|
|
ctx.Error(http.StatusUnauthorized, ctx.Tr("auth.must_change_password"))
|
|
|
|
|
return
|
|
|
|
|
}
|
|
|
|
|
ctx.Data["Title"] = ctx.Tr("auth.must_change_password")
|
|
|
|
|
ctx.Data["ChangePasscodeLink"] = setting.AppSubURL + "/user/change_password"
|
|
|
|
|
if ctx.Req.URL.Path != "/user/events" {
|
|
|
|
|
middleware.SetRedirectToCookie(ctx.Resp, setting.AppSubURL+ctx.Req.URL.RequestURI())
|
|
|
|
|
}
|
|
|
|
|
ctx.Redirect(setting.AppSubURL + "/user/settings/change_password")
|
|
|
|
|
return
|
|
|
|
|
}
|
|
|
|
|
} else if ctx.Req.URL.Path == "/user/settings/change_password" {
|
|
|
|
|
// make sure that the form cannot be accessed by users who don't need this
|
|
|
|
|
ctx.Redirect(setting.AppSubURL + "/")
|
|
|
|
|
return
|
|
|
|
|
}
|
|
|
|
|
}
|
|
|
|
|
|
|
|
|
|
// Redirect to dashboard (or alternate location) if user tries to visit any non-login page.
|
|
|
|
|
if options.SignOutRequired && ctx.IsSigned && ctx.Req.URL.RequestURI() != "/" {
|
|
|
|
|
ctx.RedirectToFirst(ctx.FormString("redirect_to"))
|
|
|
|
|
return
|
|
|
|
|
}
|
|
|
|
|
|
|
|
|
|
if !options.SignOutRequired && !options.DisableCSRF && ctx.Req.Method == "POST" {
|
|
|
|
|
ctx.Csrf.Validate(ctx)
|
|
|
|
|
if ctx.Written() {
|
|
|
|
|
return
|
|
|
|
|
}
|
|
|
|
|
}
|
|
|
|
|
|
|
|
|
|
if options.SignInRequired {
|
|
|
|
|
if !ctx.IsSigned {
|
|
|
|
|
if ctx.Req.URL.Path != "/user/events" {
|
|
|
|
|
middleware.SetRedirectToCookie(ctx.Resp, setting.AppSubURL+ctx.Req.URL.RequestURI())
|
|
|
|
|
}
|
|
|
|
|
ctx.Redirect(setting.AppSubURL + "/user/login")
|
|
|
|
|
return
|
|
|
|
|
} else if !ctx.Doer.IsActive && setting.Service.RegisterEmailConfirm {
|
|
|
|
|
ctx.Data["Title"] = ctx.Tr("auth.active_your_account")
|
|
|
|
|
ctx.HTML(http.StatusOK, "user/auth/activate")
|
|
|
|
|
return
|
|
|
|
|
}
|
|
|
|
|
}
|
|
|
|
|
|
|
|
|
|
// Redirect to log in page if auto-signin info is provided and has not signed in.
|
|
|
|
|
if !options.SignOutRequired && !ctx.IsSigned &&
|
2023-10-14 02:56:41 +02:00
|
|
|
ctx.GetSiteCookie(setting.CookieRememberName) != "" {
|
2023-09-12 08:15:16 +02:00
|
|
|
if ctx.Req.URL.Path != "/user/events" {
|
|
|
|
|
middleware.SetRedirectToCookie(ctx.Resp, setting.AppSubURL+ctx.Req.URL.RequestURI())
|
|
|
|
|
}
|
|
|
|
|
ctx.Redirect(setting.AppSubURL + "/user/login")
|
|
|
|
|
return
|
|
|
|
|
}
|
|
|
|
|
|
|
|
|
|
if options.AdminRequired {
|
|
|
|
|
if !ctx.Doer.IsAdmin {
|
|
|
|
|
ctx.Error(http.StatusForbidden)
|
|
|
|
|
return
|
|
|
|
|
}
|
|
|
|
|
ctx.Data["PageIsAdmin"] = true
|
|
|
|
|
}
|
|
|
|
|
}
|
|
|
|
|
}
|
|
|
|
|
|
2023-04-28 02:08:47 +02:00
|
|
|
func ctxDataSet(args ...any) func(ctx *context.Context) {
|
|
|
|
|
return func(ctx *context.Context) {
|
|
|
|
|
for i := 0; i < len(args); i += 2 {
|
|
|
|
|
ctx.Data[args[i].(string)] = args[i+1]
|
|
|
|
|
}
|
|
|
|
|
}
|
|
|
|
|
}
|
|
|
|
|
|
2021-06-09 01:33:54 +02:00
|
|
|
// Routes returns all web routes
|
2023-06-18 09:59:09 +02:00
|
|
|
func Routes() *web.Route {
|
2021-05-04 23:48:31 +02:00
|
|
|
routes := web.NewRoute()
|
2017-04-25 09:24:51 +02:00
|
|
|
|
2023-04-27 08:06:45 +02:00
|
|
|
routes.Head("/", misc.DummyOK) // for health check - doesn't need to be passed through gzip handler
|
2023-07-21 14:14:20 +02:00
|
|
|
routes.Methods("GET, HEAD", "/assets/*", CorsHandler(), public.FileHandlerFunc())
|
2023-07-21 00:43:49 +02:00
|
|
|
routes.Methods("GET, HEAD", "/avatars/*", storageHandler(setting.Avatar.Storage, "avatars", storage.Avatars))
|
|
|
|
|
routes.Methods("GET, HEAD", "/repo-avatars/*", storageHandler(setting.RepoAvatar.Storage, "repo-avatars", storage.RepoAvatars))
|
|
|
|
|
routes.Methods("GET, HEAD", "/apple-touch-icon.png", misc.StaticRedirect("/assets/img/apple-touch-icon.png"))
|
|
|
|
|
routes.Methods("GET, HEAD", "/apple-touch-icon-precomposed.png", misc.StaticRedirect("/assets/img/apple-touch-icon.png"))
|
|
|
|
|
routes.Methods("GET, HEAD", "/favicon.ico", misc.StaticRedirect("/assets/img/favicon.png"))
|
2021-05-04 23:48:31 +02:00
|
|
|
|
2023-04-30 14:22:23 +02:00
|
|
|
_ = templates.HTMLRenderer()
|
|
|
|
|
|
2023-05-04 08:36:34 +02:00
|
|
|
var mid []any
|
2021-05-04 23:48:31 +02:00
|
|
|
|
2021-01-26 16:36:53 +01:00
|
|
|
if setting.EnableGzip {
|
|
|
|
|
h, err := gziphandler.GzipHandlerWithOpts(gziphandler.MinSize(GzipMinSize))
|
|
|
|
|
if err != nil {
|
|
|
|
|
log.Fatal("GzipHandlerWithOpts failed: %v", err)
|
|
|
|
|
}
|
2023-05-04 08:36:34 +02:00
|
|
|
mid = append(mid, h)
|
2021-01-26 16:36:53 +01:00
|
|
|
}
|
|
|
|
|
|
2021-01-27 15:56:54 +01:00
|
|
|
if setting.Service.EnableCaptcha {
|
2021-05-04 23:48:31 +02:00
|
|
|
// The captcha http.Handler should only fire on /captcha/* so we can just mount this on that url
|
2023-07-21 00:43:49 +02:00
|
|
|
routes.Methods("GET,HEAD", "/captcha/*", append(mid, captcha.Captchaer(context.GetImageCaptcha()))...)
|
2021-01-27 18:46:35 +01:00
|
|
|
}
|
|
|
|
|
|
2021-01-26 16:36:53 +01:00
|
|
|
if setting.Metrics.Enabled {
|
2023-04-27 08:06:45 +02:00
|
|
|
prometheus.MustRegister(metrics.NewCollector())
|
2023-05-04 08:36:34 +02:00
|
|
|
routes.Get("/metrics", append(mid, Metrics)...)
|
2021-01-26 16:36:53 +01:00
|
|
|
}
|
|
|
|
|
|
2023-07-21 14:14:20 +02:00
|
|
|
routes.Get("/robots.txt", append(mid, misc.RobotsTxt)...)
|
2023-04-27 08:06:45 +02:00
|
|
|
routes.Get("/ssh_info", misc.SSHInfo)
|
2022-05-04 13:56:20 +02:00
|
|
|
routes.Get("/api/healthz", healthcheck.Check)
|
|
|
|
|
|
2023-05-04 08:36:34 +02:00
|
|
|
mid = append(mid, common.Sessioner(), context.Contexter())
|
2021-05-04 23:48:31 +02:00
|
|
|
|
2021-06-09 19:53:16 +02:00
|
|
|
// Get user from session if logged in.
|
2023-09-12 08:15:16 +02:00
|
|
|
mid = append(mid, webAuth(buildAuthGroup()))
|
2021-06-09 19:53:16 +02:00
|
|
|
|
2021-05-04 23:48:31 +02:00
|
|
|
// GetHead allows a HEAD request redirect to GET if HEAD method is not defined for that route
|
2023-09-12 08:15:16 +02:00
|
|
|
mid = append(mid, chi_middleware.GetHead)
|
2021-05-04 23:48:31 +02:00
|
|
|
|
2021-01-26 16:36:53 +01:00
|
|
|
if setting.API.EnableSwagger {
|
2023-04-27 08:06:45 +02:00
|
|
|
// Note: The route is here but no in API routes because it renders a web page
|
2023-05-04 08:36:34 +02:00
|
|
|
routes.Get("/api/swagger", append(mid, misc.Swagger)...) // Render V1 by default
|
2023-02-07 11:23:49 +01:00
|
|
|
routes.Get("/api/forgejo/swagger", append(mid, misc.SwaggerForgejo)...)
|
2021-01-26 16:36:53 +01:00
|
|
|
}
|
|
|
|
|
|
2021-05-04 23:48:31 +02:00
|
|
|
// TODO: These really seem like things that could be folded into Contexter or as helper functions
|
2023-05-04 08:36:34 +02:00
|
|
|
mid = append(mid, user.GetNotificationCount)
|
|
|
|
|
mid = append(mid, repo.GetActiveStopwatch)
|
|
|
|
|
mid = append(mid, goGet)
|
2021-01-26 16:36:53 +01:00
|
|
|
|
2021-05-04 23:48:31 +02:00
|
|
|
others := web.NewRoute()
|
2023-05-04 08:36:34 +02:00
|
|
|
others.Use(mid...)
|
2023-04-27 08:06:45 +02:00
|
|
|
registerRoutes(others)
|
2021-05-04 23:48:31 +02:00
|
|
|
routes.Mount("", others)
|
|
|
|
|
return routes
|
2020-10-19 23:03:08 +02:00
|
|
|
}
|
|
|
|
|
|
2023-11-02 15:14:33 +01:00
|
|
|
var ignSignInAndCsrf = verifyAuthWithOptions(&common.VerifyOptions{DisableCSRF: true})
|
|
|
|
|
|
2023-04-27 08:06:45 +02:00
|
|
|
// registerRoutes register routes
|
|
|
|
|
func registerRoutes(m *web.Route) {
|
2023-09-12 08:15:16 +02:00
|
|
|
reqSignIn := verifyAuthWithOptions(&common.VerifyOptions{SignInRequired: true})
|
|
|
|
|
reqSignOut := verifyAuthWithOptions(&common.VerifyOptions{SignOutRequired: true})
|
2023-05-04 14:07:15 +02:00
|
|
|
// TODO: rename them to "optSignIn", which means that the "sign-in" could be optional, depends on the VerifyOptions (RequireSignInView)
|
2023-09-12 08:15:16 +02:00
|
|
|
ignSignIn := verifyAuthWithOptions(&common.VerifyOptions{SignInRequired: setting.Service.RequireSignInView})
|
|
|
|
|
ignExploreSignIn := verifyAuthWithOptions(&common.VerifyOptions{SignInRequired: setting.Service.RequireSignInView || setting.Service.Explore.RequireSigninView})
|
2023-11-02 15:14:33 +01:00
|
|
|
|
2017-04-25 09:24:51 +02:00
|
|
|
validation.AddBindingRules()
|
|
|
|
|
|
2022-02-09 21:33:36 +01:00
|
|
|
linkAccountEnabled := func(ctx *context.Context) {
|
|
|
|
|
if !setting.Service.EnableOpenIDSignIn && !setting.Service.EnableOpenIDSignUp && !setting.OAuth2.Enable {
|
|
|
|
|
ctx.Error(http.StatusForbidden)
|
|
|
|
|
return
|
|
|
|
|
}
|
|
|
|
|
}
|
|
|
|
|
|
2017-08-19 17:34:49 +02:00
|
|
|
openIDSignInEnabled := func(ctx *context.Context) {
|
|
|
|
|
if !setting.Service.EnableOpenIDSignIn {
|
2021-04-05 17:30:52 +02:00
|
|
|
ctx.Error(http.StatusForbidden)
|
2017-08-19 17:34:49 +02:00
|
|
|
return
|
|
|
|
|
}
|
|
|
|
|
}
|
|
|
|
|
|
|
|
|
|
openIDSignUpEnabled := func(ctx *context.Context) {
|
|
|
|
|
if !setting.Service.EnableOpenIDSignUp {
|
2021-04-05 17:30:52 +02:00
|
|
|
ctx.Error(http.StatusForbidden)
|
2017-08-19 17:34:49 +02:00
|
|
|
return
|
|
|
|
|
}
|
|
|
|
|
}
|
|
|
|
|
|
2019-12-15 15:20:08 +01:00
|
|
|
reqMilestonesDashboardPageEnabled := func(ctx *context.Context) {
|
|
|
|
|
if !setting.Service.ShowMilestonesDashboardPage {
|
2021-04-05 17:30:52 +02:00
|
|
|
ctx.Error(http.StatusForbidden)
|
2019-12-15 15:20:08 +01:00
|
|
|
return
|
|
|
|
|
}
|
|
|
|
|
}
|
|
|
|
|
|
2021-02-11 18:34:34 +01:00
|
|
|
// webhooksEnabled requires webhooks to be enabled by admin.
|
|
|
|
|
webhooksEnabled := func(ctx *context.Context) {
|
|
|
|
|
if setting.DisableWebhooks {
|
2021-04-05 17:30:52 +02:00
|
|
|
ctx.Error(http.StatusForbidden)
|
2021-02-11 18:34:34 +01:00
|
|
|
return
|
|
|
|
|
}
|
|
|
|
|
}
|
|
|
|
|
|
2021-06-06 01:59:27 +02:00
|
|
|
lfsServerEnabled := func(ctx *context.Context) {
|
|
|
|
|
if !setting.LFS.StartServer {
|
|
|
|
|
ctx.Error(http.StatusNotFound)
|
|
|
|
|
return
|
|
|
|
|
}
|
|
|
|
|
}
|
|
|
|
|
|
2022-05-09 20:20:21 +02:00
|
|
|
federationEnabled := func(ctx *context.Context) {
|
|
|
|
|
if !setting.Federation.Enabled {
|
|
|
|
|
ctx.Error(http.StatusNotFound)
|
|
|
|
|
return
|
|
|
|
|
}
|
|
|
|
|
}
|
|
|
|
|
|
2022-07-31 18:57:02 +02:00
|
|
|
dlSourceEnabled := func(ctx *context.Context) {
|
|
|
|
|
if setting.Repository.DisableDownloadSourceArchives {
|
|
|
|
|
ctx.Error(http.StatusNotFound)
|
|
|
|
|
return
|
|
|
|
|
}
|
|
|
|
|
}
|
|
|
|
|
|
2022-10-28 17:17:38 +02:00
|
|
|
sitemapEnabled := func(ctx *context.Context) {
|
2023-04-23 01:38:25 +02:00
|
|
|
if !setting.Other.EnableSitemap {
|
2022-10-28 17:17:38 +02:00
|
|
|
ctx.Error(http.StatusNotFound)
|
|
|
|
|
return
|
|
|
|
|
}
|
|
|
|
|
}
|
|
|
|
|
|
2022-11-20 15:08:38 +01:00
|
|
|
packagesEnabled := func(ctx *context.Context) {
|
|
|
|
|
if !setting.Packages.Enabled {
|
|
|
|
|
ctx.Error(http.StatusForbidden)
|
|
|
|
|
return
|
|
|
|
|
}
|
|
|
|
|
}
|
|
|
|
|
|
2022-11-21 06:14:58 +01:00
|
|
|
feedEnabled := func(ctx *context.Context) {
|
2023-04-23 01:38:25 +02:00
|
|
|
if !setting.Other.EnableFeed {
|
2022-11-21 06:14:58 +01:00
|
|
|
ctx.Error(http.StatusNotFound)
|
|
|
|
|
return
|
|
|
|
|
}
|
|
|
|
|
}
|
|
|
|
|
|
2023-07-29 16:13:24 +02:00
|
|
|
reqUnitAccess := func(unitType unit.Type, accessMode perm.AccessMode, ignoreGlobal bool) func(ctx *context.Context) {
|
2023-05-06 11:39:06 +02:00
|
|
|
return func(ctx *context.Context) {
|
2023-07-29 16:13:24 +02:00
|
|
|
// only check global disabled units when ignoreGlobal is false
|
|
|
|
|
if !ignoreGlobal && unitType.UnitGlobalDisabled() {
|
2023-05-06 11:39:06 +02:00
|
|
|
ctx.NotFound(unitType.String(), nil)
|
|
|
|
|
return
|
|
|
|
|
}
|
|
|
|
|
|
|
|
|
|
if ctx.ContextUser == nil {
|
|
|
|
|
ctx.NotFound(unitType.String(), nil)
|
|
|
|
|
return
|
|
|
|
|
}
|
|
|
|
|
|
|
|
|
|
if ctx.ContextUser.IsOrganization() {
|
|
|
|
|
if ctx.Org.Organization.UnitPermission(ctx, ctx.Doer, unitType) < accessMode {
|
|
|
|
|
ctx.NotFound(unitType.String(), nil)
|
|
|
|
|
return
|
|
|
|
|
}
|
|
|
|
|
}
|
|
|
|
|
}
|
|
|
|
|
}
|
|
|
|
|
|
2023-03-10 15:28:32 +01:00
|
|
|
addWebhookAddRoutes := func() {
|
2023-07-02 02:59:32 +02:00
|
|
|
m.Get("/{type}/new", repo_setting.WebhooksNew)
|
|
|
|
|
m.Post("/gitea/new", web.Bind(forms.NewWebhookForm{}), repo_setting.GiteaHooksNewPost)
|
|
|
|
|
m.Post("/gogs/new", web.Bind(forms.NewGogshookForm{}), repo_setting.GogsHooksNewPost)
|
|
|
|
|
m.Post("/slack/new", web.Bind(forms.NewSlackHookForm{}), repo_setting.SlackHooksNewPost)
|
|
|
|
|
m.Post("/discord/new", web.Bind(forms.NewDiscordHookForm{}), repo_setting.DiscordHooksNewPost)
|
|
|
|
|
m.Post("/dingtalk/new", web.Bind(forms.NewDingtalkHookForm{}), repo_setting.DingtalkHooksNewPost)
|
|
|
|
|
m.Post("/telegram/new", web.Bind(forms.NewTelegramHookForm{}), repo_setting.TelegramHooksNewPost)
|
|
|
|
|
m.Post("/matrix/new", web.Bind(forms.NewMatrixHookForm{}), repo_setting.MatrixHooksNewPost)
|
|
|
|
|
m.Post("/msteams/new", web.Bind(forms.NewMSTeamsHookForm{}), repo_setting.MSTeamsHooksNewPost)
|
|
|
|
|
m.Post("/feishu/new", web.Bind(forms.NewFeishuHookForm{}), repo_setting.FeishuHooksNewPost)
|
|
|
|
|
m.Post("/wechatwork/new", web.Bind(forms.NewWechatWorkHookForm{}), repo_setting.WechatworkHooksNewPost)
|
|
|
|
|
m.Post("/packagist/new", web.Bind(forms.NewPackagistHookForm{}), repo_setting.PackagistHooksNewPost)
|
2023-03-10 15:28:32 +01:00
|
|
|
}
|
|
|
|
|
|
|
|
|
|
addWebhookEditRoutes := func() {
|
2023-07-02 02:59:32 +02:00
|
|
|
m.Post("/gitea/{id}", web.Bind(forms.NewWebhookForm{}), repo_setting.GiteaHooksEditPost)
|
|
|
|
|
m.Post("/gogs/{id}", web.Bind(forms.NewGogshookForm{}), repo_setting.GogsHooksEditPost)
|
|
|
|
|
m.Post("/slack/{id}", web.Bind(forms.NewSlackHookForm{}), repo_setting.SlackHooksEditPost)
|
|
|
|
|
m.Post("/discord/{id}", web.Bind(forms.NewDiscordHookForm{}), repo_setting.DiscordHooksEditPost)
|
|
|
|
|
m.Post("/dingtalk/{id}", web.Bind(forms.NewDingtalkHookForm{}), repo_setting.DingtalkHooksEditPost)
|
|
|
|
|
m.Post("/telegram/{id}", web.Bind(forms.NewTelegramHookForm{}), repo_setting.TelegramHooksEditPost)
|
|
|
|
|
m.Post("/matrix/{id}", web.Bind(forms.NewMatrixHookForm{}), repo_setting.MatrixHooksEditPost)
|
|
|
|
|
m.Post("/msteams/{id}", web.Bind(forms.NewMSTeamsHookForm{}), repo_setting.MSTeamsHooksEditPost)
|
|
|
|
|
m.Post("/feishu/{id}", web.Bind(forms.NewFeishuHookForm{}), repo_setting.FeishuHooksEditPost)
|
|
|
|
|
m.Post("/wechatwork/{id}", web.Bind(forms.NewWechatWorkHookForm{}), repo_setting.WechatworkHooksEditPost)
|
|
|
|
|
m.Post("/packagist/{id}", web.Bind(forms.NewPackagistHookForm{}), repo_setting.PackagistHooksEditPost)
|
2023-03-10 15:28:32 +01:00
|
|
|
}
|
|
|
|
|
|
2023-06-21 00:54:15 +02:00
|
|
|
addSettingVariablesRoutes := func() {
|
|
|
|
|
m.Group("/variables", func() {
|
|
|
|
|
m.Get("", repo_setting.Variables)
|
|
|
|
|
m.Post("/new", web.Bind(forms.EditVariableForm{}), repo_setting.VariableCreate)
|
|
|
|
|
m.Post("/{variable_id}/edit", web.Bind(forms.EditVariableForm{}), repo_setting.VariableUpdate)
|
|
|
|
|
m.Post("/{variable_id}/delete", repo_setting.VariableDelete)
|
|
|
|
|
})
|
|
|
|
|
}
|
|
|
|
|
|
2023-04-28 02:08:47 +02:00
|
|
|
addSettingsSecretsRoutes := func() {
|
|
|
|
|
m.Group("/secrets", func() {
|
|
|
|
|
m.Get("", repo_setting.Secrets)
|
|
|
|
|
m.Post("", web.Bind(forms.AddSecretForm{}), repo_setting.SecretsPost)
|
|
|
|
|
m.Post("/delete", repo_setting.SecretsDelete)
|
|
|
|
|
})
|
|
|
|
|
}
|
|
|
|
|
|
|
|
|
|
addSettingsRunnersRoutes := func() {
|
|
|
|
|
m.Group("/runners", func() {
|
|
|
|
|
m.Get("", repo_setting.Runners)
|
|
|
|
|
m.Combo("/{runnerid}").Get(repo_setting.RunnersEdit).
|
|
|
|
|
Post(web.Bind(forms.EditRunnerForm{}), repo_setting.RunnersEditPost)
|
|
|
|
|
m.Post("/{runnerid}/delete", repo_setting.RunnerDeletePost)
|
|
|
|
|
m.Get("/reset_registration_token", repo_setting.ResetRunnerRegistrationToken)
|
|
|
|
|
})
|
|
|
|
|
}
|
|
|
|
|
|
2021-01-30 09:55:53 +01:00
|
|
|
// FIXME: not all routes need go through same middleware.
|
2017-04-25 09:24:51 +02:00
|
|
|
// Especially some AJAX requests, we can reduce middleware number to improve performance.
|
2023-07-21 14:14:20 +02:00
|
|
|
|
2021-06-09 01:33:54 +02:00
|
|
|
m.Get("/", Home)
|
2022-10-28 17:17:38 +02:00
|
|
|
m.Get("/sitemap.xml", sitemapEnabled, ignExploreSignIn, HomeSitemap)
|
2021-11-26 15:55:11 +01:00
|
|
|
m.Group("/.well-known", func() {
|
2022-01-02 14:12:35 +01:00
|
|
|
m.Get("/openid-configuration", auth.OIDCWellKnown)
|
2022-05-09 20:20:21 +02:00
|
|
|
m.Group("", func() {
|
2021-11-26 15:55:11 +01:00
|
|
|
m.Get("/nodeinfo", NodeInfoLinks)
|
2022-05-09 20:20:21 +02:00
|
|
|
m.Get("/webfinger", WebfingerQuery)
|
|
|
|
|
}, federationEnabled)
|
2023-04-27 08:06:45 +02:00
|
|
|
m.Get("/change-password", func(ctx *context.Context) {
|
|
|
|
|
ctx.Redirect(setting.AppSubURL + "/user/settings/account")
|
2021-11-26 15:55:11 +01:00
|
|
|
})
|
2023-07-21 14:14:20 +02:00
|
|
|
m.Any("/*", CorsHandler(), public.FileHandlerFunc())
|
|
|
|
|
}, CorsHandler())
|
2021-11-26 15:55:11 +01:00
|
|
|
|
2017-04-25 09:24:51 +02:00
|
|
|
m.Group("/explore", func() {
|
|
|
|
|
m.Get("", func(ctx *context.Context) {
|
|
|
|
|
ctx.Redirect(setting.AppSubURL + "/explore/repos")
|
|
|
|
|
})
|
2021-06-09 01:33:54 +02:00
|
|
|
m.Get("/repos", explore.Repos)
|
2022-10-28 17:17:38 +02:00
|
|
|
m.Get("/repos/sitemap-{idx}.xml", sitemapEnabled, explore.Repos)
|
2021-06-09 01:33:54 +02:00
|
|
|
m.Get("/users", explore.Users)
|
2022-10-28 17:17:38 +02:00
|
|
|
m.Get("/users/sitemap-{idx}.xml", sitemapEnabled, explore.Users)
|
2021-06-09 01:33:54 +02:00
|
|
|
m.Get("/organizations", explore.Organizations)
|
2023-06-09 21:02:33 +02:00
|
|
|
m.Get("/code", func(ctx *context.Context) {
|
|
|
|
|
if unit.TypeCode.UnitGlobalDisabled() {
|
|
|
|
|
ctx.NotFound(unit.TypeCode.String(), nil)
|
|
|
|
|
return
|
|
|
|
|
}
|
|
|
|
|
}, explore.Code)
|
2022-04-07 20:59:56 +02:00
|
|
|
m.Get("/topics/search", explore.TopicSearch)
|
2021-03-11 14:40:54 +01:00
|
|
|
}, ignExploreSignIn)
|
2022-04-07 20:59:56 +02:00
|
|
|
m.Group("/issues", func() {
|
|
|
|
|
m.Get("", user.Issues)
|
|
|
|
|
m.Get("/search", repo.SearchIssues)
|
|
|
|
|
}, reqSignIn)
|
|
|
|
|
|
2021-01-13 05:19:17 +01:00
|
|
|
m.Get("/pulls", reqSignIn, user.Pulls)
|
2019-12-15 15:20:08 +01:00
|
|
|
m.Get("/milestones", reqSignIn, reqMilestonesDashboardPageEnabled, user.Milestones)
|
2017-04-25 09:24:51 +02:00
|
|
|
|
|
|
|
|
// ***** START: User *****
|
2023-07-27 07:08:51 +02:00
|
|
|
// "user/login" doesn't need signOut, then logged-in users can still access this route for redirection purposes by "/user/login?redirec_to=..."
|
|
|
|
|
m.Get("/user/login", auth.SignIn)
|
2017-04-25 09:24:51 +02:00
|
|
|
m.Group("/user", func() {
|
2022-12-12 09:09:26 +01:00
|
|
|
m.Post("/login", web.Bind(forms.SignInForm{}), auth.SignInPost)
|
2017-08-19 17:34:49 +02:00
|
|
|
m.Group("", func() {
|
2017-04-25 09:24:51 +02:00
|
|
|
m.Combo("/login/openid").
|
2022-01-02 14:12:35 +01:00
|
|
|
Get(auth.SignInOpenID).
|
2022-12-12 09:09:26 +01:00
|
|
|
Post(web.Bind(forms.SignInOpenIDForm{}), auth.SignInOpenIDPost)
|
2017-08-19 17:34:49 +02:00
|
|
|
}, openIDSignInEnabled)
|
|
|
|
|
m.Group("/openid", func() {
|
|
|
|
|
m.Combo("/connect").
|
2022-01-02 14:12:35 +01:00
|
|
|
Get(auth.ConnectOpenID).
|
2022-12-12 09:09:26 +01:00
|
|
|
Post(web.Bind(forms.ConnectOpenIDForm{}), auth.ConnectOpenIDPost)
|
2017-08-19 17:34:49 +02:00
|
|
|
m.Group("/register", func() {
|
|
|
|
|
m.Combo("").
|
2022-01-02 14:12:35 +01:00
|
|
|
Get(auth.RegisterOpenID, openIDSignUpEnabled).
|
2022-12-12 09:09:26 +01:00
|
|
|
Post(web.Bind(forms.SignUpOpenIDForm{}), auth.RegisterOpenIDPost)
|
2017-08-19 17:34:49 +02:00
|
|
|
}, openIDSignUpEnabled)
|
|
|
|
|
}, openIDSignInEnabled)
|
2022-01-02 14:12:35 +01:00
|
|
|
m.Get("/sign_up", auth.SignUp)
|
2022-12-12 09:09:26 +01:00
|
|
|
m.Post("/sign_up", web.Bind(forms.RegisterForm{}), auth.SignUpPost)
|
2022-02-09 21:33:36 +01:00
|
|
|
m.Get("/link_account", linkAccountEnabled, auth.LinkAccount)
|
2022-12-12 09:09:26 +01:00
|
|
|
m.Post("/link_account_signin", linkAccountEnabled, web.Bind(forms.SignInForm{}), auth.LinkAccountPostSignIn)
|
|
|
|
|
m.Post("/link_account_signup", linkAccountEnabled, web.Bind(forms.RegisterForm{}), auth.LinkAccountPostRegister)
|
2017-04-25 09:24:51 +02:00
|
|
|
m.Group("/two_factor", func() {
|
2022-01-02 14:12:35 +01:00
|
|
|
m.Get("", auth.TwoFactor)
|
2022-12-12 09:09:26 +01:00
|
|
|
m.Post("", web.Bind(forms.TwoFactorAuthForm{}), auth.TwoFactorPost)
|
2022-01-02 14:12:35 +01:00
|
|
|
m.Get("/scratch", auth.TwoFactorScratch)
|
2022-12-12 09:09:26 +01:00
|
|
|
m.Post("/scratch", web.Bind(forms.TwoFactorScratchAuthForm{}), auth.TwoFactorScratchPost)
|
2017-04-25 09:24:51 +02:00
|
|
|
})
|
2022-01-14 16:03:31 +01:00
|
|
|
m.Group("/webauthn", func() {
|
|
|
|
|
m.Get("", auth.WebAuthn)
|
|
|
|
|
m.Get("/assertion", auth.WebAuthnLoginAssertion)
|
|
|
|
|
m.Post("/assertion", auth.WebAuthnLoginAssertionPost)
|
2018-05-19 16:12:37 +02:00
|
|
|
})
|
2017-04-25 09:24:51 +02:00
|
|
|
}, reqSignOut)
|
|
|
|
|
|
2022-01-20 12:41:25 +01:00
|
|
|
m.Any("/user/events", routing.MarkLongPolling, events.Events)
|
2020-05-07 23:49:00 +02:00
|
|
|
|
2019-03-08 17:42:50 +01:00
|
|
|
m.Group("/login/oauth", func() {
|
2022-12-12 09:09:26 +01:00
|
|
|
m.Get("/authorize", web.Bind(forms.AuthorizationForm{}), auth.AuthorizeOAuth)
|
|
|
|
|
m.Post("/grant", web.Bind(forms.GrantApplicationForm{}), auth.GrantApplicationOAuth)
|
2019-03-08 17:42:50 +01:00
|
|
|
// TODO manage redirection
|
2022-12-12 09:09:26 +01:00
|
|
|
m.Post("/authorize", web.Bind(forms.AuthorizationForm{}), auth.AuthorizeOAuth)
|
2019-03-08 17:42:50 +01:00
|
|
|
}, ignSignInAndCsrf, reqSignIn)
|
2022-01-02 14:12:35 +01:00
|
|
|
m.Get("/login/oauth/userinfo", ignSignInAndCsrf, auth.InfoOAuth)
|
2022-12-12 09:09:26 +01:00
|
|
|
m.Post("/login/oauth/access_token", CorsHandler(), web.Bind(forms.AccessTokenForm{}), ignSignInAndCsrf, auth.AccessTokenOAuth)
|
2022-01-02 14:12:35 +01:00
|
|
|
m.Get("/login/oauth/keys", ignSignInAndCsrf, auth.OIDCKeys)
|
2022-12-12 09:09:26 +01:00
|
|
|
m.Post("/login/oauth/introspect", CorsHandler(), web.Bind(forms.IntrospectTokenForm{}), ignSignInAndCsrf, auth.IntrospectOAuth)
|
2019-03-08 17:42:50 +01:00
|
|
|
|
2017-04-25 09:24:51 +02:00
|
|
|
m.Group("/user/settings", func() {
|
2022-01-02 14:12:35 +01:00
|
|
|
m.Get("", user_setting.Profile)
|
2022-12-12 09:09:26 +01:00
|
|
|
m.Post("", web.Bind(forms.UpdateProfileForm{}), user_setting.ProfilePost)
|
2022-01-02 14:12:35 +01:00
|
|
|
m.Get("/change_password", auth.MustChangePassword)
|
2022-12-12 09:09:26 +01:00
|
|
|
m.Post("/change_password", web.Bind(forms.MustChangePasswordForm{}), auth.MustChangePasswordPost)
|
|
|
|
|
m.Post("/avatar", web.Bind(forms.AvatarForm{}), user_setting.AvatarPost)
|
2022-01-02 14:12:35 +01:00
|
|
|
m.Post("/avatar/delete", user_setting.DeleteAvatar)
|
2018-05-15 12:07:32 +02:00
|
|
|
m.Group("/account", func() {
|
2022-12-12 09:09:26 +01:00
|
|
|
m.Combo("").Get(user_setting.Account).Post(web.Bind(forms.ChangePasswordForm{}), user_setting.AccountPost)
|
|
|
|
|
m.Post("/email", web.Bind(forms.AddEmailForm{}), user_setting.EmailPost)
|
2022-01-02 14:12:35 +01:00
|
|
|
m.Post("/email/delete", user_setting.DeleteEmail)
|
|
|
|
|
m.Post("/delete", user_setting.DeleteAccount)
|
2021-10-27 17:40:08 +02:00
|
|
|
})
|
|
|
|
|
m.Group("/appearance", func() {
|
2022-01-02 14:12:35 +01:00
|
|
|
m.Get("", user_setting.Appearance)
|
2022-12-12 09:09:26 +01:00
|
|
|
m.Post("/language", web.Bind(forms.UpdateLanguageForm{}), user_setting.UpdateUserLang)
|
2022-01-21 18:59:26 +01:00
|
|
|
m.Post("/hidden_comments", user_setting.UpdateUserHiddenComments)
|
2022-12-12 09:09:26 +01:00
|
|
|
m.Post("/theme", web.Bind(forms.UpdateThemeForm{}), user_setting.UpdateUIThemePost)
|
2018-05-15 12:07:32 +02:00
|
|
|
})
|
|
|
|
|
m.Group("/security", func() {
|
2022-01-02 14:12:35 +01:00
|
|
|
m.Get("", security.Security)
|
2018-05-15 12:07:32 +02:00
|
|
|
m.Group("/two_factor", func() {
|
2022-01-02 14:12:35 +01:00
|
|
|
m.Post("/regenerate_scratch", security.RegenerateScratchTwoFactor)
|
|
|
|
|
m.Post("/disable", security.DisableTwoFactor)
|
|
|
|
|
m.Get("/enroll", security.EnrollTwoFactor)
|
2022-12-12 09:09:26 +01:00
|
|
|
m.Post("/enroll", web.Bind(forms.TwoFactorAuthForm{}), security.EnrollTwoFactorPost)
|
2018-05-15 12:07:32 +02:00
|
|
|
})
|
2022-01-14 16:03:31 +01:00
|
|
|
m.Group("/webauthn", func() {
|
2022-12-12 09:09:26 +01:00
|
|
|
m.Post("/request_register", web.Bind(forms.WebauthnRegistrationForm{}), security.WebAuthnRegister)
|
2022-01-14 16:03:31 +01:00
|
|
|
m.Post("/register", security.WebauthnRegisterPost)
|
2022-12-12 09:09:26 +01:00
|
|
|
m.Post("/delete", web.Bind(forms.WebauthnDeleteForm{}), security.WebauthnDelete)
|
2018-05-19 16:12:37 +02:00
|
|
|
})
|
2018-05-15 12:07:32 +02:00
|
|
|
m.Group("/openid", func() {
|
2022-12-12 09:09:26 +01:00
|
|
|
m.Post("", web.Bind(forms.AddOpenIDForm{}), security.OpenIDPost)
|
2022-01-02 14:12:35 +01:00
|
|
|
m.Post("/delete", security.DeleteOpenID)
|
|
|
|
|
m.Post("/toggle_visibility", security.ToggleOpenIDVisibility)
|
2018-05-15 12:07:32 +02:00
|
|
|
}, openIDSignInEnabled)
|
2022-02-09 21:33:36 +01:00
|
|
|
m.Post("/account_link", linkAccountEnabled, security.DeleteAccountLink)
|
2018-05-15 12:07:32 +02:00
|
|
|
})
|
2019-03-08 17:42:50 +01:00
|
|
|
m.Group("/applications/oauth2", func() {
|
2022-01-02 14:12:35 +01:00
|
|
|
m.Get("/{id}", user_setting.OAuth2ApplicationShow)
|
2022-12-12 09:09:26 +01:00
|
|
|
m.Post("/{id}", web.Bind(forms.EditOAuth2ApplicationForm{}), user_setting.OAuthApplicationsEdit)
|
2022-01-02 14:12:35 +01:00
|
|
|
m.Post("/{id}/regenerate_secret", user_setting.OAuthApplicationsRegenerateSecret)
|
2022-12-12 09:09:26 +01:00
|
|
|
m.Post("", web.Bind(forms.EditOAuth2ApplicationForm{}), user_setting.OAuthApplicationsPost)
|
2022-10-09 14:07:41 +02:00
|
|
|
m.Post("/{id}/delete", user_setting.DeleteOAuth2Application)
|
|
|
|
|
m.Post("/{id}/revoke/{grantId}", user_setting.RevokeOAuth2Grant)
|
2019-03-08 17:42:50 +01:00
|
|
|
})
|
2022-01-02 14:12:35 +01:00
|
|
|
m.Combo("/applications").Get(user_setting.Applications).
|
2022-12-12 09:09:26 +01:00
|
|
|
Post(web.Bind(forms.NewAccessTokenForm{}), user_setting.ApplicationsPost)
|
2022-01-02 14:12:35 +01:00
|
|
|
m.Post("/applications/delete", user_setting.DeleteApplication)
|
|
|
|
|
m.Combo("/keys").Get(user_setting.Keys).
|
2022-12-12 09:09:26 +01:00
|
|
|
Post(web.Bind(forms.AddKeyForm{}), user_setting.KeysPost)
|
2022-01-02 14:12:35 +01:00
|
|
|
m.Post("/keys/delete", user_setting.DeleteKey)
|
2022-11-20 15:08:38 +01:00
|
|
|
m.Group("/packages", func() {
|
|
|
|
|
m.Get("", user_setting.Packages)
|
|
|
|
|
m.Group("/rules", func() {
|
|
|
|
|
m.Group("/add", func() {
|
|
|
|
|
m.Get("", user_setting.PackagesRuleAdd)
|
2022-12-12 09:09:26 +01:00
|
|
|
m.Post("", web.Bind(forms.PackageCleanupRuleForm{}), user_setting.PackagesRuleAddPost)
|
2022-11-20 15:08:38 +01:00
|
|
|
})
|
|
|
|
|
m.Group("/{id}", func() {
|
|
|
|
|
m.Get("", user_setting.PackagesRuleEdit)
|
2022-12-12 09:09:26 +01:00
|
|
|
m.Post("", web.Bind(forms.PackageCleanupRuleForm{}), user_setting.PackagesRuleEditPost)
|
2022-11-20 15:08:38 +01:00
|
|
|
m.Get("/preview", user_setting.PackagesRulePreview)
|
|
|
|
|
})
|
|
|
|
|
})
|
2023-02-05 11:12:31 +01:00
|
|
|
m.Group("/cargo", func() {
|
|
|
|
|
m.Post("/initialize", user_setting.InitializeCargoIndex)
|
|
|
|
|
m.Post("/rebuild", user_setting.RebuildCargoIndex)
|
|
|
|
|
})
|
2023-02-06 02:49:21 +01:00
|
|
|
m.Post("/chef/regenerate_keypair", user_setting.RegenerateChefKeyPair)
|
2022-11-20 15:08:38 +01:00
|
|
|
}, packagesEnabled)
|
2023-04-28 02:08:47 +02:00
|
|
|
|
|
|
|
|
m.Group("/actions", func() {
|
|
|
|
|
m.Get("", user_setting.RedirectToDefaultSetting)
|
2023-05-31 03:39:54 +02:00
|
|
|
addSettingsRunnersRoutes()
|
2023-04-28 02:08:47 +02:00
|
|
|
addSettingsSecretsRoutes()
|
2023-06-21 00:54:15 +02:00
|
|
|
addSettingVariablesRoutes()
|
2023-04-28 02:08:47 +02:00
|
|
|
}, actions.MustEnableActions)
|
|
|
|
|
|
2022-01-02 14:12:35 +01:00
|
|
|
m.Get("/organization", user_setting.Organization)
|
|
|
|
|
m.Get("/repos", user_setting.Repos)
|
|
|
|
|
m.Post("/repos/unadopted", user_setting.AdoptOrDeleteRepository)
|
2023-03-10 15:28:32 +01:00
|
|
|
|
|
|
|
|
m.Group("/hooks", func() {
|
|
|
|
|
m.Get("", user_setting.Webhooks)
|
|
|
|
|
m.Post("/delete", user_setting.DeleteWebhook)
|
|
|
|
|
addWebhookAddRoutes()
|
|
|
|
|
m.Group("/{id}", func() {
|
2023-07-02 02:59:32 +02:00
|
|
|
m.Get("", repo_setting.WebHooksEdit)
|
|
|
|
|
m.Post("/replay/{uuid}", repo_setting.ReplayWebhook)
|
2023-03-10 15:28:32 +01:00
|
|
|
})
|
|
|
|
|
addWebhookEditRoutes()
|
2023-04-28 02:08:47 +02:00
|
|
|
}, webhooksEnabled)
|
|
|
|
|
}, reqSignIn, ctxDataSet("PageIsUserSettings", true, "AllThemes", setting.UI.Themes, "EnablePackages", setting.Packages.Enabled))
|
2017-04-25 09:24:51 +02:00
|
|
|
|
|
|
|
|
m.Group("/user", func() {
|
2022-04-12 04:02:58 +02:00
|
|
|
m.Get("/activate", auth.Activate)
|
|
|
|
|
m.Post("/activate", auth.ActivatePost)
|
2022-01-02 14:12:35 +01:00
|
|
|
m.Any("/activate_email", auth.ActivateEmail)
|
Avatar refactor, move avatar code from `models` to `models.avatars`, remove duplicated code (#17123)
Why this refactor
The goal is to move most files from `models` package to `models.xxx` package. Many models depend on avatar model, so just move this first.
And the existing logic is not clear, there are too many function like `AvatarLink`, `RelAvatarLink`, `SizedRelAvatarLink`, `SizedAvatarLink`, `MakeFinalAvatarURL`, `HashedAvatarLink`, etc. This refactor make everything clear:
* user.AvatarLink()
* user.AvatarLinkWithSize(size)
* avatars.GenerateEmailAvatarFastLink(email, size)
* avatars.GenerateEmailAvatarFinalLink(email, size)
And many duplicated code are deleted in route handler, the handler and the model share the same avatar logic now.
2021-10-06 01:25:46 +02:00
|
|
|
m.Get("/avatar/{username}/{size}", user.AvatarByUserName)
|
2022-01-02 14:12:35 +01:00
|
|
|
m.Get("/recover_account", auth.ResetPasswd)
|
|
|
|
|
m.Post("/recover_account", auth.ResetPasswdPost)
|
|
|
|
|
m.Get("/forgot_password", auth.ForgotPasswd)
|
|
|
|
|
m.Post("/forgot_password", auth.ForgotPasswdPost)
|
|
|
|
|
m.Post("/logout", auth.SignOut)
|
2022-04-12 04:02:58 +02:00
|
|
|
m.Get("/task/{task}", reqSignIn, user.TaskStatus)
|
|
|
|
|
m.Get("/stopwatches", reqSignIn, user.GetStopwatches)
|
|
|
|
|
m.Get("/search", ignExploreSignIn, user.Search)
|
2022-05-29 02:03:17 +02:00
|
|
|
m.Group("/oauth2", func() {
|
|
|
|
|
m.Get("/{provider}", auth.SignInOAuth)
|
|
|
|
|
m.Get("/{provider}/callback", auth.SignInOAuthCallback)
|
|
|
|
|
})
|
2017-04-25 09:24:51 +02:00
|
|
|
})
|
|
|
|
|
// ***** END: User *****
|
|
|
|
|
|
2021-01-26 16:36:53 +01:00
|
|
|
m.Get("/avatar/{hash}", user.AvatarByEmailHash)
|
2020-03-27 13:34:39 +01:00
|
|
|
|
2023-09-12 08:15:16 +02:00
|
|
|
adminReq := verifyAuthWithOptions(&common.VerifyOptions{SignInRequired: true, AdminRequired: true})
|
2017-04-25 09:24:51 +02:00
|
|
|
|
|
|
|
|
// ***** START: Admin *****
|
|
|
|
|
m.Group("/admin", func() {
|
2023-06-03 16:03:41 +02:00
|
|
|
m.Get("", admin.Dashboard)
|
|
|
|
|
m.Post("", web.Bind(forms.AdminDashboardForm{}), admin.DashboardPost)
|
2022-10-17 01:29:26 +02:00
|
|
|
|
|
|
|
|
m.Group("/config", func() {
|
|
|
|
|
m.Get("", admin.Config)
|
|
|
|
|
m.Post("", admin.ChangeConfig)
|
|
|
|
|
m.Post("/test_mail", admin.SendTestMail)
|
|
|
|
|
})
|
|
|
|
|
|
2020-01-07 12:23:09 +01:00
|
|
|
m.Group("/monitor", func() {
|
2023-06-03 16:03:41 +02:00
|
|
|
m.Get("/stats", admin.MonitorStats)
|

Improve queue & process & stacktrace (#24636)
Although some features are mixed together in this PR, this PR is not
that large, and these features are all related.
Actually there are more than 70 lines are for a toy "test queue", so
this PR is quite simple.
Major features:
1. Allow site admin to clear a queue (remove all items in a queue)
* Because there is no transaction, the "unique queue" could be corrupted
in rare cases, that's unfixable.
* eg: the item is in the "set" but not in the "list", so the item would
never be able to be pushed into the queue.
* Now site admin could simply clear the queue, then everything becomes
correct, the lost items could be re-pushed into queue by future
operations.
3. Split the "admin/monitor" to separate pages
4. Allow to download diagnosis report
* In history, there were many users reporting that Gitea queue gets
stuck, or Gitea's CPU is 100%
* With diagnosis report, maintainers could know what happens clearly
The diagnosis report sample:
[gitea-diagnosis-20230510-192913.zip](https://github.com/go-gitea/gitea/files/11441346/gitea-diagnosis-20230510-192913.zip)
, use "go tool pprof profile.dat" to view the report.
Screenshots:

---------
Co-authored-by: Jason Song <i@wolfogre.com>
Co-authored-by: Giteabot <teabot@gitea.io>
2023-05-11 09:45:47 +02:00
|
|
|
m.Get("/cron", admin.CronTasks)
|
|
|
|
|
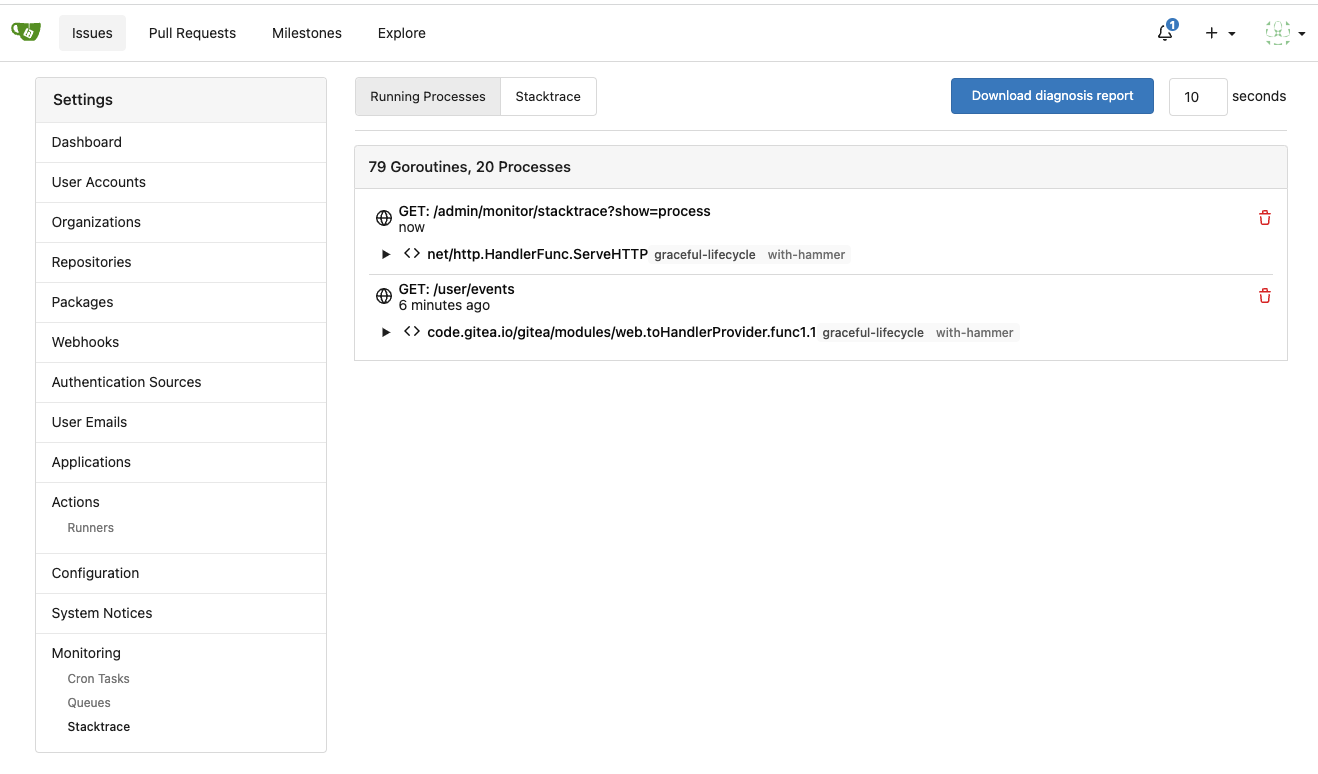
m.Get("/stacktrace", admin.Stacktrace)
|
|
|
|
|
m.Post("/stacktrace/cancel/{pid}", admin.StacktraceCancel)
|
|
|
|
|
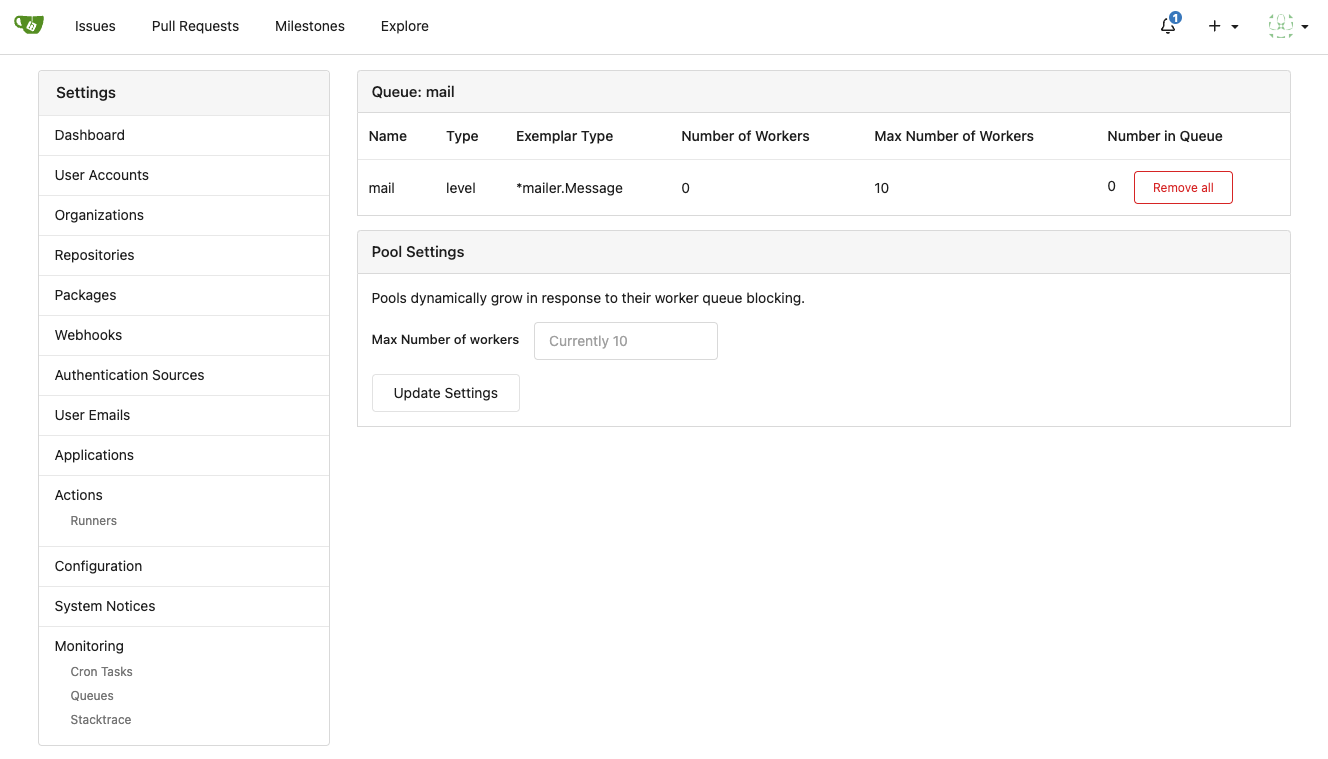
m.Get("/queue", admin.Queues)
|
2021-01-26 16:36:53 +01:00
|
|
|
m.Group("/queue/{qid}", func() {
|

Improve queue & process & stacktrace (#24636)
Although some features are mixed together in this PR, this PR is not
that large, and these features are all related.
Actually there are more than 70 lines are for a toy "test queue", so
this PR is quite simple.
Major features:
1. Allow site admin to clear a queue (remove all items in a queue)
* Because there is no transaction, the "unique queue" could be corrupted
in rare cases, that's unfixable.
* eg: the item is in the "set" but not in the "list", so the item would
never be able to be pushed into the queue.
* Now site admin could simply clear the queue, then everything becomes
correct, the lost items could be re-pushed into queue by future
operations.
3. Split the "admin/monitor" to separate pages
4. Allow to download diagnosis report
* In history, there were many users reporting that Gitea queue gets
stuck, or Gitea's CPU is 100%
* With diagnosis report, maintainers could know what happens clearly
The diagnosis report sample:
[gitea-diagnosis-20230510-192913.zip](https://github.com/go-gitea/gitea/files/11441346/gitea-diagnosis-20230510-192913.zip)
, use "go tool pprof profile.dat" to view the report.
Screenshots:



---------
Co-authored-by: Jason Song <i@wolfogre.com>
Co-authored-by: Giteabot <teabot@gitea.io>
2023-05-11 09:45:47 +02:00
|
|
|
m.Get("", admin.QueueManage)
|

Rewrite queue (#24505)
# ⚠️ Breaking
Many deprecated queue config options are removed (actually, they should
have been removed in 1.18/1.19).
If you see the fatal message when starting Gitea: "Please update your
app.ini to remove deprecated config options", please follow the error
messages to remove these options from your app.ini.
Example:
```
2023/05/06 19:39:22 [E] Removed queue option: `[indexer].ISSUE_INDEXER_QUEUE_TYPE`. Use new options in `[queue.issue_indexer]`
2023/05/06 19:39:22 [E] Removed queue option: `[indexer].UPDATE_BUFFER_LEN`. Use new options in `[queue.issue_indexer]`
2023/05/06 19:39:22 [F] Please update your app.ini to remove deprecated config options
```
Many options in `[queue]` are are dropped, including:
`WRAP_IF_NECESSARY`, `MAX_ATTEMPTS`, `TIMEOUT`, `WORKERS`,
`BLOCK_TIMEOUT`, `BOOST_TIMEOUT`, `BOOST_WORKERS`, they can be removed
from app.ini.
# The problem
The old queue package has some legacy problems:
* complexity: I doubt few people could tell how it works.
* maintainability: Too many channels and mutex/cond are mixed together,
too many different structs/interfaces depends each other.
* stability: due to the complexity & maintainability, sometimes there
are strange bugs and difficult to debug, and some code doesn't have test
(indeed some code is difficult to test because a lot of things are mixed
together).
* general applicability: although it is called "queue", its behavior is
not a well-known queue.
* scalability: it doesn't seem easy to make it work with a cluster
without breaking its behaviors.
It came from some very old code to "avoid breaking", however, its
technical debt is too heavy now. It's a good time to introduce a better
"queue" package.
# The new queue package
It keeps using old config and concept as much as possible.
* It only contains two major kinds of concepts:
* The "base queue": channel, levelqueue, redis
* They have the same abstraction, the same interface, and they are
tested by the same testing code.
* The "WokerPoolQueue", it uses the "base queue" to provide "worker
pool" function, calls the "handler" to process the data in the base
queue.
* The new code doesn't do "PushBack"
* Think about a queue with many workers, the "PushBack" can't guarantee
the order for re-queued unhandled items, so in new code it just does
"normal push"
* The new code doesn't do "pause/resume"
* The "pause/resume" was designed to handle some handler's failure: eg:
document indexer (elasticsearch) is down
* If a queue is paused for long time, either the producers blocks or the
new items are dropped.
* The new code doesn't do such "pause/resume" trick, it's not a common
queue's behavior and it doesn't help much.
* If there are unhandled items, the "push" function just blocks for a
few seconds and then re-queue them and retry.
* The new code doesn't do "worker booster"
* Gitea's queue's handlers are light functions, the cost is only the
go-routine, so it doesn't make sense to "boost" them.
* The new code only use "max worker number" to limit the concurrent
workers.
* The new "Push" never blocks forever
* Instead of creating more and more blocking goroutines, return an error
is more friendly to the server and to the end user.
There are more details in code comments: eg: the "Flush" problem, the
strange "code.index" hanging problem, the "immediate" queue problem.
Almost ready for review.
TODO:
* [x] add some necessary comments during review
* [x] add some more tests if necessary
* [x] update documents and config options
* [x] test max worker / active worker
* [x] re-run the CI tasks to see whether any test is flaky
* [x] improve the `handleOldLengthConfiguration` to provide more
friendly messages
* [x] fine tune default config values (eg: length?)
## Code coverage:

2023-05-08 13:49:59 +02:00
|
|
|
m.Post("/set", admin.QueueSet)
|

Improve queue & process & stacktrace (#24636)
Although some features are mixed together in this PR, this PR is not
that large, and these features are all related.
Actually there are more than 70 lines are for a toy "test queue", so
this PR is quite simple.
Major features:
1. Allow site admin to clear a queue (remove all items in a queue)
* Because there is no transaction, the "unique queue" could be corrupted
in rare cases, that's unfixable.
* eg: the item is in the "set" but not in the "list", so the item would
never be able to be pushed into the queue.
* Now site admin could simply clear the queue, then everything becomes
correct, the lost items could be re-pushed into queue by future
operations.
3. Split the "admin/monitor" to separate pages
4. Allow to download diagnosis report
* In history, there were many users reporting that Gitea queue gets
stuck, or Gitea's CPU is 100%
* With diagnosis report, maintainers could know what happens clearly
The diagnosis report sample:
[gitea-diagnosis-20230510-192913.zip](https://github.com/go-gitea/gitea/files/11441346/gitea-diagnosis-20230510-192913.zip)
, use "go tool pprof profile.dat" to view the report.
Screenshots:



---------
Co-authored-by: Jason Song <i@wolfogre.com>
Co-authored-by: Giteabot <teabot@gitea.io>
2023-05-11 09:45:47 +02:00
|
|
|
m.Post("/remove-all-items", admin.QueueRemoveAllItems)
|
2020-01-07 12:23:09 +01:00
|
|
|
})
|

Improve queue & process & stacktrace (#24636)
Although some features are mixed together in this PR, this PR is not
that large, and these features are all related.
Actually there are more than 70 lines are for a toy "test queue", so
this PR is quite simple.
Major features:
1. Allow site admin to clear a queue (remove all items in a queue)
* Because there is no transaction, the "unique queue" could be corrupted
in rare cases, that's unfixable.
* eg: the item is in the "set" but not in the "list", so the item would
never be able to be pushed into the queue.
* Now site admin could simply clear the queue, then everything becomes
correct, the lost items could be re-pushed into queue by future
operations.
3. Split the "admin/monitor" to separate pages
4. Allow to download diagnosis report
* In history, there were many users reporting that Gitea queue gets
stuck, or Gitea's CPU is 100%
* With diagnosis report, maintainers could know what happens clearly
The diagnosis report sample:
[gitea-diagnosis-20230510-192913.zip](https://github.com/go-gitea/gitea/files/11441346/gitea-diagnosis-20230510-192913.zip)
, use "go tool pprof profile.dat" to view the report.
Screenshots:



---------
Co-authored-by: Jason Song <i@wolfogre.com>
Co-authored-by: Giteabot <teabot@gitea.io>
2023-05-11 09:45:47 +02:00
|
|
|
m.Get("/diagnosis", admin.MonitorDiagnosis)
|
2020-01-07 12:23:09 +01:00
|
|
|
})
|
2017-04-25 09:24:51 +02:00
|
|
|
|
|
|
|
|
m.Group("/users", func() {
|
|
|
|
|
m.Get("", admin.Users)
|
2022-12-12 09:09:26 +01:00
|
|
|
m.Combo("/new").Get(admin.NewUser).Post(web.Bind(forms.AdminCreateUserForm{}), admin.NewUserPost)
|
2023-08-31 11:21:18 +02:00
|
|
|
m.Get("/{userid}", admin.ViewUser)
|
|
|
|
|
m.Combo("/{userid}/edit").Get(admin.EditUser).Post(web.Bind(forms.AdminEditUserForm{}), admin.EditUserPost)
|
2021-01-26 16:36:53 +01:00
|
|
|
m.Post("/{userid}/delete", admin.DeleteUser)
|
2022-12-12 09:09:26 +01:00
|
|
|
m.Post("/{userid}/avatar", web.Bind(forms.AvatarForm{}), admin.AvatarPost)
|
2021-11-16 20:13:13 +01:00
|
|
|
m.Post("/{userid}/avatar/delete", admin.DeleteAvatar)
|
2017-04-25 09:24:51 +02:00
|
|
|
})
|
|
|
|
|
|
2020-03-02 19:25:36 +01:00
|
|
|
m.Group("/emails", func() {
|
|
|
|
|
m.Get("", admin.Emails)
|
|
|
|
|
m.Post("/activate", admin.ActivateEmail)
|
|
|
|
|
})
|
|
|
|
|
|
2017-04-25 09:24:51 +02:00
|
|
|
m.Group("/orgs", func() {
|
|
|
|
|
m.Get("", admin.Organizations)
|
|
|
|
|
})
|
|
|
|
|
|
|
|
|
|
m.Group("/repos", func() {
|
|
|
|
|
m.Get("", admin.Repos)
|
2020-09-25 06:09:23 +02:00
|
|
|
m.Combo("/unadopted").Get(admin.UnadoptedRepos).Post(admin.AdoptOrDeleteRepository)
|
2017-04-25 09:24:51 +02:00
|
|
|
m.Post("/delete", admin.DeleteRepo)
|
|
|
|
|
})
|
|
|
|
|
|
2022-11-20 15:08:38 +01:00
|
|
|
m.Group("/packages", func() {
|
|
|
|
|
m.Get("", admin.Packages)
|
|
|
|
|
m.Post("/delete", admin.DeletePackageVersion)
|
2023-08-08 02:46:10 +02:00
|
|
|
m.Post("/cleanup", admin.CleanupExpiredData)
|
2022-11-20 15:08:38 +01:00
|
|
|
}, packagesEnabled)
|
2022-03-30 10:42:47 +02:00
|
|
|
|
2021-01-15 00:24:03 +01:00
|
|
|
m.Group("/hooks", func() {
|
2020-03-08 23:08:05 +01:00
|
|
|
m.Get("", admin.DefaultOrSystemWebhooks)
|
|
|
|
|
m.Post("/delete", admin.DeleteDefaultOrSystemWebhook)
|
2022-01-05 22:00:20 +01:00
|
|
|
m.Group("/{id}", func() {
|
2023-07-02 02:59:32 +02:00
|
|
|
m.Get("", repo_setting.WebHooksEdit)
|
|
|
|
|
m.Post("/replay/{uuid}", repo_setting.ReplayWebhook)
|
2022-01-05 22:00:20 +01:00
|
|
|
})
|
2023-03-10 15:28:32 +01:00
|
|
|
addWebhookEditRoutes()
|
2021-02-11 18:34:34 +01:00
|
|
|
}, webhooksEnabled)
|
2019-03-19 03:33:20 +01:00
|
|
|
|
2021-01-26 16:36:53 +01:00
|
|
|
m.Group("/{configType:default-hooks|system-hooks}", func() {
|
2023-03-10 15:28:32 +01:00
|
|
|
addWebhookAddRoutes()
|
2021-01-15 00:24:03 +01:00
|
|
|
})
|
|
|
|
|
|
2017-04-25 09:24:51 +02:00
|
|
|
m.Group("/auths", func() {
|
|
|
|
|
m.Get("", admin.Authentications)
|
2022-12-12 09:09:26 +01:00
|
|
|
m.Combo("/new").Get(admin.NewAuthSource).Post(web.Bind(forms.AuthenticationForm{}), admin.NewAuthSourcePost)
|
2021-01-26 16:36:53 +01:00
|
|
|
m.Combo("/{authid}").Get(admin.EditAuthSource).
|
2022-12-12 09:09:26 +01:00
|
|
|
Post(web.Bind(forms.AuthenticationForm{}), admin.EditAuthSourcePost)
|
2021-01-26 16:36:53 +01:00
|
|
|
m.Post("/{authid}/delete", admin.DeleteAuthSource)
|
2017-04-25 09:24:51 +02:00
|
|
|
})
|
|
|
|
|
|
|
|
|
|
m.Group("/notices", func() {
|
|
|
|
|
m.Get("", admin.Notices)
|
|
|
|
|
m.Post("/delete", admin.DeleteNotices)
|
2020-02-26 17:25:54 +01:00
|
|
|
m.Post("/empty", admin.EmptyNotices)
|
2017-04-25 09:24:51 +02:00
|
|
|
})
|
2022-10-12 16:08:29 +02:00
|
|
|
|
|
|
|
|
m.Group("/applications", func() {
|
|
|
|
|
m.Get("", admin.Applications)
|
2022-12-12 09:09:26 +01:00
|
|
|
m.Post("/oauth2", web.Bind(forms.EditOAuth2ApplicationForm{}), admin.ApplicationsPost)
|
2022-10-12 16:08:29 +02:00
|
|
|
m.Group("/oauth2/{id}", func() {
|
2022-12-12 09:09:26 +01:00
|
|
|
m.Combo("").Get(admin.EditApplication).Post(web.Bind(forms.EditOAuth2ApplicationForm{}), admin.EditApplicationPost)
|
2022-10-12 16:08:29 +02:00
|
|
|
m.Post("/regenerate_secret", admin.ApplicationsRegenerateSecret)
|
|
|
|
|
m.Post("/delete", admin.DeleteApplication)
|
|
|
|
|
})
|
|
|
|
|
}, func(ctx *context.Context) {
|
|
|
|
|
if !setting.OAuth2.Enable {
|
|
|
|
|
ctx.Error(http.StatusForbidden)
|
|
|
|
|
return
|
|
|
|
|
}
|
|
|
|
|
})
|

Implement actions (#21937)
Close #13539.
Co-authored by: @lunny @appleboy @fuxiaohei and others.
Related projects:
- https://gitea.com/gitea/actions-proto-def
- https://gitea.com/gitea/actions-proto-go
- https://gitea.com/gitea/act
- https://gitea.com/gitea/act_runner
### Summary
The target of this PR is to bring a basic implementation of "Actions",
an internal CI/CD system of Gitea. That means even though it has been
merged, the state of the feature is **EXPERIMENTAL**, and please note
that:
- It is disabled by default;
- It shouldn't be used in a production environment currently;
- It shouldn't be used in a public Gitea instance currently;
- Breaking changes may be made before it's stable.
**Please comment on #13539 if you have any different product design
ideas**, all decisions reached there will be adopted here. But in this
PR, we don't talk about **naming, feature-creep or alternatives**.
### ⚠️ Breaking
`gitea-actions` will become a reserved user name. If a user with the
name already exists in the database, it is recommended to rename it.
### Some important reviews
- What is `DEFAULT_ACTIONS_URL` in `app.ini` for?
- https://github.com/go-gitea/gitea/pull/21937#discussion_r1055954954
- Why the api for runners is not under the normal `/api/v1` prefix?
- https://github.com/go-gitea/gitea/pull/21937#discussion_r1061173592
- Why DBFS?
- https://github.com/go-gitea/gitea/pull/21937#discussion_r1061301178
- Why ignore events triggered by `gitea-actions` bot?
- https://github.com/go-gitea/gitea/pull/21937#discussion_r1063254103
- Why there's no permission control for actions?
- https://github.com/go-gitea/gitea/pull/21937#discussion_r1090229868
### What it looks like
<details>
#### Manage runners
<img width="1792" alt="image"
src="https://user-images.githubusercontent.com/9418365/205870657-c72f590e-2e08-4cd4-be7f-2e0abb299bbf.png">
#### List runs
<img width="1792" alt="image"
src="https://user-images.githubusercontent.com/9418365/205872794-50fde990-2b45-48c1-a178-908e4ec5b627.png">
#### View logs
<img width="1792" alt="image"
src="https://user-images.githubusercontent.com/9418365/205872501-9b7b9000-9542-4991-8f55-18ccdada77c3.png">
</details>
### How to try it
<details>
#### 1. Start Gitea
Clone this branch and [install from
source](https://docs.gitea.io/en-us/install-from-source).
Add additional configurations in `app.ini` to enable Actions:
```ini
[actions]
ENABLED = true
```
Start it.
If all is well, you'll see the management page of runners:
<img width="1792" alt="image"
src="https://user-images.githubusercontent.com/9418365/205877365-8e30a780-9b10-4154-b3e8-ee6c3cb35a59.png">
#### 2. Start runner
Clone the [act_runner](https://gitea.com/gitea/act_runner), and follow
the
[README](https://gitea.com/gitea/act_runner/src/branch/main/README.md)
to start it.
If all is well, you'll see a new runner has been added:
<img width="1792" alt="image"
src="https://user-images.githubusercontent.com/9418365/205878000-216f5937-e696-470d-b66c-8473987d91c3.png">
#### 3. Enable actions for a repo
Create a new repo or open an existing one, check the `Actions` checkbox
in settings and submit.
<img width="1792" alt="image"
src="https://user-images.githubusercontent.com/9418365/205879705-53e09208-73c0-4b3e-a123-2dcf9aba4b9c.png">
<img width="1792" alt="image"
src="https://user-images.githubusercontent.com/9418365/205879383-23f3d08f-1a85-41dd-a8b3-54e2ee6453e8.png">
If all is well, you'll see a new tab "Actions":
<img width="1792" alt="image"
src="https://user-images.githubusercontent.com/9418365/205881648-a8072d8c-5803-4d76-b8a8-9b2fb49516c1.png">
#### 4. Upload workflow files
Upload some workflow files to `.gitea/workflows/xxx.yaml`, you can
follow the [quickstart](https://docs.github.com/en/actions/quickstart)
of GitHub Actions. Yes, Gitea Actions is compatible with GitHub Actions
in most cases, you can use the same demo:
```yaml
name: GitHub Actions Demo
run-name: ${{ github.actor }} is testing out GitHub Actions 🚀
on: [push]
jobs:
Explore-GitHub-Actions:
runs-on: ubuntu-latest
steps:
- run: echo "🎉 The job was automatically triggered by a ${{ github.event_name }} event."
- run: echo "🐧 This job is now running on a ${{ runner.os }} server hosted by GitHub!"
- run: echo "🔎 The name of your branch is ${{ github.ref }} and your repository is ${{ github.repository }}."
- name: Check out repository code
uses: actions/checkout@v3
- run: echo "💡 The ${{ github.repository }} repository has been cloned to the runner."
- run: echo "🖥️ The workflow is now ready to test your code on the runner."
- name: List files in the repository
run: |
ls ${{ github.workspace }}
- run: echo "🍏 This job's status is ${{ job.status }}."
```
If all is well, you'll see a new run in `Actions` tab:
<img width="1792" alt="image"
src="https://user-images.githubusercontent.com/9418365/205884473-79a874bc-171b-4aaf-acd5-0241a45c3b53.png">
#### 5. Check the logs of jobs
Click a run and you'll see the logs:
<img width="1792" alt="image"
src="https://user-images.githubusercontent.com/9418365/205884800-994b0374-67f7-48ff-be9a-4c53f3141547.png">
#### 6. Go on
You can try more examples in [the
documents](https://docs.github.com/en/actions/using-workflows/workflow-syntax-for-github-actions)
of GitHub Actions, then you might find a lot of bugs.
Come on, PRs are welcome.
</details>
See also: [Feature Preview: Gitea
Actions](https://blog.gitea.io/2022/12/feature-preview-gitea-actions/)
---------
Co-authored-by: a1012112796 <1012112796@qq.com>
Co-authored-by: Lunny Xiao <xiaolunwen@gmail.com>
Co-authored-by: delvh <dev.lh@web.de>
Co-authored-by: ChristopherHX <christopher.homberger@web.de>
Co-authored-by: John Olheiser <john.olheiser@gmail.com>
2023-01-31 02:45:19 +01:00
|
|
|
|
2023-04-28 02:08:47 +02:00
|
|
|
m.Group("/actions", func() {
|
|
|
|
|
m.Get("", admin.RedirectToDefaultSetting)
|
|
|
|
|
addSettingsRunnersRoutes()
|
|
|
|
|
})
|
|
|
|
|
}, adminReq, ctxDataSet("EnableOAuth2", setting.OAuth2.Enable, "EnablePackages", setting.Packages.Enabled))
|
2017-04-25 09:24:51 +02:00
|
|
|
// ***** END: Admin *****
|
|
|
|
|
|
|
|
|
|
m.Group("", func() {
|
2023-04-27 08:06:45 +02:00
|
|
|
m.Get("/{username}", user.UsernameSubRoute)
|
2021-01-26 16:36:53 +01:00
|
|
|
m.Get("/attachments/{uuid}", repo.GetAttachment)
|
2017-04-25 09:24:51 +02:00
|
|
|
}, ignSignIn)
|
|
|
|
|
|
2022-03-26 10:04:22 +01:00
|
|
|
m.Post("/{username}", reqSignIn, context_service.UserAssignmentWeb(), user.Action)
|
2017-04-25 09:24:51 +02:00
|
|
|
|
|
|
|
|
reqRepoAdmin := context.RequireRepoAdmin()
|
2021-11-09 20:57:58 +01:00
|
|
|
reqRepoCodeWriter := context.RequireRepoWriter(unit.TypeCode)
|
2022-04-28 17:45:33 +02:00
|
|
|
canEnableEditor := context.CanEnableEditor()
|
2021-11-09 20:57:58 +01:00
|
|
|
reqRepoCodeReader := context.RequireRepoReader(unit.TypeCode)
|
|
|
|
|
reqRepoReleaseWriter := context.RequireRepoWriter(unit.TypeReleases)
|
|
|
|
|
reqRepoReleaseReader := context.RequireRepoReader(unit.TypeReleases)
|
|
|
|
|
reqRepoWikiWriter := context.RequireRepoWriter(unit.TypeWiki)
|
|
|
|
|
reqRepoIssueReader := context.RequireRepoReader(unit.TypeIssues)
|
|
|
|
|
reqRepoPullsReader := context.RequireRepoReader(unit.TypePullRequests)
|
|
|
|
|
reqRepoIssuesOrPullsWriter := context.RequireRepoWriterOr(unit.TypeIssues, unit.TypePullRequests)
|
|
|
|
|
reqRepoIssuesOrPullsReader := context.RequireRepoReaderOr(unit.TypeIssues, unit.TypePullRequests)
|
|
|
|
|
reqRepoProjectsReader := context.RequireRepoReader(unit.TypeProjects)
|
|
|
|
|
reqRepoProjectsWriter := context.RequireRepoWriter(unit.TypeProjects)
|

Implement actions (#21937)
Close #13539.
Co-authored by: @lunny @appleboy @fuxiaohei and others.
Related projects:
- https://gitea.com/gitea/actions-proto-def
- https://gitea.com/gitea/actions-proto-go
- https://gitea.com/gitea/act
- https://gitea.com/gitea/act_runner
### Summary
The target of this PR is to bring a basic implementation of "Actions",
an internal CI/CD system of Gitea. That means even though it has been
merged, the state of the feature is **EXPERIMENTAL**, and please note
that:
- It is disabled by default;
- It shouldn't be used in a production environment currently;
- It shouldn't be used in a public Gitea instance currently;
- Breaking changes may be made before it's stable.
**Please comment on #13539 if you have any different product design
ideas**, all decisions reached there will be adopted here. But in this
PR, we don't talk about **naming, feature-creep or alternatives**.
### ⚠️ Breaking
`gitea-actions` will become a reserved user name. If a user with the
name already exists in the database, it is recommended to rename it.
### Some important reviews
- What is `DEFAULT_ACTIONS_URL` in `app.ini` for?
- https://github.com/go-gitea/gitea/pull/21937#discussion_r1055954954
- Why the api for runners is not under the normal `/api/v1` prefix?
- https://github.com/go-gitea/gitea/pull/21937#discussion_r1061173592
- Why DBFS?
- https://github.com/go-gitea/gitea/pull/21937#discussion_r1061301178
- Why ignore events triggered by `gitea-actions` bot?
- https://github.com/go-gitea/gitea/pull/21937#discussion_r1063254103
- Why there's no permission control for actions?
- https://github.com/go-gitea/gitea/pull/21937#discussion_r1090229868
### What it looks like
<details>
#### Manage runners
<img width="1792" alt="image"
src="https://user-images.githubusercontent.com/9418365/205870657-c72f590e-2e08-4cd4-be7f-2e0abb299bbf.png">
#### List runs
<img width="1792" alt="image"
src="https://user-images.githubusercontent.com/9418365/205872794-50fde990-2b45-48c1-a178-908e4ec5b627.png">
#### View logs
<img width="1792" alt="image"
src="https://user-images.githubusercontent.com/9418365/205872501-9b7b9000-9542-4991-8f55-18ccdada77c3.png">
</details>
### How to try it
<details>
#### 1. Start Gitea
Clone this branch and [install from
source](https://docs.gitea.io/en-us/install-from-source).
Add additional configurations in `app.ini` to enable Actions:
```ini
[actions]
ENABLED = true
```
Start it.
If all is well, you'll see the management page of runners:
<img width="1792" alt="image"
src="https://user-images.githubusercontent.com/9418365/205877365-8e30a780-9b10-4154-b3e8-ee6c3cb35a59.png">
#### 2. Start runner
Clone the [act_runner](https://gitea.com/gitea/act_runner), and follow
the
[README](https://gitea.com/gitea/act_runner/src/branch/main/README.md)
to start it.
If all is well, you'll see a new runner has been added:
<img width="1792" alt="image"
src="https://user-images.githubusercontent.com/9418365/205878000-216f5937-e696-470d-b66c-8473987d91c3.png">
#### 3. Enable actions for a repo
Create a new repo or open an existing one, check the `Actions` checkbox
in settings and submit.
<img width="1792" alt="image"
src="https://user-images.githubusercontent.com/9418365/205879705-53e09208-73c0-4b3e-a123-2dcf9aba4b9c.png">
<img width="1792" alt="image"
src="https://user-images.githubusercontent.com/9418365/205879383-23f3d08f-1a85-41dd-a8b3-54e2ee6453e8.png">
If all is well, you'll see a new tab "Actions":
<img width="1792" alt="image"
src="https://user-images.githubusercontent.com/9418365/205881648-a8072d8c-5803-4d76-b8a8-9b2fb49516c1.png">
#### 4. Upload workflow files
Upload some workflow files to `.gitea/workflows/xxx.yaml`, you can
follow the [quickstart](https://docs.github.com/en/actions/quickstart)
of GitHub Actions. Yes, Gitea Actions is compatible with GitHub Actions
in most cases, you can use the same demo:
```yaml
name: GitHub Actions Demo
run-name: ${{ github.actor }} is testing out GitHub Actions 🚀
on: [push]
jobs:
Explore-GitHub-Actions:
runs-on: ubuntu-latest
steps:
- run: echo "🎉 The job was automatically triggered by a ${{ github.event_name }} event."
- run: echo "🐧 This job is now running on a ${{ runner.os }} server hosted by GitHub!"
- run: echo "🔎 The name of your branch is ${{ github.ref }} and your repository is ${{ github.repository }}."
- name: Check out repository code
uses: actions/checkout@v3
- run: echo "💡 The ${{ github.repository }} repository has been cloned to the runner."
- run: echo "🖥️ The workflow is now ready to test your code on the runner."
- name: List files in the repository
run: |
ls ${{ github.workspace }}
- run: echo "🍏 This job's status is ${{ job.status }}."
```
If all is well, you'll see a new run in `Actions` tab:
<img width="1792" alt="image"
src="https://user-images.githubusercontent.com/9418365/205884473-79a874bc-171b-4aaf-acd5-0241a45c3b53.png">
#### 5. Check the logs of jobs
Click a run and you'll see the logs:
<img width="1792" alt="image"
src="https://user-images.githubusercontent.com/9418365/205884800-994b0374-67f7-48ff-be9a-4c53f3141547.png">
#### 6. Go on
You can try more examples in [the
documents](https://docs.github.com/en/actions/using-workflows/workflow-syntax-for-github-actions)
of GitHub Actions, then you might find a lot of bugs.
Come on, PRs are welcome.
</details>
See also: [Feature Preview: Gitea
Actions](https://blog.gitea.io/2022/12/feature-preview-gitea-actions/)
---------
Co-authored-by: a1012112796 <1012112796@qq.com>
Co-authored-by: Lunny Xiao <xiaolunwen@gmail.com>
Co-authored-by: delvh <dev.lh@web.de>
Co-authored-by: ChristopherHX <christopher.homberger@web.de>
Co-authored-by: John Olheiser <john.olheiser@gmail.com>
2023-01-31 02:45:19 +01:00
|
|
|
reqRepoActionsReader := context.RequireRepoReader(unit.TypeActions)
|
|
|
|
|
reqRepoActionsWriter := context.RequireRepoWriter(unit.TypeActions)
|
2017-04-25 09:24:51 +02:00
|
|
|
|
2022-03-30 10:42:47 +02:00
|
|
|
reqPackageAccess := func(accessMode perm.AccessMode) func(ctx *context.Context) {
|
|
|
|
|
return func(ctx *context.Context) {
|
|
|
|
|
if ctx.Package.AccessMode < accessMode && !ctx.IsUserSiteAdmin() {
|
|
|
|
|
ctx.NotFound("", nil)
|
|
|
|
|
}
|
|
|
|
|
}
|
|
|
|
|
}
|
|
|
|
|
|
2017-04-25 09:24:51 +02:00
|
|
|
// ***** START: Organization *****
|
2022-07-15 16:21:54 +02:00
|
|
|
m.Group("/org", func() {
|
|
|
|
|
m.Group("/{org}", func() {
|
|
|
|
|
m.Get("/members", org.Members)
|
|
|
|
|
}, context.OrgAssignment())
|
|
|
|
|
}, ignSignIn)
|
|
|
|
|
|
2017-04-25 09:24:51 +02:00
|
|
|
m.Group("/org", func() {
|
|
|
|
|
m.Group("", func() {
|
|
|
|
|
m.Get("/create", org.Create)
|
2022-12-12 09:09:26 +01:00
|
|
|
m.Post("/create", web.Bind(forms.CreateOrgForm{}), org.CreatePost)
|
2017-04-25 09:24:51 +02:00
|
|
|
})
|
|
|
|
|
|
2022-10-19 14:40:28 +02:00
|
|
|
m.Group("/invite/{token}", func() {
|
|
|
|
|
m.Get("", org.TeamInvite)
|
|
|
|
|
m.Post("", org.TeamInvitePost)
|
|
|
|
|
})
|
|
|
|
|
|
2021-01-26 16:36:53 +01:00
|
|
|
m.Group("/{org}", func() {
|
2017-04-25 09:24:51 +02:00
|
|
|
m.Get("/dashboard", user.Dashboard)
|
2021-01-26 16:36:53 +01:00
|
|
|
m.Get("/dashboard/{team}", user.Dashboard)
|
2021-01-13 05:19:17 +01:00
|
|
|
m.Get("/issues", user.Issues)
|
2021-01-26 16:36:53 +01:00
|
|
|
m.Get("/issues/{team}", user.Issues)
|
2021-01-13 05:19:17 +01:00
|
|
|
m.Get("/pulls", user.Pulls)
|
2021-01-26 16:36:53 +01:00
|
|
|
m.Get("/pulls/{team}", user.Pulls)
|
2019-12-15 15:20:08 +01:00
|
|
|
m.Get("/milestones", reqMilestonesDashboardPageEnabled, user.Milestones)
|
2021-01-26 16:36:53 +01:00
|
|
|
m.Get("/milestones/{team}", reqMilestonesDashboardPageEnabled, user.Milestones)
|
|
|
|
|
m.Post("/members/action/{action}", org.MembersAction)
|
2017-04-25 09:24:51 +02:00
|
|
|
m.Get("/teams", org.Teams)
|
2020-12-27 20:58:03 +01:00
|
|
|
}, context.OrgAssignment(true, false, true))
|
2017-04-25 09:24:51 +02:00
|
|
|
|
2021-01-26 16:36:53 +01:00
|
|
|
m.Group("/{org}", func() {
|
|
|
|
|
m.Get("/teams/{team}", org.TeamMembers)
|
|
|
|
|
m.Get("/teams/{team}/repositories", org.TeamRepositories)
|
|
|
|
|
m.Post("/teams/{team}/action/{action}", org.TeamsAction)
|
|
|
|
|
m.Post("/teams/{team}/action/repo/{action}", org.TeamsRepoAction)
|
2017-04-25 09:24:51 +02:00
|
|
|
}, context.OrgAssignment(true, false, true))
|
|
|
|
|
|
2021-01-26 16:36:53 +01:00
|
|
|
m.Group("/{org}", func() {
|
2017-04-25 09:24:51 +02:00
|
|
|
m.Get("/teams/new", org.NewTeam)
|
2022-12-12 09:09:26 +01:00
|
|
|
m.Post("/teams/new", web.Bind(forms.CreateTeamForm{}), org.NewTeamPost)
|
2022-04-07 20:59:56 +02:00
|
|
|
m.Get("/teams/-/search", org.SearchTeam)
|
2021-01-26 16:36:53 +01:00
|
|
|
m.Get("/teams/{team}/edit", org.EditTeam)
|
2022-12-12 09:09:26 +01:00
|
|
|
m.Post("/teams/{team}/edit", web.Bind(forms.CreateTeamForm{}), org.EditTeamPost)
|
2021-01-26 16:36:53 +01:00
|
|
|
m.Post("/teams/{team}/delete", org.DeleteTeam)
|
2017-04-25 09:24:51 +02:00
|
|
|
|
|
|
|
|
m.Group("/settings", func() {
|
|
|
|
|
m.Combo("").Get(org.Settings).
|
2022-12-12 09:09:26 +01:00
|
|
|
Post(web.Bind(forms.UpdateOrgSettingForm{}), org.SettingsPost)
|
|
|
|
|
m.Post("/avatar", web.Bind(forms.AvatarForm{}), org.SettingsAvatar)
|
2017-04-25 09:24:51 +02:00
|
|
|
m.Post("/avatar/delete", org.SettingsDeleteAvatar)
|
2022-10-09 14:07:41 +02:00
|
|
|
m.Group("/applications", func() {
|
|
|
|
|
m.Get("", org.Applications)
|
2022-12-12 09:09:26 +01:00
|
|
|
m.Post("/oauth2", web.Bind(forms.EditOAuth2ApplicationForm{}), org.OAuthApplicationsPost)
|
2022-10-09 14:07:41 +02:00
|
|
|
m.Group("/oauth2/{id}", func() {
|
2022-12-12 09:09:26 +01:00
|
|
|
m.Combo("").Get(org.OAuth2ApplicationShow).Post(web.Bind(forms.EditOAuth2ApplicationForm{}), org.OAuth2ApplicationEdit)
|
2022-10-09 14:07:41 +02:00
|
|
|
m.Post("/regenerate_secret", org.OAuthApplicationsRegenerateSecret)
|
|
|
|
|
m.Post("/delete", org.DeleteOAuth2Application)
|
|
|
|
|
})
|
|
|
|
|
}, func(ctx *context.Context) {
|
|
|
|
|
if !setting.OAuth2.Enable {
|
|
|
|
|
ctx.Error(http.StatusForbidden)
|
|
|
|
|
return
|
|
|
|
|
}
|
|
|
|
|
})
|
2017-04-25 09:24:51 +02:00
|
|
|
|
|
|
|
|
m.Group("/hooks", func() {
|
|
|
|
|
m.Get("", org.Webhooks)
|
|
|
|
|
m.Post("/delete", org.DeleteWebhook)
|
2023-03-10 15:28:32 +01:00
|
|
|
addWebhookAddRoutes()
|
2022-01-05 22:00:20 +01:00
|
|
|
m.Group("/{id}", func() {
|
2023-07-02 02:59:32 +02:00
|
|
|
m.Get("", repo_setting.WebHooksEdit)
|
|
|
|
|
m.Post("/replay/{uuid}", repo_setting.ReplayWebhook)
|
2022-01-05 22:00:20 +01:00
|
|
|
})
|
2023-03-10 15:28:32 +01:00
|
|
|
addWebhookEditRoutes()
|
2023-04-28 02:08:47 +02:00
|
|
|
}, webhooksEnabled)
|
2017-04-25 09:24:51 +02:00
|
|
|
|

Add Organization Wide Labels (#10814)
* Add organization wide labels
Implement organization wide labels similar to organization wide
webhooks. This lets you create individual labels for organizations that can be used
for all repos under that organization (so being able to reuse the same
label across multiple repos).
This makes it possible for small organizations with many repos to use
labels effectively.
Fixes #7406
* Add migration
* remove comments
* fix tests
* Update options/locale/locale_en-US.ini
Removed unused translation string
* show org labels in issue search label filter
* Use more clear var name
* rename migration after merge from master
* comment typo
* update migration again after rebase with master
* check for orgID <=0 per guillep2k review
* fmt
* Apply suggestions from code review
Co-Authored-By: guillep2k <18600385+guillep2k@users.noreply.github.com>
* remove unused code
* Make sure RepoID is 0 when searching orgID per code review
* more changes/code review requests
* More descriptive translation var per code review
* func description/delete comment when issue label deleted instead of hiding it
* remove comment
* only use issues in that repo when calculating number of open issues for org label on repo label page
* Add integration test for IssuesSearch API with labels
* remove unused function
* Update models/issue_label.go
Co-Authored-By: guillep2k <18600385+guillep2k@users.noreply.github.com>
* Use subquery in GetLabelIDsInReposByNames
* Fix tests to use correct orgID
* fix more tests
* IssuesSearch api now uses new BuildLabelNamesIssueIDsCondition. Add a few more tests as well
* update comment for clarity
* Revert previous code change now that we can use the new BuildLabelNamesIssueIDsCondition
* Don't sort repos by date in IssuesSearch API
After much debugging I've found a strange issue where in some cases MySQL will return a different result than other enigines if a query is sorted by a null collumn. For example with our integration test data where we don't set updated_unix in repository fixtures:
SELECT `id`, `owner_id`, `owner_name`, `lower_name`, `name`, `description`, `website`, `original_service_type`, `original_url`, `default_branch`, `num_watches`, `num_stars`, `num_forks`, `num_issues`, `num_closed_issues`, `num_pulls`, `num_closed_pulls`, `num_milestones`, `num_closed_milestones`, `is_private`, `is_empty`, `is_archived`, `is_mirror`, `status`, `is_fork`, `fork_id`, `is_template`, `template_id`, `size`, `is_fsck_enabled`, `close_issues_via_commit_in_any_branch`, `topics`, `avatar`, `created_unix`, `updated_unix` FROM `repository` ORDER BY updated_unix DESC LIMIT 15 OFFSET 45
Returns different results for MySQL than other engines. However, the similar query:
SELECT `id`, `owner_id`, `owner_name`, `lower_name`, `name`, `description`, `website`, `original_service_type`, `original_url`, `default_branch`, `num_watches`, `num_stars`, `num_forks`, `num_issues`, `num_closed_issues`, `num_pulls`, `num_closed_pulls`, `num_milestones`, `num_closed_milestones`, `is_private`, `is_empty`, `is_archived`, `is_mirror`, `status`, `is_fork`, `fork_id`, `is_template`, `template_id`, `size`, `is_fsck_enabled`, `close_issues_via_commit_in_any_branch`, `topics`, `avatar`, `created_unix`, `updated_unix` FROM `repository` ORDER BY updated_unix DESC LIMIT 15 OFFSET 30
Returns the same results.
This causes integration tests to fail on MySQL in certain cases but would never show up in a real installation. Since this API call always returns issues based on the optionally provided repo_priority_id or the issueID itself, there is no change to results by changing the repo sorting method used to get ids earlier in the function.
* linter is back!
* code review
* remove now unused option
* Fix newline at end of files
* more unused code
* update to master
* check for matching ids before query
* Update models/issue_label.go
Co-Authored-By: 6543 <6543@obermui.de>
* Update models/issue_label.go
* update comments
* Update routers/org/setting.go
Co-authored-by: Lauris BH <lauris@nix.lv>
Co-authored-by: guillep2k <18600385+guillep2k@users.noreply.github.com>
Co-authored-by: 6543 <6543@obermui.de>
2020-04-01 06:14:46 +02:00
|
|
|
m.Group("/labels", func() {
|
|
|
|
|
m.Get("", org.RetrieveLabels, org.Labels)
|
2022-12-12 09:09:26 +01:00
|
|
|
m.Post("/new", web.Bind(forms.CreateLabelForm{}), org.NewLabel)
|
|
|
|
|
m.Post("/edit", web.Bind(forms.CreateLabelForm{}), org.UpdateLabel)
|

Add Organization Wide Labels (#10814)
* Add organization wide labels
Implement organization wide labels similar to organization wide
webhooks. This lets you create individual labels for organizations that can be used
for all repos under that organization (so being able to reuse the same
label across multiple repos).
This makes it possible for small organizations with many repos to use
labels effectively.
Fixes #7406
* Add migration
* remove comments
* fix tests
* Update options/locale/locale_en-US.ini
Removed unused translation string
* show org labels in issue search label filter
* Use more clear var name
* rename migration after merge from master
* comment typo
* update migration again after rebase with master
* check for orgID <=0 per guillep2k review
* fmt
* Apply suggestions from code review
Co-Authored-By: guillep2k <18600385+guillep2k@users.noreply.github.com>
* remove unused code
* Make sure RepoID is 0 when searching orgID per code review
* more changes/code review requests
* More descriptive translation var per code review
* func description/delete comment when issue label deleted instead of hiding it
* remove comment
* only use issues in that repo when calculating number of open issues for org label on repo label page
* Add integration test for IssuesSearch API with labels
* remove unused function
* Update models/issue_label.go
Co-Authored-By: guillep2k <18600385+guillep2k@users.noreply.github.com>
* Use subquery in GetLabelIDsInReposByNames
* Fix tests to use correct orgID
* fix more tests
* IssuesSearch api now uses new BuildLabelNamesIssueIDsCondition. Add a few more tests as well
* update comment for clarity
* Revert previous code change now that we can use the new BuildLabelNamesIssueIDsCondition
* Don't sort repos by date in IssuesSearch API
After much debugging I've found a strange issue where in some cases MySQL will return a different result than other enigines if a query is sorted by a null collumn. For example with our integration test data where we don't set updated_unix in repository fixtures:
SELECT `id`, `owner_id`, `owner_name`, `lower_name`, `name`, `description`, `website`, `original_service_type`, `original_url`, `default_branch`, `num_watches`, `num_stars`, `num_forks`, `num_issues`, `num_closed_issues`, `num_pulls`, `num_closed_pulls`, `num_milestones`, `num_closed_milestones`, `is_private`, `is_empty`, `is_archived`, `is_mirror`, `status`, `is_fork`, `fork_id`, `is_template`, `template_id`, `size`, `is_fsck_enabled`, `close_issues_via_commit_in_any_branch`, `topics`, `avatar`, `created_unix`, `updated_unix` FROM `repository` ORDER BY updated_unix DESC LIMIT 15 OFFSET 45
Returns different results for MySQL than other engines. However, the similar query:
SELECT `id`, `owner_id`, `owner_name`, `lower_name`, `name`, `description`, `website`, `original_service_type`, `original_url`, `default_branch`, `num_watches`, `num_stars`, `num_forks`, `num_issues`, `num_closed_issues`, `num_pulls`, `num_closed_pulls`, `num_milestones`, `num_closed_milestones`, `is_private`, `is_empty`, `is_archived`, `is_mirror`, `status`, `is_fork`, `fork_id`, `is_template`, `template_id`, `size`, `is_fsck_enabled`, `close_issues_via_commit_in_any_branch`, `topics`, `avatar`, `created_unix`, `updated_unix` FROM `repository` ORDER BY updated_unix DESC LIMIT 15 OFFSET 30
Returns the same results.
This causes integration tests to fail on MySQL in certain cases but would never show up in a real installation. Since this API call always returns issues based on the optionally provided repo_priority_id or the issueID itself, there is no change to results by changing the repo sorting method used to get ids earlier in the function.
* linter is back!
* code review
* remove now unused option
* Fix newline at end of files
* more unused code
* update to master
* check for matching ids before query
* Update models/issue_label.go
Co-Authored-By: 6543 <6543@obermui.de>
* Update models/issue_label.go
* update comments
* Update routers/org/setting.go
Co-authored-by: Lauris BH <lauris@nix.lv>
Co-authored-by: guillep2k <18600385+guillep2k@users.noreply.github.com>
Co-authored-by: 6543 <6543@obermui.de>
2020-04-01 06:14:46 +02:00
|
|
|
m.Post("/delete", org.DeleteLabel)
|
2022-12-12 09:09:26 +01:00
|
|
|
m.Post("/initialize", web.Bind(forms.InitializeLabelsForm{}), org.InitializeLabels)
|

Add Organization Wide Labels (#10814)
* Add organization wide labels
Implement organization wide labels similar to organization wide
webhooks. This lets you create individual labels for organizations that can be used
for all repos under that organization (so being able to reuse the same
label across multiple repos).
This makes it possible for small organizations with many repos to use
labels effectively.
Fixes #7406
* Add migration
* remove comments
* fix tests
* Update options/locale/locale_en-US.ini
Removed unused translation string
* show org labels in issue search label filter
* Use more clear var name
* rename migration after merge from master
* comment typo
* update migration again after rebase with master
* check for orgID <=0 per guillep2k review
* fmt
* Apply suggestions from code review
Co-Authored-By: guillep2k <18600385+guillep2k@users.noreply.github.com>
* remove unused code
* Make sure RepoID is 0 when searching orgID per code review
* more changes/code review requests
* More descriptive translation var per code review
* func description/delete comment when issue label deleted instead of hiding it
* remove comment
* only use issues in that repo when calculating number of open issues for org label on repo label page
* Add integration test for IssuesSearch API with labels
* remove unused function
* Update models/issue_label.go
Co-Authored-By: guillep2k <18600385+guillep2k@users.noreply.github.com>
* Use subquery in GetLabelIDsInReposByNames
* Fix tests to use correct orgID
* fix more tests
* IssuesSearch api now uses new BuildLabelNamesIssueIDsCondition. Add a few more tests as well
* update comment for clarity
* Revert previous code change now that we can use the new BuildLabelNamesIssueIDsCondition
* Don't sort repos by date in IssuesSearch API
After much debugging I've found a strange issue where in some cases MySQL will return a different result than other enigines if a query is sorted by a null collumn. For example with our integration test data where we don't set updated_unix in repository fixtures:
SELECT `id`, `owner_id`, `owner_name`, `lower_name`, `name`, `description`, `website`, `original_service_type`, `original_url`, `default_branch`, `num_watches`, `num_stars`, `num_forks`, `num_issues`, `num_closed_issues`, `num_pulls`, `num_closed_pulls`, `num_milestones`, `num_closed_milestones`, `is_private`, `is_empty`, `is_archived`, `is_mirror`, `status`, `is_fork`, `fork_id`, `is_template`, `template_id`, `size`, `is_fsck_enabled`, `close_issues_via_commit_in_any_branch`, `topics`, `avatar`, `created_unix`, `updated_unix` FROM `repository` ORDER BY updated_unix DESC LIMIT 15 OFFSET 45
Returns different results for MySQL than other engines. However, the similar query:
SELECT `id`, `owner_id`, `owner_name`, `lower_name`, `name`, `description`, `website`, `original_service_type`, `original_url`, `default_branch`, `num_watches`, `num_stars`, `num_forks`, `num_issues`, `num_closed_issues`, `num_pulls`, `num_closed_pulls`, `num_milestones`, `num_closed_milestones`, `is_private`, `is_empty`, `is_archived`, `is_mirror`, `status`, `is_fork`, `fork_id`, `is_template`, `template_id`, `size`, `is_fsck_enabled`, `close_issues_via_commit_in_any_branch`, `topics`, `avatar`, `created_unix`, `updated_unix` FROM `repository` ORDER BY updated_unix DESC LIMIT 15 OFFSET 30
Returns the same results.
This causes integration tests to fail on MySQL in certain cases but would never show up in a real installation. Since this API call always returns issues based on the optionally provided repo_priority_id or the issueID itself, there is no change to results by changing the repo sorting method used to get ids earlier in the function.
* linter is back!
* code review
* remove now unused option
* Fix newline at end of files
* more unused code
* update to master
* check for matching ids before query
* Update models/issue_label.go
Co-Authored-By: 6543 <6543@obermui.de>
* Update models/issue_label.go
* update comments
* Update routers/org/setting.go
Co-authored-by: Lauris BH <lauris@nix.lv>
Co-authored-by: guillep2k <18600385+guillep2k@users.noreply.github.com>
Co-authored-by: 6543 <6543@obermui.de>
2020-04-01 06:14:46 +02:00
|
|
|
})
|
|
|
|
|
|
2023-04-28 02:08:47 +02:00
|
|
|
m.Group("/actions", func() {
|
|
|
|
|
m.Get("", org_setting.RedirectToDefaultSetting)
|
|
|
|
|
addSettingsRunnersRoutes()
|
|
|
|
|
addSettingsSecretsRoutes()
|
2023-06-21 00:54:15 +02:00
|
|
|
addSettingVariablesRoutes()
|

Implement actions (#21937)
Close #13539.
Co-authored by: @lunny @appleboy @fuxiaohei and others.
Related projects:
- https://gitea.com/gitea/actions-proto-def
- https://gitea.com/gitea/actions-proto-go
- https://gitea.com/gitea/act
- https://gitea.com/gitea/act_runner
### Summary
The target of this PR is to bring a basic implementation of "Actions",
an internal CI/CD system of Gitea. That means even though it has been
merged, the state of the feature is **EXPERIMENTAL**, and please note
that:
- It is disabled by default;
- It shouldn't be used in a production environment currently;
- It shouldn't be used in a public Gitea instance currently;
- Breaking changes may be made before it's stable.
**Please comment on #13539 if you have any different product design
ideas**, all decisions reached there will be adopted here. But in this
PR, we don't talk about **naming, feature-creep or alternatives**.
### ⚠️ Breaking
`gitea-actions` will become a reserved user name. If a user with the
name already exists in the database, it is recommended to rename it.
### Some important reviews
- What is `DEFAULT_ACTIONS_URL` in `app.ini` for?
- https://github.com/go-gitea/gitea/pull/21937#discussion_r1055954954
- Why the api for runners is not under the normal `/api/v1` prefix?
- https://github.com/go-gitea/gitea/pull/21937#discussion_r1061173592
- Why DBFS?
- https://github.com/go-gitea/gitea/pull/21937#discussion_r1061301178
- Why ignore events triggered by `gitea-actions` bot?
- https://github.com/go-gitea/gitea/pull/21937#discussion_r1063254103
- Why there's no permission control for actions?
- https://github.com/go-gitea/gitea/pull/21937#discussion_r1090229868
### What it looks like
<details>
#### Manage runners
<img width="1792" alt="image"
src="https://user-images.githubusercontent.com/9418365/205870657-c72f590e-2e08-4cd4-be7f-2e0abb299bbf.png">
#### List runs
<img width="1792" alt="image"
src="https://user-images.githubusercontent.com/9418365/205872794-50fde990-2b45-48c1-a178-908e4ec5b627.png">
#### View logs
<img width="1792" alt="image"
src="https://user-images.githubusercontent.com/9418365/205872501-9b7b9000-9542-4991-8f55-18ccdada77c3.png">
</details>
### How to try it
<details>
#### 1. Start Gitea
Clone this branch and [install from
source](https://docs.gitea.io/en-us/install-from-source).
Add additional configurations in `app.ini` to enable Actions:
```ini
[actions]
ENABLED = true
```
Start it.
If all is well, you'll see the management page of runners:
<img width="1792" alt="image"
src="https://user-images.githubusercontent.com/9418365/205877365-8e30a780-9b10-4154-b3e8-ee6c3cb35a59.png">
#### 2. Start runner
Clone the [act_runner](https://gitea.com/gitea/act_runner), and follow
the
[README](https://gitea.com/gitea/act_runner/src/branch/main/README.md)
to start it.
If all is well, you'll see a new runner has been added:
<img width="1792" alt="image"
src="https://user-images.githubusercontent.com/9418365/205878000-216f5937-e696-470d-b66c-8473987d91c3.png">
#### 3. Enable actions for a repo
Create a new repo or open an existing one, check the `Actions` checkbox
in settings and submit.
<img width="1792" alt="image"
src="https://user-images.githubusercontent.com/9418365/205879705-53e09208-73c0-4b3e-a123-2dcf9aba4b9c.png">
<img width="1792" alt="image"
src="https://user-images.githubusercontent.com/9418365/205879383-23f3d08f-1a85-41dd-a8b3-54e2ee6453e8.png">
If all is well, you'll see a new tab "Actions":
<img width="1792" alt="image"
src="https://user-images.githubusercontent.com/9418365/205881648-a8072d8c-5803-4d76-b8a8-9b2fb49516c1.png">
#### 4. Upload workflow files
Upload some workflow files to `.gitea/workflows/xxx.yaml`, you can
follow the [quickstart](https://docs.github.com/en/actions/quickstart)
of GitHub Actions. Yes, Gitea Actions is compatible with GitHub Actions
in most cases, you can use the same demo:
```yaml
name: GitHub Actions Demo
run-name: ${{ github.actor }} is testing out GitHub Actions 🚀
on: [push]
jobs:
Explore-GitHub-Actions:
runs-on: ubuntu-latest
steps:
- run: echo "🎉 The job was automatically triggered by a ${{ github.event_name }} event."
- run: echo "🐧 This job is now running on a ${{ runner.os }} server hosted by GitHub!"
- run: echo "🔎 The name of your branch is ${{ github.ref }} and your repository is ${{ github.repository }}."
- name: Check out repository code
uses: actions/checkout@v3
- run: echo "💡 The ${{ github.repository }} repository has been cloned to the runner."
- run: echo "🖥️ The workflow is now ready to test your code on the runner."
- name: List files in the repository
run: |
ls ${{ github.workspace }}
- run: echo "🍏 This job's status is ${{ job.status }}."
```
If all is well, you'll see a new run in `Actions` tab:
<img width="1792" alt="image"
src="https://user-images.githubusercontent.com/9418365/205884473-79a874bc-171b-4aaf-acd5-0241a45c3b53.png">
#### 5. Check the logs of jobs
Click a run and you'll see the logs:
<img width="1792" alt="image"
src="https://user-images.githubusercontent.com/9418365/205884800-994b0374-67f7-48ff-be9a-4c53f3141547.png">
#### 6. Go on
You can try more examples in [the
documents](https://docs.github.com/en/actions/using-workflows/workflow-syntax-for-github-actions)
of GitHub Actions, then you might find a lot of bugs.
Come on, PRs are welcome.
</details>
See also: [Feature Preview: Gitea
Actions](https://blog.gitea.io/2022/12/feature-preview-gitea-actions/)
---------
Co-authored-by: a1012112796 <1012112796@qq.com>
Co-authored-by: Lunny Xiao <xiaolunwen@gmail.com>
Co-authored-by: delvh <dev.lh@web.de>
Co-authored-by: ChristopherHX <christopher.homberger@web.de>
Co-authored-by: John Olheiser <john.olheiser@gmail.com>
2023-01-31 02:45:19 +01:00
|
|
|
}, actions.MustEnableActions)
|
|
|
|
|
|
2023-07-21 00:43:49 +02:00
|
|
|
m.Methods("GET,POST", "/delete", org.SettingsDelete)
|
2022-11-20 15:08:38 +01:00
|
|
|
|
|
|
|
|
m.Group("/packages", func() {
|
|
|
|
|
m.Get("", org.Packages)
|
|
|
|
|
m.Group("/rules", func() {
|
|
|
|
|
m.Group("/add", func() {
|
|
|
|
|
m.Get("", org.PackagesRuleAdd)
|
2022-12-12 09:09:26 +01:00
|
|
|
m.Post("", web.Bind(forms.PackageCleanupRuleForm{}), org.PackagesRuleAddPost)
|
2022-11-20 15:08:38 +01:00
|
|
|
})
|
|
|
|
|
m.Group("/{id}", func() {
|
|
|
|
|
m.Get("", org.PackagesRuleEdit)
|
2022-12-12 09:09:26 +01:00
|
|
|
m.Post("", web.Bind(forms.PackageCleanupRuleForm{}), org.PackagesRuleEditPost)
|
2022-11-20 15:08:38 +01:00
|
|
|
m.Get("/preview", org.PackagesRulePreview)
|
|
|
|
|
})
|
|
|
|
|
})
|
2023-02-05 11:12:31 +01:00
|
|
|
m.Group("/cargo", func() {
|
|
|
|
|
m.Post("/initialize", org.InitializeCargoIndex)
|
|
|
|
|
m.Post("/rebuild", org.RebuildCargoIndex)
|
|
|
|
|
})
|
2022-11-20 15:08:38 +01:00
|
|
|
}, packagesEnabled)
|
2023-04-28 02:08:47 +02:00
|
|
|
}, ctxDataSet("EnableOAuth2", setting.OAuth2.Enable, "EnablePackages", setting.Packages.Enabled, "PageIsOrgSettings", true))
|
2017-04-25 09:24:51 +02:00
|
|
|
}, context.OrgAssignment(true, true))
|
|
|
|
|
}, reqSignIn)
|
|
|
|
|
// ***** END: Organization *****
|
|
|
|
|
|
|
|
|
|
// ***** START: Repository *****
|
|
|
|
|
m.Group("/repo", func() {
|
|
|
|
|
m.Get("/create", repo.Create)
|
2022-12-12 09:09:26 +01:00
|
|
|
m.Post("/create", web.Bind(forms.CreateRepoForm{}), repo.CreatePost)
|
2017-04-25 09:24:51 +02:00
|
|
|
m.Get("/migrate", repo.Migrate)
|
2022-12-12 09:09:26 +01:00
|
|
|
m.Post("/migrate", web.Bind(forms.MigrateRepoForm{}), repo.MigratePost)
|
2017-09-18 16:52:20 +02:00
|
|
|
m.Group("/fork", func() {
|
2021-01-26 16:36:53 +01:00
|
|
|
m.Combo("/{repoid}").Get(repo.Fork).
|
2022-12-12 09:09:26 +01:00
|
|
|
Post(web.Bind(forms.CreateRepoForm{}), repo.ForkPost)
|
2018-11-28 12:26:14 +01:00
|
|
|
}, context.RepoIDAssignment(), context.UnitTypes(), reqRepoCodeReader)
|
2022-04-07 20:59:56 +02:00
|
|
|
m.Get("/search", repo.SearchRepo)
|
2017-04-25 09:24:51 +02:00
|
|
|
}, reqSignIn)
|
|
|
|
|
|
2022-03-30 10:42:47 +02:00
|
|
|
m.Group("/{username}/-", func() {
|
2022-03-31 19:31:53 +02:00
|
|
|
if setting.Packages.Enabled {
|
|
|
|
|
m.Group("/packages", func() {
|
|
|
|
|
m.Get("", user.ListPackages)
|
|
|
|
|
m.Group("/{type}/{name}", func() {
|
|
|
|
|
m.Get("", user.RedirectToLastVersion)
|
|
|
|
|
m.Get("/versions", user.ListPackageVersions)
|
|
|
|
|
m.Group("/{version}", func() {
|
|
|
|
|
m.Get("", user.ViewPackageVersion)
|
|
|
|
|
m.Get("/files/{fileid}", user.DownloadPackageFile)
|
|
|
|
|
m.Group("/settings", func() {
|
|
|
|
|
m.Get("", user.PackageSettings)
|
2022-12-12 09:09:26 +01:00
|
|
|
m.Post("", web.Bind(forms.PackageSettingForm{}), user.PackageSettingsPost)
|
2022-03-31 19:31:53 +02:00
|
|
|
}, reqPackageAccess(perm.AccessModeWrite))
|
|
|
|
|
})
|
2022-03-30 10:42:47 +02:00
|
|
|
})
|
2023-05-04 14:07:15 +02:00
|
|
|
}, context.PackageAssignment(), reqPackageAccess(perm.AccessModeRead))
|
2022-03-31 19:31:53 +02:00
|
|
|
}
|
2023-01-20 12:42:33 +01:00
|
|
|
|
|
|
|
|
m.Group("/projects", func() {
|
2023-03-10 16:18:20 +01:00
|
|
|
m.Group("", func() {
|
|
|
|
|
m.Get("", org.Projects)
|
|
|
|
|
m.Get("/{id}", org.ViewProject)
|
2023-07-29 16:13:24 +02:00
|
|
|
}, reqUnitAccess(unit.TypeProjects, perm.AccessModeRead, true))
|
2023-01-20 12:42:33 +01:00
|
|
|
m.Group("", func() { //nolint:dupl
|
2023-05-31 08:50:18 +02:00
|
|
|
m.Get("/new", org.RenderNewProject)
|
2023-01-20 12:42:33 +01:00
|
|
|
m.Post("/new", web.Bind(forms.CreateProjectForm{}), org.NewProjectPost)
|
|
|
|
|
m.Group("/{id}", func() {
|
|
|
|
|
m.Post("", web.Bind(forms.EditProjectBoardForm{}), org.AddBoardToProjectPost)
|
|
|
|
|
m.Post("/delete", org.DeleteProject)
|
|
|
|
|
|
2023-05-31 08:50:18 +02:00
|
|
|
m.Get("/edit", org.RenderEditProject)
|
2023-01-20 12:42:33 +01:00
|
|
|
m.Post("/edit", web.Bind(forms.CreateProjectForm{}), org.EditProjectPost)
|
|
|
|
|
m.Post("/{action:open|close}", org.ChangeProjectStatus)
|
|
|
|
|
|
|
|
|
|
m.Group("/{boardID}", func() {
|
|
|
|
|
m.Put("", web.Bind(forms.EditProjectBoardForm{}), org.EditProjectBoard)
|
|
|
|
|
m.Delete("", org.DeleteProjectBoard)
|
|
|
|
|
m.Post("/default", org.SetDefaultProjectBoard)
|
2023-04-19 16:28:28 +02:00
|
|
|
m.Post("/unsetdefault", org.UnsetDefaultProjectBoard)
|
2023-01-20 12:42:33 +01:00
|
|
|
|
|
|
|
|
m.Post("/move", org.MoveIssues)
|
|
|
|
|
})
|
|
|
|
|
})
|
2023-07-29 16:13:24 +02:00
|
|
|
}, reqSignIn, reqUnitAccess(unit.TypeProjects, perm.AccessModeWrite, true), func(ctx *context.Context) {
|
2023-03-10 16:18:20 +01:00
|
|
|
if ctx.ContextUser.IsIndividual() && ctx.ContextUser.ID != ctx.Doer.ID {
|
2023-01-20 12:42:33 +01:00
|
|
|
ctx.NotFound("NewProject", nil)
|
|
|
|
|
return
|
|
|
|
|
}
|
|
|
|
|
})
|
2023-07-29 16:13:24 +02:00
|
|
|
})
|
2023-01-20 12:42:33 +01:00
|
|
|
|
2023-03-10 16:18:20 +01:00
|
|
|
m.Group("", func() {
|
|
|
|
|
m.Get("/code", user.CodeSearch)
|
2023-07-29 16:13:24 +02:00
|
|
|
}, reqUnitAccess(unit.TypeCode, perm.AccessModeRead, false))
|
2023-05-04 14:07:15 +02:00
|
|
|
}, ignSignIn, context_service.UserAssignmentWeb(), context.OrgAssignment()) // for "/{username}/-" (packages, projects, code)
|
2022-03-30 10:42:47 +02:00
|
|
|
|
2021-01-26 16:36:53 +01:00
|
|
|
m.Group("/{username}/{reponame}", func() {
|
2017-04-25 09:24:51 +02:00
|
|
|
m.Group("/settings", func() {
|
2022-06-12 07:43:27 +02:00
|
|
|
m.Group("", func() {
|
2023-07-02 02:59:32 +02:00
|
|
|
m.Combo("").Get(repo_setting.Settings).
|
|
|
|
|
Post(web.Bind(forms.RepoSettingForm{}), repo_setting.SettingsPost)
|
|
|
|
|
}, repo_setting.SettingsCtxData)
|
|
|
|
|
m.Post("/avatar", web.Bind(forms.AvatarForm{}), repo_setting.SettingsAvatar)
|
|
|
|
|
m.Post("/avatar/delete", repo_setting.SettingsDeleteAvatar)
|
2019-05-30 04:22:26 +02:00
|
|
|
|
2017-04-25 09:24:51 +02:00
|
|
|
m.Group("/collaboration", func() {
|
2023-07-02 02:59:32 +02:00
|
|
|
m.Combo("").Get(repo_setting.Collaboration).Post(repo_setting.CollaborationPost)
|
|
|
|
|
m.Post("/access_mode", repo_setting.ChangeCollaborationAccessMode)
|
|
|
|
|
m.Post("/delete", repo_setting.DeleteCollaboration)
|
2019-09-23 22:08:03 +02:00
|
|
|
m.Group("/team", func() {
|
2023-07-02 02:59:32 +02:00
|
|
|
m.Post("", repo_setting.AddTeamPost)
|
|
|
|
|
m.Post("/delete", repo_setting.DeleteTeam)
|
2019-09-23 22:08:03 +02:00
|
|
|
})
|
2017-04-25 09:24:51 +02:00
|
|
|
})
|
2021-06-25 16:28:55 +02:00
|
|
|
|
2017-04-25 09:24:51 +02:00
|
|
|
m.Group("/branches", func() {
|
2023-07-02 02:59:32 +02:00
|
|
|
m.Post("/", repo_setting.SetDefaultBranchPost)
|
2023-01-16 09:00:22 +01:00
|
|
|
}, repo.MustBeNotEmpty)
|
|
|
|
|
|
|
|
|
|
m.Group("/branches", func() {
|
2023-07-02 02:59:32 +02:00
|
|
|
m.Get("/", repo_setting.ProtectedBranchRules)
|
|
|
|
|
m.Combo("/edit").Get(repo_setting.SettingsProtectedBranch).
|
|
|
|
|
Post(web.Bind(forms.ProtectBranchForm{}), context.RepoMustNotBeArchived(), repo_setting.SettingsProtectedBranchPost)
|
|
|
|
|
m.Post("/{id}/delete", repo_setting.DeleteProtectedBranchRulePost)
|
2019-01-18 01:01:04 +01:00
|
|
|
}, repo.MustBeNotEmpty)
|
2023-01-16 09:00:22 +01:00
|
|
|
|
2023-07-02 02:59:32 +02:00
|
|
|
m.Post("/rename_branch", web.Bind(forms.RenameBranchForm{}), context.RepoMustNotBeArchived(), repo_setting.RenameBranchPost)
|
2017-04-25 09:24:51 +02:00
|
|
|
|
2021-06-25 16:28:55 +02:00
|
|
|
m.Group("/tags", func() {
|
2023-07-02 02:59:32 +02:00
|
|
|
m.Get("", repo_setting.ProtectedTags)
|
|
|
|
|
m.Post("", web.Bind(forms.ProtectTagForm{}), context.RepoMustNotBeArchived(), repo_setting.NewProtectedTagPost)
|
|
|
|
|
m.Post("/delete", context.RepoMustNotBeArchived(), repo_setting.DeleteProtectedTagPost)
|
|
|
|
|
m.Get("/{id}", repo_setting.EditProtectedTag)
|
|
|
|
|
m.Post("/{id}", web.Bind(forms.ProtectTagForm{}), context.RepoMustNotBeArchived(), repo_setting.EditProtectedTagPost)
|
2021-06-25 16:28:55 +02:00
|
|
|
})
|
|
|
|
|
|
2021-02-11 18:34:34 +01:00
|
|
|
m.Group("/hooks/git", func() {
|
2023-07-02 02:59:32 +02:00
|
|
|
m.Get("", repo_setting.GitHooks)
|
|
|
|
|
m.Combo("/{name}").Get(repo_setting.GitHooksEdit).
|
|
|
|
|
Post(repo_setting.GitHooksEditPost)
|
2021-02-11 18:34:34 +01:00
|
|
|
}, context.GitHookService())
|
|
|
|
|
|
2017-04-25 09:24:51 +02:00
|
|
|
m.Group("/hooks", func() {
|
2023-07-02 02:59:32 +02:00
|
|
|
m.Get("", repo_setting.Webhooks)
|
|
|
|
|
m.Post("/delete", repo_setting.DeleteWebhook)
|
2023-03-10 15:28:32 +01:00
|
|
|
addWebhookAddRoutes()
|
2022-01-05 22:00:20 +01:00
|
|
|
m.Group("/{id}", func() {
|
2023-07-02 02:59:32 +02:00
|
|
|
m.Get("", repo_setting.WebHooksEdit)
|
|
|
|
|
m.Post("/test", repo_setting.TestWebhook)
|
|
|
|
|
m.Post("/replay/{uuid}", repo_setting.ReplayWebhook)
|
2022-01-05 22:00:20 +01:00
|
|
|
})
|
2023-03-10 15:28:32 +01:00
|
|
|
addWebhookEditRoutes()
|
2023-04-28 02:08:47 +02:00
|
|
|
}, webhooksEnabled)
|
2017-04-25 09:24:51 +02:00
|
|
|
|
|
|
|
|
m.Group("/keys", func() {
|
2023-07-02 02:59:32 +02:00
|
|
|
m.Combo("").Get(repo_setting.DeployKeys).
|
|
|
|
|
Post(web.Bind(forms.AddKeyForm{}), repo_setting.DeployKeysPost)
|
|
|
|
|
m.Post("/delete", repo_setting.DeleteDeployKey)
|
2023-02-01 13:53:04 +01:00
|
|
|
})
|
|
|
|
|
|
2019-10-28 19:31:55 +01:00
|
|
|
m.Group("/lfs", func() {
|
2023-07-02 02:59:32 +02:00
|
|
|
m.Get("/", repo_setting.LFSFiles)
|
|
|
|
|
m.Get("/show/{oid}", repo_setting.LFSFileGet)
|
|
|
|
|
m.Post("/delete/{oid}", repo_setting.LFSDelete)
|
|
|
|
|
m.Get("/pointers", repo_setting.LFSPointerFiles)
|
|
|
|
|
m.Post("/pointers/associate", repo_setting.LFSAutoAssociate)
|
|
|
|
|
m.Get("/find", repo_setting.LFSFileFind)
|
2019-12-12 14:18:07 +01:00
|
|
|
m.Group("/locks", func() {
|
2023-07-02 02:59:32 +02:00
|
|
|
m.Get("/", repo_setting.LFSLocks)
|
|
|
|
|
m.Post("/", repo_setting.LFSLockFile)
|
|
|
|
|
m.Post("/{lid}/unlock", repo_setting.LFSUnlock)
|
2019-12-12 14:18:07 +01:00
|
|
|
})
|
2019-10-28 19:31:55 +01:00
|
|
|
})
|
2023-04-28 02:08:47 +02:00
|
|
|
m.Group("/actions", func() {
|
|
|
|
|
m.Get("", repo_setting.RedirectToDefaultSetting)
|
|
|
|
|
addSettingsRunnersRoutes()
|
|
|
|
|
addSettingsSecretsRoutes()
|
2023-06-21 00:54:15 +02:00
|
|
|
addSettingVariablesRoutes()
|

Implement actions (#21937)
Close #13539.
Co-authored by: @lunny @appleboy @fuxiaohei and others.
Related projects:
- https://gitea.com/gitea/actions-proto-def
- https://gitea.com/gitea/actions-proto-go
- https://gitea.com/gitea/act
- https://gitea.com/gitea/act_runner
### Summary
The target of this PR is to bring a basic implementation of "Actions",
an internal CI/CD system of Gitea. That means even though it has been
merged, the state of the feature is **EXPERIMENTAL**, and please note
that:
- It is disabled by default;
- It shouldn't be used in a production environment currently;
- It shouldn't be used in a public Gitea instance currently;
- Breaking changes may be made before it's stable.
**Please comment on #13539 if you have any different product design
ideas**, all decisions reached there will be adopted here. But in this
PR, we don't talk about **naming, feature-creep or alternatives**.
### ⚠️ Breaking
`gitea-actions` will become a reserved user name. If a user with the
name already exists in the database, it is recommended to rename it.
### Some important reviews
- What is `DEFAULT_ACTIONS_URL` in `app.ini` for?
- https://github.com/go-gitea/gitea/pull/21937#discussion_r1055954954
- Why the api for runners is not under the normal `/api/v1` prefix?
- https://github.com/go-gitea/gitea/pull/21937#discussion_r1061173592
- Why DBFS?
- https://github.com/go-gitea/gitea/pull/21937#discussion_r1061301178
- Why ignore events triggered by `gitea-actions` bot?
- https://github.com/go-gitea/gitea/pull/21937#discussion_r1063254103
- Why there's no permission control for actions?
- https://github.com/go-gitea/gitea/pull/21937#discussion_r1090229868
### What it looks like
<details>
#### Manage runners
<img width="1792" alt="image"
src="https://user-images.githubusercontent.com/9418365/205870657-c72f590e-2e08-4cd4-be7f-2e0abb299bbf.png">
#### List runs
<img width="1792" alt="image"
src="https://user-images.githubusercontent.com/9418365/205872794-50fde990-2b45-48c1-a178-908e4ec5b627.png">
#### View logs
<img width="1792" alt="image"
src="https://user-images.githubusercontent.com/9418365/205872501-9b7b9000-9542-4991-8f55-18ccdada77c3.png">
</details>
### How to try it
<details>
#### 1. Start Gitea
Clone this branch and [install from
source](https://docs.gitea.io/en-us/install-from-source).
Add additional configurations in `app.ini` to enable Actions:
```ini
[actions]
ENABLED = true
```
Start it.
If all is well, you'll see the management page of runners:
<img width="1792" alt="image"
src="https://user-images.githubusercontent.com/9418365/205877365-8e30a780-9b10-4154-b3e8-ee6c3cb35a59.png">
#### 2. Start runner
Clone the [act_runner](https://gitea.com/gitea/act_runner), and follow
the
[README](https://gitea.com/gitea/act_runner/src/branch/main/README.md)
to start it.
If all is well, you'll see a new runner has been added:
<img width="1792" alt="image"
src="https://user-images.githubusercontent.com/9418365/205878000-216f5937-e696-470d-b66c-8473987d91c3.png">
#### 3. Enable actions for a repo
Create a new repo or open an existing one, check the `Actions` checkbox
in settings and submit.
<img width="1792" alt="image"
src="https://user-images.githubusercontent.com/9418365/205879705-53e09208-73c0-4b3e-a123-2dcf9aba4b9c.png">
<img width="1792" alt="image"
src="https://user-images.githubusercontent.com/9418365/205879383-23f3d08f-1a85-41dd-a8b3-54e2ee6453e8.png">
If all is well, you'll see a new tab "Actions":
<img width="1792" alt="image"
src="https://user-images.githubusercontent.com/9418365/205881648-a8072d8c-5803-4d76-b8a8-9b2fb49516c1.png">
#### 4. Upload workflow files
Upload some workflow files to `.gitea/workflows/xxx.yaml`, you can
follow the [quickstart](https://docs.github.com/en/actions/quickstart)
of GitHub Actions. Yes, Gitea Actions is compatible with GitHub Actions
in most cases, you can use the same demo:
```yaml
name: GitHub Actions Demo
run-name: ${{ github.actor }} is testing out GitHub Actions 🚀
on: [push]
jobs:
Explore-GitHub-Actions:
runs-on: ubuntu-latest
steps:
- run: echo "🎉 The job was automatically triggered by a ${{ github.event_name }} event."
- run: echo "🐧 This job is now running on a ${{ runner.os }} server hosted by GitHub!"
- run: echo "🔎 The name of your branch is ${{ github.ref }} and your repository is ${{ github.repository }}."
- name: Check out repository code
uses: actions/checkout@v3
- run: echo "💡 The ${{ github.repository }} repository has been cloned to the runner."
- run: echo "🖥️ The workflow is now ready to test your code on the runner."
- name: List files in the repository
run: |
ls ${{ github.workspace }}
- run: echo "🍏 This job's status is ${{ job.status }}."
```
If all is well, you'll see a new run in `Actions` tab:
<img width="1792" alt="image"
src="https://user-images.githubusercontent.com/9418365/205884473-79a874bc-171b-4aaf-acd5-0241a45c3b53.png">
#### 5. Check the logs of jobs
Click a run and you'll see the logs:
<img width="1792" alt="image"
src="https://user-images.githubusercontent.com/9418365/205884800-994b0374-67f7-48ff-be9a-4c53f3141547.png">
#### 6. Go on
You can try more examples in [the
documents](https://docs.github.com/en/actions/using-workflows/workflow-syntax-for-github-actions)
of GitHub Actions, then you might find a lot of bugs.
Come on, PRs are welcome.
</details>
See also: [Feature Preview: Gitea
Actions](https://blog.gitea.io/2022/12/feature-preview-gitea-actions/)
---------
Co-authored-by: a1012112796 <1012112796@qq.com>
Co-authored-by: Lunny Xiao <xiaolunwen@gmail.com>
Co-authored-by: delvh <dev.lh@web.de>
Co-authored-by: ChristopherHX <christopher.homberger@web.de>
Co-authored-by: John Olheiser <john.olheiser@gmail.com>
2023-01-31 02:45:19 +01:00
|
|
|
}, actions.MustEnableActions)
|
2023-08-04 04:21:32 +02:00
|
|
|
// the follow handler must be under "settings", otherwise this incomplete repo can't be accessed
|
|
|
|
|
m.Group("/migrate", func() {
|
|
|
|
|
m.Post("/retry", repo.MigrateRetryPost)
|
|
|
|
|
m.Post("/cancel", repo.MigrateCancelPost)
|
|
|
|
|
})
|
2023-04-28 02:08:47 +02:00
|
|
|
}, ctxDataSet("PageIsRepoSettings", true, "LFSStartServer", setting.LFS.StartServer))
|
2021-04-10 02:26:08 +02:00
|
|
|
}, reqSignIn, context.RepoAssignment, context.UnitTypes(), reqRepoAdmin, context.RepoRef())
|
2017-04-25 09:24:51 +02:00
|
|
|
|
2021-04-10 02:26:08 +02:00
|
|
|
m.Post("/{username}/{reponame}/action/{action}", reqSignIn, context.RepoAssignment, context.UnitTypes(), repo.Action)
|
2017-05-18 16:54:24 +02:00
|
|
|
|
2023-05-04 14:07:15 +02:00
|
|
|
// Grouping for those endpoints not requiring authentication (but should respect ignSignIn)
|
2021-01-26 16:36:53 +01:00
|
|
|
m.Group("/{username}/{reponame}", func() {
|
2020-05-03 11:07:04 +02:00
|
|
|
m.Group("/milestone", func() {
|
2021-01-26 16:36:53 +01:00
|
|
|
m.Get("/{id}", repo.MilestoneIssuesAndPulls)
|
2020-05-03 11:07:04 +02:00
|
|
|
}, reqRepoIssuesOrPullsReader, context.RepoRef())
|
2022-06-09 13:15:08 +02:00
|
|
|
m.Get("/find/*", repo.FindFiles)
|
|
|
|
|
m.Group("/tree-list", func() {
|
|
|
|
|
m.Get("/branch/*", context.RepoRefByType(context.RepoRefBranch), repo.TreeList)
|
|
|
|
|
m.Get("/tag/*", context.RepoRefByType(context.RepoRefTag), repo.TreeList)
|
|
|
|
|
m.Get("/commit/*", context.RepoRefByType(context.RepoRefCommit), repo.TreeList)
|
|
|
|
|
})
|
2021-12-17 23:20:27 +01:00
|
|
|
m.Get("/compare", repo.MustBeNotEmpty, reqRepoCodeReader, repo.SetEditorconfigIfExists, ignSignIn, repo.SetDiffViewStyle, repo.SetWhitespaceBehavior, repo.CompareDiff)
|
2020-05-05 00:44:30 +02:00
|
|
|
m.Combo("/compare/*", repo.MustBeNotEmpty, reqRepoCodeReader, repo.SetEditorconfigIfExists).
|
2023-05-04 14:07:15 +02:00
|
|
|
Get(repo.SetDiffViewStyle, repo.SetWhitespaceBehavior, repo.CompareDiff).
|
2022-12-12 09:09:26 +01:00
|
|
|
Post(reqSignIn, context.RepoMustNotBeArchived(), reqRepoPullsReader, repo.MustAllowPulls, web.Bind(forms.CreateIssueForm{}), repo.SetWhitespaceBehavior, repo.CompareAndPullRequestPost)
|
2022-06-04 22:10:54 +02:00
|
|
|
m.Group("/{type:issues|pulls}", func() {
|
|
|
|
|
m.Group("/{index}", func() {
|
|
|
|
|
m.Get("/info", repo.GetIssueInfo)
|
|
|
|
|
})
|
|
|
|
|
})
|
2023-05-04 14:07:15 +02:00
|
|
|
}, ignSignIn, context.RepoAssignment, context.UnitTypes()) // for "/{username}/{reponame}" which doesn't require authentication
|
2020-05-03 11:07:04 +02:00
|
|
|
|
|
|
|
|
// Grouping for those endpoints that do require authentication
|
2021-01-26 16:36:53 +01:00
|
|
|
m.Group("/{username}/{reponame}", func() {
|
2017-04-25 09:24:51 +02:00
|
|
|
m.Group("/issues", func() {
|
2020-09-11 16:48:39 +02:00
|
|
|
m.Group("/new", func() {
|
|
|
|
|
m.Combo("").Get(context.RepoRef(), repo.NewIssue).
|
2022-12-12 09:09:26 +01:00
|
|
|
Post(web.Bind(forms.CreateIssueForm{}), repo.NewIssuePost)
|
2020-09-11 16:48:39 +02:00
|
|
|
m.Get("/choose", context.RepoRef(), repo.NewIssueChooseTemplate)
|
|
|
|
|
})
|
2022-04-07 20:59:56 +02:00
|
|
|
m.Get("/search", repo.ListIssues)
|
2019-01-23 19:58:38 +01:00
|
|
|
}, context.RepoMustNotBeArchived(), reqRepoIssueReader)
|
2021-02-18 15:47:23 +01:00
|
|
|
// FIXME: should use different URLs but mostly same logic for comments of issue and pull request.
|
2017-10-16 09:55:43 +02:00
|
|
|
// So they can apply their own enable/disable logic on routers.
|
2021-12-16 20:01:14 +01:00
|
|
|
m.Group("/{type:issues|pulls}", func() {
|
2021-01-26 16:36:53 +01:00
|
|
|
m.Group("/{index}", func() {
|
2017-04-25 09:24:51 +02:00
|
|
|
m.Post("/title", repo.UpdateIssueTitle)
|
|
|
|
|
m.Post("/content", repo.UpdateIssueContent)
|
2022-12-12 09:09:26 +01:00
|
|
|
m.Post("/deadline", web.Bind(structs.EditDeadlineOption{}), repo.UpdateIssueDeadline)
|
2017-04-25 09:24:51 +02:00
|
|
|
m.Post("/watch", repo.IssueWatch)
|
2020-09-08 18:29:51 +02:00
|
|
|
m.Post("/ref", repo.UpdateIssueRef)
|
2023-05-25 15:17:19 +02:00
|
|
|
m.Post("/pin", reqRepoAdmin, repo.IssuePinOrUnpin)
|
2022-05-07 20:28:10 +02:00
|
|
|
m.Post("/viewed-files", repo.UpdateViewedFiles)
|
2018-07-17 23:23:58 +02:00
|
|
|
m.Group("/dependency", func() {
|
|
|
|
|
m.Post("/add", repo.AddDependency)
|
|
|
|
|
m.Post("/delete", repo.RemoveDependency)
|
|
|
|
|
})
|
2022-12-12 09:09:26 +01:00
|
|
|
m.Combo("/comments").Post(repo.MustAllowUserComment, web.Bind(forms.CreateCommentForm{}), repo.NewComment)
|
2017-09-12 08:48:13 +02:00
|
|
|
m.Group("/times", func() {
|
2022-12-12 09:09:26 +01:00
|
|
|
m.Post("/add", web.Bind(forms.AddTimeManuallyForm{}), repo.AddTimeManually)
|
2021-02-19 11:52:11 +01:00
|
|
|
m.Post("/{timeid}/delete", repo.DeleteTime)
|
2017-09-12 08:48:13 +02:00
|
|
|
m.Group("/stopwatch", func() {
|
|
|
|
|
m.Post("/toggle", repo.IssueStopwatch)
|
|
|
|
|
m.Post("/cancel", repo.CancelStopwatch)
|
|
|
|
|
})
|
|
|
|
|
})
|
2022-12-12 09:09:26 +01:00
|
|
|
m.Post("/reactions/{action}", web.Bind(forms.ReactionForm{}), repo.ChangeIssueReaction)
|
2022-12-12 16:02:51 +01:00
|
|
|
m.Post("/lock", reqRepoIssuesOrPullsWriter, web.Bind(forms.IssueLockForm{}), repo.LockIssue)
|
|
|
|
|
m.Post("/unlock", reqRepoIssuesOrPullsWriter, repo.UnlockIssue)
|
2022-03-09 01:38:11 +01:00
|
|
|
m.Post("/delete", reqRepoAdmin, repo.DeleteIssue)
|
2019-01-23 19:58:38 +01:00
|
|
|
}, context.RepoMustNotBeArchived())
|
2021-01-26 16:36:53 +01:00
|
|
|
m.Group("/{index}", func() {
|
2020-10-05 07:49:33 +02:00
|
|
|
m.Get("/attachments", repo.GetIssueAttachments)
|
2021-01-26 16:36:53 +01:00
|
|
|
m.Get("/attachments/{uuid}", repo.GetAttachment)
|
2020-10-05 07:49:33 +02:00
|
|
|
})
|
2021-10-11 00:40:03 +02:00
|
|
|
m.Group("/{index}", func() {
|
|
|
|
|
m.Post("/content-history/soft-delete", repo.SoftDeleteContentHistory)
|
|
|
|
|
})
|
2017-04-25 09:24:51 +02:00
|
|
|
|
2018-11-28 12:26:14 +01:00
|
|
|
m.Post("/labels", reqRepoIssuesOrPullsWriter, repo.UpdateIssueLabel)
|
|
|
|
|
m.Post("/milestone", reqRepoIssuesOrPullsWriter, repo.UpdateIssueMilestone)
|
2022-06-30 17:55:08 +02:00
|
|
|
m.Post("/projects", reqRepoIssuesOrPullsWriter, reqRepoProjectsReader, repo.UpdateIssueProject)
|
2018-11-28 12:26:14 +01:00
|
|
|
m.Post("/assignee", reqRepoIssuesOrPullsWriter, repo.UpdateIssueAssignee)
|
2020-04-06 18:33:34 +02:00
|
|
|
m.Post("/request_review", reqRepoIssuesOrPullsReader, repo.UpdatePullReviewRequest)
|
2022-12-12 09:09:26 +01:00
|
|
|
m.Post("/dismiss_review", reqRepoAdmin, web.Bind(forms.DismissReviewForm{}), repo.DismissReview)
|
2018-11-28 12:26:14 +01:00
|
|
|
m.Post("/status", reqRepoIssuesOrPullsWriter, repo.UpdateIssueStatus)
|
2023-06-19 09:46:50 +02:00
|
|
|
m.Post("/delete", reqRepoAdmin, repo.BatchDeleteIssues)
|
2023-06-21 18:08:12 +02:00
|
|
|
m.Post("/resolve_conversation", reqRepoIssuesOrPullsReader, repo.SetShowOutdatedComments, repo.UpdateResolveConversation)
|
2020-10-05 07:49:33 +02:00
|
|
|
m.Post("/attachments", repo.UploadIssueAttachment)
|
|
|
|
|
m.Post("/attachments/remove", repo.DeleteAttachment)
|
2023-05-30 17:26:51 +02:00
|
|
|
m.Delete("/unpin/{index}", reqRepoAdmin, repo.IssueUnpin)
|
|
|
|
|
m.Post("/move_pin", reqRepoAdmin, repo.IssuePinMove)
|
2019-01-23 19:58:38 +01:00
|
|
|
}, context.RepoMustNotBeArchived())
|
2021-01-26 16:36:53 +01:00
|
|
|
m.Group("/comments/{id}", func() {
|
2017-04-25 09:24:51 +02:00
|
|
|
m.Post("", repo.UpdateCommentContent)
|
|
|
|
|
m.Post("/delete", repo.DeleteComment)
|
2022-12-12 09:09:26 +01:00
|
|
|
m.Post("/reactions/{action}", web.Bind(forms.ReactionForm{}), repo.ChangeCommentReaction)
|
2019-01-23 19:58:38 +01:00
|
|
|
}, context.RepoMustNotBeArchived())
|
2021-01-26 16:36:53 +01:00
|
|
|
m.Group("/comments/{id}", func() {
|
2020-10-05 07:49:33 +02:00
|
|
|
m.Get("/attachments", repo.GetCommentAttachments)
|
|
|
|
|
})
|
2023-03-24 07:12:23 +01:00
|
|
|
m.Post("/markup", web.Bind(structs.MarkupOption{}), misc.Markup)
|
2017-04-25 09:24:51 +02:00
|
|
|
m.Group("/labels", func() {
|
2022-12-12 09:09:26 +01:00
|
|
|
m.Post("/new", web.Bind(forms.CreateLabelForm{}), repo.NewLabel)
|
|
|
|
|
m.Post("/edit", web.Bind(forms.CreateLabelForm{}), repo.UpdateLabel)
|
2017-04-25 09:24:51 +02:00
|
|
|
m.Post("/delete", repo.DeleteLabel)
|
2022-12-12 09:09:26 +01:00
|
|
|
m.Post("/initialize", web.Bind(forms.InitializeLabelsForm{}), repo.InitializeLabels)
|
2019-01-23 19:58:38 +01:00
|
|
|
}, context.RepoMustNotBeArchived(), reqRepoIssuesOrPullsWriter, context.RepoRef())
|
2017-04-25 09:24:51 +02:00
|
|
|
m.Group("/milestones", func() {
|
|
|
|
|
m.Combo("/new").Get(repo.NewMilestone).
|
2022-12-12 09:09:26 +01:00
|
|
|
Post(web.Bind(forms.CreateMilestoneForm{}), repo.NewMilestonePost)
|
2021-01-26 16:36:53 +01:00
|
|
|
m.Get("/{id}/edit", repo.EditMilestone)
|
2022-12-12 09:09:26 +01:00
|
|
|
m.Post("/{id}/edit", web.Bind(forms.CreateMilestoneForm{}), repo.EditMilestonePost)
|
2021-01-26 16:36:53 +01:00
|
|
|
m.Post("/{id}/{action}", repo.ChangeMilestoneStatus)
|
2017-04-25 09:24:51 +02:00
|
|
|
m.Post("/delete", repo.DeleteMilestone)
|
2019-01-23 19:58:38 +01:00
|
|
|
}, context.RepoMustNotBeArchived(), reqRepoIssuesOrPullsWriter, context.RepoRef())
|
2019-12-16 07:20:25 +01:00
|
|
|
m.Group("/pull", func() {
|
2021-01-26 16:36:53 +01:00
|
|
|
m.Post("/{index}/target_branch", repo.UpdatePullRequestTarget)
|
2019-12-16 07:20:25 +01:00
|
|
|
}, context.RepoMustNotBeArchived())
|
2017-04-25 09:24:51 +02:00
|
|
|
|
|
|
|
|
m.Group("", func() {
|
|
|
|
|
m.Group("", func() {
|
2017-10-30 03:04:25 +01:00
|
|
|
m.Combo("/_edit/*").Get(repo.EditFile).
|
2022-12-12 09:09:26 +01:00
|
|
|
Post(web.Bind(forms.EditRepoFileForm{}), repo.EditFilePost)
|
2017-10-30 03:04:25 +01:00
|
|
|
m.Combo("/_new/*").Get(repo.NewFile).
|
2022-12-12 09:09:26 +01:00
|
|
|
Post(web.Bind(forms.EditRepoFileForm{}), repo.NewFilePost)
|
|
|
|
|
m.Post("/_preview/*", web.Bind(forms.EditPreviewDiffForm{}), repo.DiffPreviewPost)
|
2017-10-30 03:04:25 +01:00
|
|
|
m.Combo("/_delete/*").Get(repo.DeleteFile).
|
2022-12-12 09:09:26 +01:00
|
|
|
Post(web.Bind(forms.DeleteRepoFileForm{}), repo.DeleteFilePost)
|
2017-10-30 03:04:25 +01:00
|
|
|
m.Combo("/_upload/*", repo.MustBeAbleToUpload).
|
|
|
|
|
Get(repo.UploadFile).
|
2022-12-12 09:09:26 +01:00
|
|
|
Post(web.Bind(forms.UploadRepoFileForm{}), repo.UploadFilePost)
|
2022-02-09 21:28:55 +01:00
|
|
|
m.Combo("/_diffpatch/*").Get(repo.NewDiffPatch).
|
2022-12-12 09:09:26 +01:00
|
|
|
Post(web.Bind(forms.EditRepoFileForm{}), repo.NewDiffPatchPost)
|
2022-02-09 21:28:55 +01:00
|
|
|
m.Combo("/_cherrypick/{sha:([a-f0-9]{7,40})}/*").Get(repo.CherryPick).
|
2022-12-12 09:09:26 +01:00
|
|
|
Post(web.Bind(forms.CherryPickForm{}), repo.CherryPickPost)
|
2022-04-28 17:45:33 +02:00
|
|
|
}, repo.MustBeEditable)
|
2017-10-30 03:04:25 +01:00
|
|
|
m.Group("", func() {
|
2017-04-25 09:24:51 +02:00
|
|
|
m.Post("/upload-file", repo.UploadFileToServer)
|
2022-12-12 09:09:26 +01:00
|
|
|
m.Post("/upload-remove", web.Bind(forms.RemoveUploadFileForm{}), repo.RemoveUploadFileFromServer)
|
2022-04-28 17:45:33 +02:00
|
|
|
}, repo.MustBeEditable, repo.MustBeAbleToUpload)
|
2023-04-19 15:40:42 +02:00
|
|
|
}, context.RepoRef(), canEnableEditor, context.RepoMustNotBeArchived())
|
2017-10-15 21:59:24 +02:00
|
|
|
|
|
|
|
|
m.Group("/branches", func() {
|
2021-01-26 16:36:53 +01:00
|
|
|
m.Group("/_new", func() {
|
2017-10-30 03:04:25 +01:00
|
|
|
m.Post("/branch/*", context.RepoRefByType(context.RepoRefBranch), repo.CreateBranch)
|
|
|
|
|
m.Post("/tag/*", context.RepoRefByType(context.RepoRefTag), repo.CreateBranch)
|
|
|
|
|
m.Post("/commit/*", context.RepoRefByType(context.RepoRefCommit), repo.CreateBranch)
|
2022-12-12 09:09:26 +01:00
|
|
|
}, web.Bind(forms.NewBranchForm{}))
|
2017-10-26 02:49:16 +02:00
|
|
|
m.Post("/delete", repo.DeleteBranchPost)
|
|
|
|
|
m.Post("/restore", repo.RestoreBranchPost)
|
2019-01-23 19:58:38 +01:00
|
|
|
}, context.RepoMustNotBeArchived(), reqRepoCodeWriter, repo.MustBeNotEmpty)
|
2021-04-10 02:26:08 +02:00
|
|
|
}, reqSignIn, context.RepoAssignment, context.UnitTypes())
|
2017-05-18 16:54:24 +02:00
|
|
|
|
2023-04-25 18:29:00 +02:00
|
|
|
// Tags
|
2021-01-26 16:36:53 +01:00
|
|
|
m.Group("/{username}/{reponame}", func() {
|
2022-12-21 22:06:26 +01:00
|
|
|
m.Group("/tags", func() {
|
|
|
|
|
m.Get("", repo.TagsList)
|
2023-07-21 13:20:04 +02:00
|
|
|
m.Get("/list", repo.GetTagList)
|
2022-12-21 22:06:26 +01:00
|
|
|
m.Get(".rss", feedEnabled, repo.TagsListFeedRSS)
|
|
|
|
|
m.Get(".atom", feedEnabled, repo.TagsListFeedAtom)
|
2023-04-28 02:08:47 +02:00
|
|
|
}, ctxDataSet("EnableFeed", setting.Other.EnableFeed),
|
|
|
|
|
repo.MustBeNotEmpty, reqRepoCodeReader, context.RepoRefByType(context.RepoRefTag, true))
|
2023-04-25 18:29:00 +02:00
|
|
|
m.Post("/tags/delete", repo.DeleteTag, reqSignIn,
|
|
|
|
|
repo.MustBeNotEmpty, context.RepoMustNotBeArchived(), reqRepoCodeWriter, context.RepoRef())
|
2023-04-29 06:40:55 +02:00
|
|
|
}, ignSignIn, context.RepoAssignment, context.UnitTypes())
|
2023-04-25 18:29:00 +02:00
|
|
|
|
|
|
|
|
// Releases
|
|
|
|
|
m.Group("/{username}/{reponame}", func() {
|
2017-05-18 16:54:24 +02:00
|
|
|
m.Group("/releases", func() {
|
2020-04-18 16:47:15 +02:00
|
|
|
m.Get("/", repo.Releases)
|
2020-09-17 20:24:23 +02:00
|
|
|
m.Get("/tag/*", repo.SingleRelease)
|
2020-04-18 16:47:15 +02:00
|
|
|
m.Get("/latest", repo.LatestRelease)
|
2022-12-21 22:06:26 +01:00
|
|
|
m.Get(".rss", feedEnabled, repo.ReleasesFeedRSS)
|
|
|
|
|
m.Get(".atom", feedEnabled, repo.ReleasesFeedAtom)
|
2023-04-28 02:08:47 +02:00
|
|
|
}, ctxDataSet("EnableFeed", setting.Other.EnableFeed),
|
2023-10-01 12:41:52 +02:00
|
|
|
repo.MustBeNotEmpty, context.RepoRefByType(context.RepoRefTag, true))
|
|
|
|
|
m.Get("/releases/attachments/{uuid}", repo.MustBeNotEmpty, repo.GetAttachment)
|
|
|
|
|
m.Get("/releases/download/{vTag}/{fileName}", repo.MustBeNotEmpty, repo.RedirectDownload)
|
2017-06-18 05:38:24 +02:00
|
|
|
m.Group("/releases", func() {
|
2017-05-18 16:54:24 +02:00
|
|
|
m.Get("/new", repo.NewRelease)
|
2022-12-12 09:09:26 +01:00
|
|
|
m.Post("/new", web.Bind(forms.NewReleaseForm{}), repo.NewReleasePost)
|
2017-05-18 16:54:24 +02:00
|
|
|
m.Post("/delete", repo.DeleteRelease)
|
2020-10-05 07:49:33 +02:00
|
|
|
m.Post("/attachments", repo.UploadReleaseAttachment)
|
|
|
|
|
m.Post("/attachments/remove", repo.DeleteAttachment)
|
2019-01-23 19:58:38 +01:00
|
|
|
}, reqSignIn, repo.MustBeNotEmpty, context.RepoMustNotBeArchived(), reqRepoReleaseWriter, context.RepoRef())
|
2017-05-18 16:54:24 +02:00
|
|
|
m.Group("/releases", func() {
|
|
|
|
|
m.Get("/edit/*", repo.EditRelease)
|
2022-12-12 09:09:26 +01:00
|
|
|
m.Post("/edit/*", web.Bind(forms.EditReleaseForm{}), repo.EditReleasePost)
|
2023-04-27 08:06:45 +02:00
|
|
|
}, reqSignIn, repo.MustBeNotEmpty, context.RepoMustNotBeArchived(), reqRepoReleaseWriter, repo.CommitInfoCache)
|
2021-04-10 02:26:08 +02:00
|
|
|
}, ignSignIn, context.RepoAssignment, context.UnitTypes(), reqRepoReleaseReader)
|
2017-04-25 09:24:51 +02:00
|
|
|
|
2021-07-23 20:08:04 +02:00
|
|
|
// to maintain compatibility with old attachments
|
|
|
|
|
m.Group("/{username}/{reponame}", func() {
|
|
|
|
|
m.Get("/attachments/{uuid}", repo.GetAttachment)
|
|
|
|
|
}, ignSignIn, context.RepoAssignment, context.UnitTypes())
|
|
|
|
|
|
2021-01-26 16:36:53 +01:00
|
|
|
m.Group("/{username}/{reponame}", func() {
|
2018-06-21 11:09:46 +02:00
|
|
|
m.Post("/topics", repo.TopicsPost)
|
2021-04-10 02:26:08 +02:00
|
|
|
}, context.RepoAssignment, context.RepoMustNotBeArchived(), reqRepoAdmin)
|
2018-04-11 04:51:44 +02:00
|
|
|
|
2021-01-26 16:36:53 +01:00
|
|
|
m.Group("/{username}/{reponame}", func() {
|
2017-04-25 09:24:51 +02:00
|
|
|
m.Group("", func() {
|
2023-07-20 14:41:28 +02:00
|
|
|
m.Get("/issues/posters", repo.IssuePosters) // it can't use {type:issues|pulls} because other routes like "/pulls/{index}" has higher priority
|
|
|
|
|
m.Get("/{type:issues|pulls}", repo.Issues)
|
2021-01-26 16:36:53 +01:00
|
|
|
m.Get("/{type:issues|pulls}/{index}", repo.ViewIssue)
|
2021-10-11 00:40:03 +02:00
|
|
|
m.Group("/{type:issues|pulls}/{index}/content-history", func() {
|
|
|
|
|
m.Get("/overview", repo.GetContentHistoryOverview)
|
|
|
|
|
m.Get("/list", repo.GetContentHistoryList)
|
|
|
|
|
m.Get("/detail", repo.GetContentHistoryDetail)
|
|
|
|
|
})
|
2021-01-26 16:36:53 +01:00
|
|
|
m.Get("/labels", reqRepoIssuesOrPullsReader, repo.RetrieveLabels, repo.Labels)
|
2018-11-28 12:26:14 +01:00
|
|
|
m.Get("/milestones", reqRepoIssuesOrPullsReader, repo.Milestones)
|
2017-06-03 07:56:36 +02:00
|
|
|
}, context.RepoRef())
|
2017-04-25 09:24:51 +02:00
|
|
|
|
2022-03-31 19:31:53 +02:00
|
|
|
if setting.Packages.Enabled {
|
|
|
|
|
m.Get("/packages", repo.Packages)
|
|
|
|
|
}
|
2022-03-30 10:42:47 +02:00
|
|
|
|
2020-08-17 05:07:38 +02:00
|
|
|
m.Group("/projects", func() {
|
|
|
|
|
m.Get("", repo.Projects)
|
2021-01-26 16:36:53 +01:00
|
|
|
m.Get("/{id}", repo.ViewProject)
|
2023-01-20 12:42:33 +01:00
|
|
|
m.Group("", func() { //nolint:dupl
|
2023-05-31 08:50:18 +02:00
|
|
|
m.Get("/new", repo.RenderNewProject)
|
2022-12-12 09:09:26 +01:00
|
|
|
m.Post("/new", web.Bind(forms.CreateProjectForm{}), repo.NewProjectPost)
|
2021-01-26 16:36:53 +01:00
|
|
|
m.Group("/{id}", func() {
|
2022-12-12 09:09:26 +01:00
|
|
|
m.Post("", web.Bind(forms.EditProjectBoardForm{}), repo.AddBoardToProjectPost)
|
2020-08-22 08:58:59 +02:00
|
|
|
m.Post("/delete", repo.DeleteProject)
|
|
|
|
|
|
2023-05-31 08:50:18 +02:00
|
|
|
m.Get("/edit", repo.RenderEditProject)
|
2022-12-12 09:09:26 +01:00
|
|
|
m.Post("/edit", web.Bind(forms.CreateProjectForm{}), repo.EditProjectPost)
|
2021-01-26 16:36:53 +01:00
|
|
|
m.Post("/{action:open|close}", repo.ChangeProjectStatus)
|
2020-08-22 08:58:59 +02:00
|
|
|
|
2021-01-26 16:36:53 +01:00
|
|
|
m.Group("/{boardID}", func() {
|
2022-12-12 09:09:26 +01:00
|
|
|
m.Put("", web.Bind(forms.EditProjectBoardForm{}), repo.EditProjectBoard)
|
2020-08-22 08:58:59 +02:00
|
|
|
m.Delete("", repo.DeleteProjectBoard)
|
2021-01-15 21:29:32 +01:00
|
|
|
m.Post("/default", repo.SetDefaultProjectBoard)
|
2023-04-19 16:28:28 +02:00
|
|
|
m.Post("/unsetdefault", repo.UnSetDefaultProjectBoard)
|
2020-08-22 08:58:59 +02:00
|
|
|
|
2021-12-08 07:57:18 +01:00
|
|
|
m.Post("/move", repo.MoveIssues)
|
2020-08-22 08:58:59 +02:00
|
|
|
})
|
2020-08-17 05:07:38 +02:00
|
|
|
})
|
2020-08-22 08:58:59 +02:00
|
|
|
}, reqRepoProjectsWriter, context.RepoMustNotBeArchived())
|
2020-08-17 05:07:38 +02:00
|
|
|
}, reqRepoProjectsReader, repo.MustEnableProjects)
|
|
|
|
|
|

Implement actions (#21937)
Close #13539.
Co-authored by: @lunny @appleboy @fuxiaohei and others.
Related projects:
- https://gitea.com/gitea/actions-proto-def
- https://gitea.com/gitea/actions-proto-go
- https://gitea.com/gitea/act
- https://gitea.com/gitea/act_runner
### Summary
The target of this PR is to bring a basic implementation of "Actions",
an internal CI/CD system of Gitea. That means even though it has been
merged, the state of the feature is **EXPERIMENTAL**, and please note
that:
- It is disabled by default;
- It shouldn't be used in a production environment currently;
- It shouldn't be used in a public Gitea instance currently;
- Breaking changes may be made before it's stable.
**Please comment on #13539 if you have any different product design
ideas**, all decisions reached there will be adopted here. But in this
PR, we don't talk about **naming, feature-creep or alternatives**.
### ⚠️ Breaking
`gitea-actions` will become a reserved user name. If a user with the
name already exists in the database, it is recommended to rename it.
### Some important reviews
- What is `DEFAULT_ACTIONS_URL` in `app.ini` for?
- https://github.com/go-gitea/gitea/pull/21937#discussion_r1055954954
- Why the api for runners is not under the normal `/api/v1` prefix?
- https://github.com/go-gitea/gitea/pull/21937#discussion_r1061173592
- Why DBFS?
- https://github.com/go-gitea/gitea/pull/21937#discussion_r1061301178
- Why ignore events triggered by `gitea-actions` bot?
- https://github.com/go-gitea/gitea/pull/21937#discussion_r1063254103
- Why there's no permission control for actions?
- https://github.com/go-gitea/gitea/pull/21937#discussion_r1090229868
### What it looks like
<details>
#### Manage runners
<img width="1792" alt="image"
src="https://user-images.githubusercontent.com/9418365/205870657-c72f590e-2e08-4cd4-be7f-2e0abb299bbf.png">
#### List runs
<img width="1792" alt="image"
src="https://user-images.githubusercontent.com/9418365/205872794-50fde990-2b45-48c1-a178-908e4ec5b627.png">
#### View logs
<img width="1792" alt="image"
src="https://user-images.githubusercontent.com/9418365/205872501-9b7b9000-9542-4991-8f55-18ccdada77c3.png">
</details>
### How to try it
<details>
#### 1. Start Gitea
Clone this branch and [install from
source](https://docs.gitea.io/en-us/install-from-source).
Add additional configurations in `app.ini` to enable Actions:
```ini
[actions]
ENABLED = true
```
Start it.
If all is well, you'll see the management page of runners:
<img width="1792" alt="image"
src="https://user-images.githubusercontent.com/9418365/205877365-8e30a780-9b10-4154-b3e8-ee6c3cb35a59.png">
#### 2. Start runner
Clone the [act_runner](https://gitea.com/gitea/act_runner), and follow
the
[README](https://gitea.com/gitea/act_runner/src/branch/main/README.md)
to start it.
If all is well, you'll see a new runner has been added:
<img width="1792" alt="image"
src="https://user-images.githubusercontent.com/9418365/205878000-216f5937-e696-470d-b66c-8473987d91c3.png">
#### 3. Enable actions for a repo
Create a new repo or open an existing one, check the `Actions` checkbox
in settings and submit.
<img width="1792" alt="image"
src="https://user-images.githubusercontent.com/9418365/205879705-53e09208-73c0-4b3e-a123-2dcf9aba4b9c.png">
<img width="1792" alt="image"
src="https://user-images.githubusercontent.com/9418365/205879383-23f3d08f-1a85-41dd-a8b3-54e2ee6453e8.png">
If all is well, you'll see a new tab "Actions":
<img width="1792" alt="image"
src="https://user-images.githubusercontent.com/9418365/205881648-a8072d8c-5803-4d76-b8a8-9b2fb49516c1.png">
#### 4. Upload workflow files
Upload some workflow files to `.gitea/workflows/xxx.yaml`, you can
follow the [quickstart](https://docs.github.com/en/actions/quickstart)
of GitHub Actions. Yes, Gitea Actions is compatible with GitHub Actions
in most cases, you can use the same demo:
```yaml
name: GitHub Actions Demo
run-name: ${{ github.actor }} is testing out GitHub Actions 🚀
on: [push]
jobs:
Explore-GitHub-Actions:
runs-on: ubuntu-latest
steps:
- run: echo "🎉 The job was automatically triggered by a ${{ github.event_name }} event."
- run: echo "🐧 This job is now running on a ${{ runner.os }} server hosted by GitHub!"
- run: echo "🔎 The name of your branch is ${{ github.ref }} and your repository is ${{ github.repository }}."
- name: Check out repository code
uses: actions/checkout@v3
- run: echo "💡 The ${{ github.repository }} repository has been cloned to the runner."
- run: echo "🖥️ The workflow is now ready to test your code on the runner."
- name: List files in the repository
run: |
ls ${{ github.workspace }}
- run: echo "🍏 This job's status is ${{ job.status }}."
```
If all is well, you'll see a new run in `Actions` tab:
<img width="1792" alt="image"
src="https://user-images.githubusercontent.com/9418365/205884473-79a874bc-171b-4aaf-acd5-0241a45c3b53.png">
#### 5. Check the logs of jobs
Click a run and you'll see the logs:
<img width="1792" alt="image"
src="https://user-images.githubusercontent.com/9418365/205884800-994b0374-67f7-48ff-be9a-4c53f3141547.png">
#### 6. Go on
You can try more examples in [the
documents](https://docs.github.com/en/actions/using-workflows/workflow-syntax-for-github-actions)
of GitHub Actions, then you might find a lot of bugs.
Come on, PRs are welcome.
</details>
See also: [Feature Preview: Gitea
Actions](https://blog.gitea.io/2022/12/feature-preview-gitea-actions/)
---------
Co-authored-by: a1012112796 <1012112796@qq.com>
Co-authored-by: Lunny Xiao <xiaolunwen@gmail.com>
Co-authored-by: delvh <dev.lh@web.de>
Co-authored-by: ChristopherHX <christopher.homberger@web.de>
Co-authored-by: John Olheiser <john.olheiser@gmail.com>
2023-01-31 02:45:19 +01:00
|
|
|
m.Group("/actions", func() {
|
|
|
|
|
m.Get("", actions.List)
|
2023-08-14 17:14:30 +02:00
|
|
|
m.Post("/disable", reqRepoAdmin, actions.DisableWorkflowFile)
|
|
|
|
|
m.Post("/enable", reqRepoAdmin, actions.EnableWorkflowFile)
|

Implement actions (#21937)
Close #13539.
Co-authored by: @lunny @appleboy @fuxiaohei and others.
Related projects:
- https://gitea.com/gitea/actions-proto-def
- https://gitea.com/gitea/actions-proto-go
- https://gitea.com/gitea/act
- https://gitea.com/gitea/act_runner
### Summary
The target of this PR is to bring a basic implementation of "Actions",
an internal CI/CD system of Gitea. That means even though it has been
merged, the state of the feature is **EXPERIMENTAL**, and please note
that:
- It is disabled by default;
- It shouldn't be used in a production environment currently;
- It shouldn't be used in a public Gitea instance currently;
- Breaking changes may be made before it's stable.
**Please comment on #13539 if you have any different product design
ideas**, all decisions reached there will be adopted here. But in this
PR, we don't talk about **naming, feature-creep or alternatives**.
### ⚠️ Breaking
`gitea-actions` will become a reserved user name. If a user with the
name already exists in the database, it is recommended to rename it.
### Some important reviews
- What is `DEFAULT_ACTIONS_URL` in `app.ini` for?
- https://github.com/go-gitea/gitea/pull/21937#discussion_r1055954954
- Why the api for runners is not under the normal `/api/v1` prefix?
- https://github.com/go-gitea/gitea/pull/21937#discussion_r1061173592
- Why DBFS?
- https://github.com/go-gitea/gitea/pull/21937#discussion_r1061301178
- Why ignore events triggered by `gitea-actions` bot?
- https://github.com/go-gitea/gitea/pull/21937#discussion_r1063254103
- Why there's no permission control for actions?
- https://github.com/go-gitea/gitea/pull/21937#discussion_r1090229868
### What it looks like
<details>
#### Manage runners
<img width="1792" alt="image"
src="https://user-images.githubusercontent.com/9418365/205870657-c72f590e-2e08-4cd4-be7f-2e0abb299bbf.png">
#### List runs
<img width="1792" alt="image"
src="https://user-images.githubusercontent.com/9418365/205872794-50fde990-2b45-48c1-a178-908e4ec5b627.png">
#### View logs
<img width="1792" alt="image"
src="https://user-images.githubusercontent.com/9418365/205872501-9b7b9000-9542-4991-8f55-18ccdada77c3.png">
</details>
### How to try it
<details>
#### 1. Start Gitea
Clone this branch and [install from
source](https://docs.gitea.io/en-us/install-from-source).
Add additional configurations in `app.ini` to enable Actions:
```ini
[actions]
ENABLED = true
```
Start it.
If all is well, you'll see the management page of runners:
<img width="1792" alt="image"
src="https://user-images.githubusercontent.com/9418365/205877365-8e30a780-9b10-4154-b3e8-ee6c3cb35a59.png">
#### 2. Start runner
Clone the [act_runner](https://gitea.com/gitea/act_runner), and follow
the
[README](https://gitea.com/gitea/act_runner/src/branch/main/README.md)
to start it.
If all is well, you'll see a new runner has been added:
<img width="1792" alt="image"
src="https://user-images.githubusercontent.com/9418365/205878000-216f5937-e696-470d-b66c-8473987d91c3.png">
#### 3. Enable actions for a repo
Create a new repo or open an existing one, check the `Actions` checkbox
in settings and submit.
<img width="1792" alt="image"
src="https://user-images.githubusercontent.com/9418365/205879705-53e09208-73c0-4b3e-a123-2dcf9aba4b9c.png">
<img width="1792" alt="image"
src="https://user-images.githubusercontent.com/9418365/205879383-23f3d08f-1a85-41dd-a8b3-54e2ee6453e8.png">
If all is well, you'll see a new tab "Actions":
<img width="1792" alt="image"
src="https://user-images.githubusercontent.com/9418365/205881648-a8072d8c-5803-4d76-b8a8-9b2fb49516c1.png">
#### 4. Upload workflow files
Upload some workflow files to `.gitea/workflows/xxx.yaml`, you can
follow the [quickstart](https://docs.github.com/en/actions/quickstart)
of GitHub Actions. Yes, Gitea Actions is compatible with GitHub Actions
in most cases, you can use the same demo:
```yaml
name: GitHub Actions Demo
run-name: ${{ github.actor }} is testing out GitHub Actions 🚀
on: [push]
jobs:
Explore-GitHub-Actions:
runs-on: ubuntu-latest
steps:
- run: echo "🎉 The job was automatically triggered by a ${{ github.event_name }} event."
- run: echo "🐧 This job is now running on a ${{ runner.os }} server hosted by GitHub!"
- run: echo "🔎 The name of your branch is ${{ github.ref }} and your repository is ${{ github.repository }}."
- name: Check out repository code
uses: actions/checkout@v3
- run: echo "💡 The ${{ github.repository }} repository has been cloned to the runner."
- run: echo "🖥️ The workflow is now ready to test your code on the runner."
- name: List files in the repository
run: |
ls ${{ github.workspace }}
- run: echo "🍏 This job's status is ${{ job.status }}."
```
If all is well, you'll see a new run in `Actions` tab:
<img width="1792" alt="image"
src="https://user-images.githubusercontent.com/9418365/205884473-79a874bc-171b-4aaf-acd5-0241a45c3b53.png">
#### 5. Check the logs of jobs
Click a run and you'll see the logs:
<img width="1792" alt="image"
src="https://user-images.githubusercontent.com/9418365/205884800-994b0374-67f7-48ff-be9a-4c53f3141547.png">
#### 6. Go on
You can try more examples in [the
documents](https://docs.github.com/en/actions/using-workflows/workflow-syntax-for-github-actions)
of GitHub Actions, then you might find a lot of bugs.
Come on, PRs are welcome.
</details>
See also: [Feature Preview: Gitea
Actions](https://blog.gitea.io/2022/12/feature-preview-gitea-actions/)
---------
Co-authored-by: a1012112796 <1012112796@qq.com>
Co-authored-by: Lunny Xiao <xiaolunwen@gmail.com>
Co-authored-by: delvh <dev.lh@web.de>
Co-authored-by: ChristopherHX <christopher.homberger@web.de>
Co-authored-by: John Olheiser <john.olheiser@gmail.com>
2023-01-31 02:45:19 +01:00
|
|
|
|
|
|
|
|
m.Group("/runs/{run}", func() {
|
|
|
|
|
m.Combo("").
|
|
|
|
|
Get(actions.View).
|
|
|
|
|
Post(web.Bind(actions.ViewRequest{}), actions.ViewPost)
|
|
|
|
|
m.Group("/jobs/{job}", func() {
|
|
|
|
|
m.Combo("").
|
|
|
|
|
Get(actions.View).
|
|
|
|
|
Post(web.Bind(actions.ViewRequest{}), actions.ViewPost)
|
2023-08-22 04:30:02 +02:00
|
|
|
m.Post("/rerun", reqRepoActionsWriter, actions.Rerun)
|
2023-06-29 04:58:56 +02:00
|
|
|
m.Get("/logs", actions.Logs)
|

Implement actions (#21937)
Close #13539.
Co-authored by: @lunny @appleboy @fuxiaohei and others.
Related projects:
- https://gitea.com/gitea/actions-proto-def
- https://gitea.com/gitea/actions-proto-go
- https://gitea.com/gitea/act
- https://gitea.com/gitea/act_runner
### Summary
The target of this PR is to bring a basic implementation of "Actions",
an internal CI/CD system of Gitea. That means even though it has been
merged, the state of the feature is **EXPERIMENTAL**, and please note
that:
- It is disabled by default;
- It shouldn't be used in a production environment currently;
- It shouldn't be used in a public Gitea instance currently;
- Breaking changes may be made before it's stable.
**Please comment on #13539 if you have any different product design
ideas**, all decisions reached there will be adopted here. But in this
PR, we don't talk about **naming, feature-creep or alternatives**.
### ⚠️ Breaking
`gitea-actions` will become a reserved user name. If a user with the
name already exists in the database, it is recommended to rename it.
### Some important reviews
- What is `DEFAULT_ACTIONS_URL` in `app.ini` for?
- https://github.com/go-gitea/gitea/pull/21937#discussion_r1055954954
- Why the api for runners is not under the normal `/api/v1` prefix?
- https://github.com/go-gitea/gitea/pull/21937#discussion_r1061173592
- Why DBFS?
- https://github.com/go-gitea/gitea/pull/21937#discussion_r1061301178
- Why ignore events triggered by `gitea-actions` bot?
- https://github.com/go-gitea/gitea/pull/21937#discussion_r1063254103
- Why there's no permission control for actions?
- https://github.com/go-gitea/gitea/pull/21937#discussion_r1090229868
### What it looks like
<details>
#### Manage runners
<img width="1792" alt="image"
src="https://user-images.githubusercontent.com/9418365/205870657-c72f590e-2e08-4cd4-be7f-2e0abb299bbf.png">
#### List runs
<img width="1792" alt="image"
src="https://user-images.githubusercontent.com/9418365/205872794-50fde990-2b45-48c1-a178-908e4ec5b627.png">
#### View logs
<img width="1792" alt="image"
src="https://user-images.githubusercontent.com/9418365/205872501-9b7b9000-9542-4991-8f55-18ccdada77c3.png">
</details>
### How to try it
<details>
#### 1. Start Gitea
Clone this branch and [install from
source](https://docs.gitea.io/en-us/install-from-source).
Add additional configurations in `app.ini` to enable Actions:
```ini
[actions]
ENABLED = true
```
Start it.
If all is well, you'll see the management page of runners:
<img width="1792" alt="image"
src="https://user-images.githubusercontent.com/9418365/205877365-8e30a780-9b10-4154-b3e8-ee6c3cb35a59.png">
#### 2. Start runner
Clone the [act_runner](https://gitea.com/gitea/act_runner), and follow
the
[README](https://gitea.com/gitea/act_runner/src/branch/main/README.md)
to start it.
If all is well, you'll see a new runner has been added:
<img width="1792" alt="image"
src="https://user-images.githubusercontent.com/9418365/205878000-216f5937-e696-470d-b66c-8473987d91c3.png">
#### 3. Enable actions for a repo
Create a new repo or open an existing one, check the `Actions` checkbox
in settings and submit.
<img width="1792" alt="image"
src="https://user-images.githubusercontent.com/9418365/205879705-53e09208-73c0-4b3e-a123-2dcf9aba4b9c.png">
<img width="1792" alt="image"
src="https://user-images.githubusercontent.com/9418365/205879383-23f3d08f-1a85-41dd-a8b3-54e2ee6453e8.png">
If all is well, you'll see a new tab "Actions":
<img width="1792" alt="image"
src="https://user-images.githubusercontent.com/9418365/205881648-a8072d8c-5803-4d76-b8a8-9b2fb49516c1.png">
#### 4. Upload workflow files
Upload some workflow files to `.gitea/workflows/xxx.yaml`, you can
follow the [quickstart](https://docs.github.com/en/actions/quickstart)
of GitHub Actions. Yes, Gitea Actions is compatible with GitHub Actions
in most cases, you can use the same demo:
```yaml
name: GitHub Actions Demo
run-name: ${{ github.actor }} is testing out GitHub Actions 🚀
on: [push]
jobs:
Explore-GitHub-Actions:
runs-on: ubuntu-latest
steps:
- run: echo "🎉 The job was automatically triggered by a ${{ github.event_name }} event."
- run: echo "🐧 This job is now running on a ${{ runner.os }} server hosted by GitHub!"
- run: echo "🔎 The name of your branch is ${{ github.ref }} and your repository is ${{ github.repository }}."
- name: Check out repository code
uses: actions/checkout@v3
- run: echo "💡 The ${{ github.repository }} repository has been cloned to the runner."
- run: echo "🖥️ The workflow is now ready to test your code on the runner."
- name: List files in the repository
run: |
ls ${{ github.workspace }}
- run: echo "🍏 This job's status is ${{ job.status }}."
```
If all is well, you'll see a new run in `Actions` tab:
<img width="1792" alt="image"
src="https://user-images.githubusercontent.com/9418365/205884473-79a874bc-171b-4aaf-acd5-0241a45c3b53.png">
#### 5. Check the logs of jobs
Click a run and you'll see the logs:
<img width="1792" alt="image"
src="https://user-images.githubusercontent.com/9418365/205884800-994b0374-67f7-48ff-be9a-4c53f3141547.png">
#### 6. Go on
You can try more examples in [the
documents](https://docs.github.com/en/actions/using-workflows/workflow-syntax-for-github-actions)
of GitHub Actions, then you might find a lot of bugs.
Come on, PRs are welcome.
</details>
See also: [Feature Preview: Gitea
Actions](https://blog.gitea.io/2022/12/feature-preview-gitea-actions/)
---------
Co-authored-by: a1012112796 <1012112796@qq.com>
Co-authored-by: Lunny Xiao <xiaolunwen@gmail.com>
Co-authored-by: delvh <dev.lh@web.de>
Co-authored-by: ChristopherHX <christopher.homberger@web.de>
Co-authored-by: John Olheiser <john.olheiser@gmail.com>
2023-01-31 02:45:19 +01:00
|
|
|
})
|
|
|
|
|
m.Post("/cancel", reqRepoActionsWriter, actions.Cancel)
|
2023-02-24 08:58:49 +01:00
|
|
|
m.Post("/approve", reqRepoActionsWriter, actions.Approve)
|
2023-05-19 15:37:57 +02:00
|
|
|
m.Post("/artifacts", actions.ArtifactsView)
|
2023-07-21 04:42:01 +02:00
|
|
|
m.Get("/artifacts/{artifact_name}", actions.ArtifactsDownloadView)
|
2023-08-22 04:30:02 +02:00
|
|
|
m.Post("/rerun", reqRepoActionsWriter, actions.Rerun)
|

Implement actions (#21937)
Close #13539.
Co-authored by: @lunny @appleboy @fuxiaohei and others.
Related projects:
- https://gitea.com/gitea/actions-proto-def
- https://gitea.com/gitea/actions-proto-go
- https://gitea.com/gitea/act
- https://gitea.com/gitea/act_runner
### Summary
The target of this PR is to bring a basic implementation of "Actions",
an internal CI/CD system of Gitea. That means even though it has been
merged, the state of the feature is **EXPERIMENTAL**, and please note
that:
- It is disabled by default;
- It shouldn't be used in a production environment currently;
- It shouldn't be used in a public Gitea instance currently;
- Breaking changes may be made before it's stable.
**Please comment on #13539 if you have any different product design
ideas**, all decisions reached there will be adopted here. But in this
PR, we don't talk about **naming, feature-creep or alternatives**.
### ⚠️ Breaking
`gitea-actions` will become a reserved user name. If a user with the
name already exists in the database, it is recommended to rename it.
### Some important reviews
- What is `DEFAULT_ACTIONS_URL` in `app.ini` for?
- https://github.com/go-gitea/gitea/pull/21937#discussion_r1055954954
- Why the api for runners is not under the normal `/api/v1` prefix?
- https://github.com/go-gitea/gitea/pull/21937#discussion_r1061173592
- Why DBFS?
- https://github.com/go-gitea/gitea/pull/21937#discussion_r1061301178
- Why ignore events triggered by `gitea-actions` bot?
- https://github.com/go-gitea/gitea/pull/21937#discussion_r1063254103
- Why there's no permission control for actions?
- https://github.com/go-gitea/gitea/pull/21937#discussion_r1090229868
### What it looks like
<details>
#### Manage runners
<img width="1792" alt="image"
src="https://user-images.githubusercontent.com/9418365/205870657-c72f590e-2e08-4cd4-be7f-2e0abb299bbf.png">
#### List runs
<img width="1792" alt="image"
src="https://user-images.githubusercontent.com/9418365/205872794-50fde990-2b45-48c1-a178-908e4ec5b627.png">
#### View logs
<img width="1792" alt="image"
src="https://user-images.githubusercontent.com/9418365/205872501-9b7b9000-9542-4991-8f55-18ccdada77c3.png">
</details>
### How to try it
<details>
#### 1. Start Gitea
Clone this branch and [install from
source](https://docs.gitea.io/en-us/install-from-source).
Add additional configurations in `app.ini` to enable Actions:
```ini
[actions]
ENABLED = true
```
Start it.
If all is well, you'll see the management page of runners:
<img width="1792" alt="image"
src="https://user-images.githubusercontent.com/9418365/205877365-8e30a780-9b10-4154-b3e8-ee6c3cb35a59.png">
#### 2. Start runner
Clone the [act_runner](https://gitea.com/gitea/act_runner), and follow
the
[README](https://gitea.com/gitea/act_runner/src/branch/main/README.md)
to start it.
If all is well, you'll see a new runner has been added:
<img width="1792" alt="image"
src="https://user-images.githubusercontent.com/9418365/205878000-216f5937-e696-470d-b66c-8473987d91c3.png">
#### 3. Enable actions for a repo
Create a new repo or open an existing one, check the `Actions` checkbox
in settings and submit.
<img width="1792" alt="image"
src="https://user-images.githubusercontent.com/9418365/205879705-53e09208-73c0-4b3e-a123-2dcf9aba4b9c.png">
<img width="1792" alt="image"
src="https://user-images.githubusercontent.com/9418365/205879383-23f3d08f-1a85-41dd-a8b3-54e2ee6453e8.png">
If all is well, you'll see a new tab "Actions":
<img width="1792" alt="image"
src="https://user-images.githubusercontent.com/9418365/205881648-a8072d8c-5803-4d76-b8a8-9b2fb49516c1.png">
#### 4. Upload workflow files
Upload some workflow files to `.gitea/workflows/xxx.yaml`, you can
follow the [quickstart](https://docs.github.com/en/actions/quickstart)
of GitHub Actions. Yes, Gitea Actions is compatible with GitHub Actions
in most cases, you can use the same demo:
```yaml
name: GitHub Actions Demo
run-name: ${{ github.actor }} is testing out GitHub Actions 🚀
on: [push]
jobs:
Explore-GitHub-Actions:
runs-on: ubuntu-latest
steps:
- run: echo "🎉 The job was automatically triggered by a ${{ github.event_name }} event."
- run: echo "🐧 This job is now running on a ${{ runner.os }} server hosted by GitHub!"
- run: echo "🔎 The name of your branch is ${{ github.ref }} and your repository is ${{ github.repository }}."
- name: Check out repository code
uses: actions/checkout@v3
- run: echo "💡 The ${{ github.repository }} repository has been cloned to the runner."
- run: echo "🖥️ The workflow is now ready to test your code on the runner."
- name: List files in the repository
run: |
ls ${{ github.workspace }}
- run: echo "🍏 This job's status is ${{ job.status }}."
```
If all is well, you'll see a new run in `Actions` tab:
<img width="1792" alt="image"
src="https://user-images.githubusercontent.com/9418365/205884473-79a874bc-171b-4aaf-acd5-0241a45c3b53.png">
#### 5. Check the logs of jobs
Click a run and you'll see the logs:
<img width="1792" alt="image"
src="https://user-images.githubusercontent.com/9418365/205884800-994b0374-67f7-48ff-be9a-4c53f3141547.png">
#### 6. Go on
You can try more examples in [the
documents](https://docs.github.com/en/actions/using-workflows/workflow-syntax-for-github-actions)
of GitHub Actions, then you might find a lot of bugs.
Come on, PRs are welcome.
</details>
See also: [Feature Preview: Gitea
Actions](https://blog.gitea.io/2022/12/feature-preview-gitea-actions/)
---------
Co-authored-by: a1012112796 <1012112796@qq.com>
Co-authored-by: Lunny Xiao <xiaolunwen@gmail.com>
Co-authored-by: delvh <dev.lh@web.de>
Co-authored-by: ChristopherHX <christopher.homberger@web.de>
Co-authored-by: John Olheiser <john.olheiser@gmail.com>
2023-01-31 02:45:19 +01:00
|
|
|
})
|
|
|
|
|
}, reqRepoActionsReader, actions.MustEnableActions)
|
|
|
|
|
|
2017-04-25 09:24:51 +02:00
|
|
|
m.Group("/wiki", func() {
|
2021-11-16 19:18:25 +01:00
|
|
|
m.Combo("/").
|
|
|
|
|
Get(repo.Wiki).
|
2023-04-27 08:06:45 +02:00
|
|
|
Post(context.RepoMustNotBeArchived(), reqSignIn, reqRepoWikiWriter, web.Bind(forms.NewWikiForm{}), repo.WikiPost)
|
2021-11-16 19:18:25 +01:00
|
|
|
m.Combo("/*").
|
|
|
|
|
Get(repo.Wiki).
|
2023-04-27 08:06:45 +02:00
|
|
|
Post(context.RepoMustNotBeArchived(), reqSignIn, reqRepoWikiWriter, web.Bind(forms.NewWikiForm{}), repo.WikiPost)
|
2021-02-13 05:35:43 +01:00
|
|
|
m.Get("/commit/{sha:[a-f0-9]{7,40}}", repo.SetEditorconfigIfExists, repo.SetDiffViewStyle, repo.SetWhitespaceBehavior, repo.Diff)
|
2021-08-31 04:22:54 +02:00
|
|
|
m.Get("/commit/{sha:[a-f0-9]{7,40}}.{ext:patch|diff}", repo.RawDiff)
|
2021-11-16 19:18:25 +01:00
|
|
|
}, repo.MustEnableWiki, func(ctx *context.Context) {
|
2020-05-16 18:38:40 +02:00
|
|
|
ctx.Data["PageIsWiki"] = true
|
2022-03-29 05:21:30 +02:00
|
|
|
ctx.Data["CloneButtonOriginLink"] = ctx.Repo.Repository.WikiCloneLink()
|
2020-05-16 18:38:40 +02:00
|
|
|
})
|
2017-04-25 09:24:51 +02:00
|
|
|
|
|
|
|
|
m.Group("/wiki", func() {
|
|
|
|
|
m.Get("/raw/*", repo.WikiRaw)
|
2017-09-30 06:04:16 +02:00
|
|
|
}, repo.MustEnableWiki)
|
2017-04-25 09:24:51 +02:00
|
|
|
|
2017-10-15 01:17:39 +02:00
|
|
|
m.Group("/activity", func() {
|
|
|
|
|
m.Get("", repo.Activity)
|
2021-01-26 16:36:53 +01:00
|
|
|
m.Get("/{period}", repo.Activity)
|
2021-11-09 20:57:58 +01:00
|
|
|
}, context.RepoRef(), repo.MustBeNotEmpty, context.RequireRepoReaderOr(unit.TypePullRequests, unit.TypeIssues, unit.TypeReleases))
|
2017-10-15 01:17:39 +02:00
|
|
|
|
2019-05-04 14:39:03 +02:00
|
|
|
m.Group("/activity_author_data", func() {
|
|
|
|
|
m.Get("", repo.ActivityAuthors)
|
2021-01-26 16:36:53 +01:00
|
|
|
m.Get("/{period}", repo.ActivityAuthors)
|
2021-11-09 20:57:58 +01:00
|
|
|
}, context.RepoRef(), repo.MustBeNotEmpty, context.RequireRepoReaderOr(unit.TypeCode))
|
2019-05-04 14:39:03 +02:00
|
|
|
|

[RFC] Make archival asynchronous (#11296)
* Make archival asynchronous
The prime benefit being sought here is for large archives to not
clog up the rendering process and cause unsightly proxy timeouts.
As a secondary benefit, archive-in-progress is moved out of the
way into a /tmp file so that new archival requests for the same
commit will not get fulfilled based on an archive that isn't yet
finished.
This asynchronous system is fairly primitive; request comes in, we'll
spawn off a new goroutine to handle it, then we'll mark it as done.
Status requests will see if the file exists in the final location,
and report the archival as done when it exists.
Fixes #11265
* Archive links: drop initial delay to three-quarters of a second
Some, or perhaps even most, archives will not take all that long to archive.
The archive process starts as soon as the download button is initially
clicked, so in theory they could be done quite quickly. Drop the initial
delay down to three-quarters of a second to make it more responsive in the
common case of the archive being quickly created.
* archiver: restructure a little bit to facilitate testing
This introduces two sync.Cond pointers to the archiver package. If they're
non-nil when we go to process a request, we'll wait until signalled (at all)
to proceed. The tests will then create the sync.Cond so that it can signal
at-will and sanity-check the state of the queue at different phases.
The author believes that nil-checking these two sync.Cond pointers on every
archive processing will introduce minimal overhead with no impact on
maintainability.
* gofmt nit: no space around binary + operator
* services: archiver: appease golangci-lint, lock queueMutex
Locking/unlocking the queueMutex is allowed, but not required, for
Cond.Signal() and Cond.Broadcast(). The magic at play here is just a little
too much for golangci-lint, as we take the address of queueMutex and this is
mostly used in archiver.go; the variable still gets flagged as unused.
* archiver: tests: fix several timing nits
Once we've signaled a cond var, it may take some small amount of time for
the goroutines released to hit the spot we're wanting them to be at. Give
them an appropriate amount of time.
* archiver: tests: no underscore in var name, ungh
* archiver: tests: Test* is run in a separate context than TestMain
We must setup the mutex/cond variables at the beginning of any test that's
going to use it, or else these will be nil when the test is actually ran.
* archiver: tests: hopefully final tweak
Things got shuffled around such that we carefully build up and release
requests from the queue, so we can validate the state of the queue at each
step. Fix some assertions that no longer hold true as fallout.
* repo: Download: restore some semblance of previous behavior
When archival was made async, the GET endpoint was only useful if a previous
POST had initiated the download. This commit restores the previous behavior,
to an extent; we'll now submit the archive request there and return a
"202 Accepted" to indicate that it's processing if we didn't manage to
complete the request within ~2 seconds of submission.
This lets a client directly GET the archive, and gives them some indication
that they may attempt to GET it again at a later time.
* archiver: tests: simplify a bit further
We don't need to risk failure and use time.ParseDuration to get 2 *
time.Second.
else if isn't really necessary if the conditions are simple enough and lead
to the same result.
* archiver: tests: resolve potential source of flakiness
Increase all timeouts to 10 seconds; these aren't hard-coded sleeps, so
there's no guarantee we'll actually take that long. If we need longer to
not have a false-positive, then so be it.
While here, various assert.{Not,}Equal arguments are flipped around so that
the wording in error output reflects reality, where the expected argument is
second and actual third.
* archiver: setup infrastructure for notifying consumers of completion
This API will *not* allow consumers to subscribe to specific requests being
completed, just *any* request being completed. The caller is responsible for
determining if their request is satisfied and waiting again if needed.
* repo: archive: make GET endpoint synchronous again
If the request isn't complete, this endpoint will now submit the request and
wait for completion using the new API. This may still be susceptible to
timeouts for larger repos, but other endpoints now exist that the web
interface will use to negotiate its way through larger archive processes.
* archiver: tests: amend test to include WaitForCompletion()
This is a trivial one, so go ahead and include it.
* archiver: tests: fix test by calling NewContext()
The mutex is otherwise uninitialized, so we need to ensure that we're
actually initializing it if we plan to test it.
* archiver: tests: integrate new WaitForCompletion a little better
We can use this to wait for archives to come in, rather than spinning and
hoping with a timeout.
* archiver: tests: combine numQueued declaration with next-instruction assignment
* routers: repo: reap unused archiving flag from DownloadStatus()
This had some planned usage before, indicating whether this request
initiated the archival process or not. After several rounds of refactoring,
this use was deemed not necessary for much of anything and got boiled down
to !complete in all cases.
* services: archiver: restructure to use a channel
We now offer two forms of waiting for a request:
- WaitForCompletion: wait for completion with no timeout
- TimedWaitForCompletion: wait for completion with timeout
In both cases, we wait for the given request's cchan to close; in the latter
case, we do so with the caller-provided timeout. This completely removes the
need for busy-wait loops in Download/InitiateDownload, as it's fairly clean
to wait on a channel with timeout.
* services: archiver: use defer to unlock now that we can
This previously carried the lock into the goroutine, but an intermediate
step just added the request to archiveInProgress outside of the new
goroutine and removed the need for the goroutine to start out with it.
* Revert "archiver: tests: combine numQueued declaration with next-instruction assignment"
This reverts commit bcc52140238e16680f2e05e448e9be51372afdf5.
Revert "archiver: tests: integrate new WaitForCompletion a little better"
This reverts commit 9fc8bedb5667d24d3a3c7843dc28a229efffb1e6.
Revert "archiver: tests: fix test by calling NewContext()"
This reverts commit 709c35685eaaf261ebbb7d3420e3376a4ee8e7f2.
Revert "archiver: tests: amend test to include WaitForCompletion()"
This reverts commit 75261f56bc05d1fa8ff7e81dcbc0ccd93fdc9d50.
* archiver: tests: first attempt at WaitForCompletion() tests
* archiver: tests: slight improvement, less busy-loop
Just wait for the requests to complete in order, instead of busy-waiting
with a timeout. This is slightly less fragile.
While here, reverse the arguments of a nearby assert.Equal() so that
expected/actual are correct in any test output.
* archiver: address lint nits
* services: archiver: only close the channel once
* services: archiver: use a struct{} for the wait channel
This makes it obvious that the channel is only being used as a signal,
rather than anything useful being piped through it.
* archiver: tests: fix expectations
Move the close of the channel into doArchive() itself; notably, before these
goroutines move on to waiting on the Release cond.
The tests are adjusted to reflect that we can't WaitForCompletion() after
they've already completed, as WaitForCompletion() doesn't indicate that
they've been released from the queue yet.
* archiver: tests: set cchan to nil for comparison
* archiver: move ctx.Error's back into the route handlers
We shouldn't be setting this in a service, we should just be validating the
request that we were handed.
* services: archiver: use regex to match a hash
This makes sure we don't try and use refName as a hash when it's clearly not
one, e.g. heads/pull/foo.
* routers: repo: remove the weird /archive/status endpoint
We don't need to do this anymore, we can just continue POSTing to the
archive/* endpoint until we're told the download's complete. This avoids a
potential naming conflict, where a ref could start with "status/"
* archiver: tests: bump reasonable timeout to 15s
* archiver: tests: actually release timedReq
* archiver: tests: run through inFlight instead of manually checking
While we're here, add a test for manually re-processing an archive that's
already been complete. Re-open the channel and mark it incomplete, so that
doArchive can just mark it complete again.
* initArchiveLinks: prevent default behavior from clicking
* archiver: alias gitea's context, golang context import pending
* archiver: simplify logic, just reconstruct slices
While the previous logic was perhaps slightly more efficient, the
new variant's readability is much improved.
* archiver: don't block shutdown on waiting for archive
The technique established launches a goroutine to do the wait,
which will close a wait channel upon termination. For the timeout
case, we also send back a value indicating whether the timeout was
hit or not.
The timeouts are expected to be relatively small, but still a multi-
second delay to shutdown due to this could be unfortunate.
* archiver: simplify shutdown logic
We can just grab the shutdown channel from the graceful manager instead of
constructing a channel to halt the caller and/or pass a result back.
* Style issues
* Fix mis-merge
Co-authored-by: Lunny Xiao <xiaolunwen@gmail.com>
Co-authored-by: Lauris BH <lauris@nix.lv>
2020-11-07 21:27:28 +01:00
|
|
|
m.Group("/archive", func() {
|
2021-06-23 23:12:38 +02:00
|
|
|
m.Get("/*", repo.Download)
|

[RFC] Make archival asynchronous (#11296)
* Make archival asynchronous
The prime benefit being sought here is for large archives to not
clog up the rendering process and cause unsightly proxy timeouts.
As a secondary benefit, archive-in-progress is moved out of the
way into a /tmp file so that new archival requests for the same
commit will not get fulfilled based on an archive that isn't yet
finished.
This asynchronous system is fairly primitive; request comes in, we'll
spawn off a new goroutine to handle it, then we'll mark it as done.
Status requests will see if the file exists in the final location,
and report the archival as done when it exists.
Fixes #11265
* Archive links: drop initial delay to three-quarters of a second
Some, or perhaps even most, archives will not take all that long to archive.
The archive process starts as soon as the download button is initially
clicked, so in theory they could be done quite quickly. Drop the initial
delay down to three-quarters of a second to make it more responsive in the
common case of the archive being quickly created.
* archiver: restructure a little bit to facilitate testing
This introduces two sync.Cond pointers to the archiver package. If they're
non-nil when we go to process a request, we'll wait until signalled (at all)
to proceed. The tests will then create the sync.Cond so that it can signal
at-will and sanity-check the state of the queue at different phases.
The author believes that nil-checking these two sync.Cond pointers on every
archive processing will introduce minimal overhead with no impact on
maintainability.
* gofmt nit: no space around binary + operator
* services: archiver: appease golangci-lint, lock queueMutex
Locking/unlocking the queueMutex is allowed, but not required, for
Cond.Signal() and Cond.Broadcast(). The magic at play here is just a little
too much for golangci-lint, as we take the address of queueMutex and this is
mostly used in archiver.go; the variable still gets flagged as unused.
* archiver: tests: fix several timing nits
Once we've signaled a cond var, it may take some small amount of time for
the goroutines released to hit the spot we're wanting them to be at. Give
them an appropriate amount of time.
* archiver: tests: no underscore in var name, ungh
* archiver: tests: Test* is run in a separate context than TestMain
We must setup the mutex/cond variables at the beginning of any test that's
going to use it, or else these will be nil when the test is actually ran.
* archiver: tests: hopefully final tweak
Things got shuffled around such that we carefully build up and release
requests from the queue, so we can validate the state of the queue at each
step. Fix some assertions that no longer hold true as fallout.
* repo: Download: restore some semblance of previous behavior
When archival was made async, the GET endpoint was only useful if a previous
POST had initiated the download. This commit restores the previous behavior,
to an extent; we'll now submit the archive request there and return a
"202 Accepted" to indicate that it's processing if we didn't manage to
complete the request within ~2 seconds of submission.
This lets a client directly GET the archive, and gives them some indication
that they may attempt to GET it again at a later time.
* archiver: tests: simplify a bit further
We don't need to risk failure and use time.ParseDuration to get 2 *
time.Second.
else if isn't really necessary if the conditions are simple enough and lead
to the same result.
* archiver: tests: resolve potential source of flakiness
Increase all timeouts to 10 seconds; these aren't hard-coded sleeps, so
there's no guarantee we'll actually take that long. If we need longer to
not have a false-positive, then so be it.
While here, various assert.{Not,}Equal arguments are flipped around so that
the wording in error output reflects reality, where the expected argument is
second and actual third.
* archiver: setup infrastructure for notifying consumers of completion
This API will *not* allow consumers to subscribe to specific requests being
completed, just *any* request being completed. The caller is responsible for
determining if their request is satisfied and waiting again if needed.
* repo: archive: make GET endpoint synchronous again
If the request isn't complete, this endpoint will now submit the request and
wait for completion using the new API. This may still be susceptible to
timeouts for larger repos, but other endpoints now exist that the web
interface will use to negotiate its way through larger archive processes.
* archiver: tests: amend test to include WaitForCompletion()
This is a trivial one, so go ahead and include it.
* archiver: tests: fix test by calling NewContext()
The mutex is otherwise uninitialized, so we need to ensure that we're
actually initializing it if we plan to test it.
* archiver: tests: integrate new WaitForCompletion a little better
We can use this to wait for archives to come in, rather than spinning and
hoping with a timeout.
* archiver: tests: combine numQueued declaration with next-instruction assignment
* routers: repo: reap unused archiving flag from DownloadStatus()
This had some planned usage before, indicating whether this request
initiated the archival process or not. After several rounds of refactoring,
this use was deemed not necessary for much of anything and got boiled down
to !complete in all cases.
* services: archiver: restructure to use a channel
We now offer two forms of waiting for a request:
- WaitForCompletion: wait for completion with no timeout
- TimedWaitForCompletion: wait for completion with timeout
In both cases, we wait for the given request's cchan to close; in the latter
case, we do so with the caller-provided timeout. This completely removes the
need for busy-wait loops in Download/InitiateDownload, as it's fairly clean
to wait on a channel with timeout.
* services: archiver: use defer to unlock now that we can
This previously carried the lock into the goroutine, but an intermediate
step just added the request to archiveInProgress outside of the new
goroutine and removed the need for the goroutine to start out with it.
* Revert "archiver: tests: combine numQueued declaration with next-instruction assignment"
This reverts commit bcc52140238e16680f2e05e448e9be51372afdf5.
Revert "archiver: tests: integrate new WaitForCompletion a little better"
This reverts commit 9fc8bedb5667d24d3a3c7843dc28a229efffb1e6.
Revert "archiver: tests: fix test by calling NewContext()"
This reverts commit 709c35685eaaf261ebbb7d3420e3376a4ee8e7f2.
Revert "archiver: tests: amend test to include WaitForCompletion()"
This reverts commit 75261f56bc05d1fa8ff7e81dcbc0ccd93fdc9d50.
* archiver: tests: first attempt at WaitForCompletion() tests
* archiver: tests: slight improvement, less busy-loop
Just wait for the requests to complete in order, instead of busy-waiting
with a timeout. This is slightly less fragile.
While here, reverse the arguments of a nearby assert.Equal() so that
expected/actual are correct in any test output.
* archiver: address lint nits
* services: archiver: only close the channel once
* services: archiver: use a struct{} for the wait channel
This makes it obvious that the channel is only being used as a signal,
rather than anything useful being piped through it.
* archiver: tests: fix expectations
Move the close of the channel into doArchive() itself; notably, before these
goroutines move on to waiting on the Release cond.
The tests are adjusted to reflect that we can't WaitForCompletion() after
they've already completed, as WaitForCompletion() doesn't indicate that
they've been released from the queue yet.
* archiver: tests: set cchan to nil for comparison
* archiver: move ctx.Error's back into the route handlers
We shouldn't be setting this in a service, we should just be validating the
request that we were handed.
* services: archiver: use regex to match a hash
This makes sure we don't try and use refName as a hash when it's clearly not
one, e.g. heads/pull/foo.
* routers: repo: remove the weird /archive/status endpoint
We don't need to do this anymore, we can just continue POSTing to the
archive/* endpoint until we're told the download's complete. This avoids a
potential naming conflict, where a ref could start with "status/"
* archiver: tests: bump reasonable timeout to 15s
* archiver: tests: actually release timedReq
* archiver: tests: run through inFlight instead of manually checking
While we're here, add a test for manually re-processing an archive that's
already been complete. Re-open the channel and mark it incomplete, so that
doArchive can just mark it complete again.
* initArchiveLinks: prevent default behavior from clicking
* archiver: alias gitea's context, golang context import pending
* archiver: simplify logic, just reconstruct slices
While the previous logic was perhaps slightly more efficient, the
new variant's readability is much improved.
* archiver: don't block shutdown on waiting for archive
The technique established launches a goroutine to do the wait,
which will close a wait channel upon termination. For the timeout
case, we also send back a value indicating whether the timeout was
hit or not.
The timeouts are expected to be relatively small, but still a multi-
second delay to shutdown due to this could be unfortunate.
* archiver: simplify shutdown logic
We can just grab the shutdown channel from the graceful manager instead of
constructing a channel to halt the caller and/or pass a result back.
* Style issues
* Fix mis-merge
Co-authored-by: Lunny Xiao <xiaolunwen@gmail.com>
Co-authored-by: Lauris BH <lauris@nix.lv>
2020-11-07 21:27:28 +01:00
|
|
|
m.Post("/*", repo.InitiateDownload)
|
2022-07-31 18:57:02 +02:00
|
|
|
}, repo.MustBeNotEmpty, dlSourceEnabled, reqRepoCodeReader)
|
2017-04-25 09:24:51 +02:00
|
|
|
|
2017-10-26 02:49:16 +02:00
|
|
|
m.Group("/branches", func() {
|
2023-07-22 13:47:06 +02:00
|
|
|
m.Get("/list", repo.GetBranchesList)
|
2017-10-26 02:49:16 +02:00
|
|
|
m.Get("", repo.Branches)
|
2019-01-18 01:01:04 +01:00
|
|
|
}, repo.MustBeNotEmpty, context.RepoRef(), reqRepoCodeReader)
|
2017-10-26 02:49:16 +02:00
|
|
|
|
2019-11-15 03:52:59 +01:00
|
|
|
m.Group("/blob_excerpt", func() {
|
2021-01-26 16:36:53 +01:00
|
|
|
m.Get("/{sha}", repo.SetEditorconfigIfExists, repo.SetDiffViewStyle, repo.ExcerptBlob)
|
2023-07-07 07:31:56 +02:00
|
|
|
}, func(ctx *context.Context) gocontext.CancelFunc {
|
2022-02-05 19:26:12 +01:00
|
|
|
if ctx.FormBool("wiki") {
|
|
|
|
|
ctx.Data["PageIsWiki"] = true
|
|
|
|
|
repo.MustEnableWiki(ctx)
|
2023-07-07 07:31:56 +02:00
|
|
|
return nil
|
2022-02-05 19:26:12 +01:00
|
|
|
}
|
|
|
|
|
|
|
|
|
|
reqRepoCodeReader(ctx)
|
|
|
|
|
if ctx.Written() {
|
2023-07-07 07:31:56 +02:00
|
|
|
return nil
|
2022-02-05 19:26:12 +01:00
|
|
|
}
|
2023-07-07 07:31:56 +02:00
|
|
|
cancel := context.RepoRef()(ctx)
|
2022-02-05 19:26:12 +01:00
|
|
|
if ctx.Written() {
|
2023-07-07 07:31:56 +02:00
|
|
|
return cancel
|
2022-02-05 19:26:12 +01:00
|
|
|
}
|
|
|
|
|
|
|
|
|
|
repo.MustBeNotEmpty(ctx)
|
2022-06-20 12:02:49 +02:00
|
|
|
return cancel
|
2022-02-05 19:26:12 +01:00
|
|
|
})
|
2019-11-15 03:52:59 +01:00
|
|
|
|
2023-07-20 14:41:28 +02:00
|
|
|
m.Get("/pulls/posters", repo.PullPosters)
|
2021-01-26 16:36:53 +01:00
|
|
|
m.Group("/pulls/{index}", func() {
|
2023-07-03 03:00:28 +02:00
|
|
|
m.Get("", repo.SetWhitespaceBehavior, repo.GetPullDiffStats, repo.ViewIssue)
|
2018-01-05 11:56:52 +01:00
|
|
|
m.Get(".diff", repo.DownloadPullDiff)
|
2018-01-07 14:10:20 +01:00
|
|
|
m.Get(".patch", repo.DownloadPullPatch)
|
2023-07-28 21:18:12 +02:00
|
|
|
m.Group("/commits", func() {
|
|
|
|
|
m.Get("", context.RepoRef(), repo.SetWhitespaceBehavior, repo.GetPullDiffStats, repo.ViewPullCommits)
|
|
|
|
|
m.Get("/list", context.RepoRef(), repo.GetPullCommits)
|
|
|
|
|
m.Get("/{sha:[a-f0-9]{7,40}}", context.RepoRef(), repo.SetEditorconfigIfExists, repo.SetDiffViewStyle, repo.SetWhitespaceBehavior, repo.SetShowOutdatedComments, repo.ViewPullFilesForSingleCommit)
|
|
|
|
|
})
|
2022-12-12 09:09:26 +01:00
|
|
|
m.Post("/merge", context.RepoMustNotBeArchived(), web.Bind(forms.MergePullRequestForm{}), repo.MergePullRequest)
|
2022-06-11 16:44:20 +02:00
|
|
|
m.Post("/cancel_auto_merge", context.RepoMustNotBeArchived(), repo.CancelAutoMergePullRequest)
|
2020-01-17 07:03:40 +01:00
|
|
|
m.Post("/update", repo.UpdatePullRequest)
|
2022-12-12 09:09:26 +01:00
|
|
|
m.Post("/set_allow_maintainer_edit", web.Bind(forms.UpdateAllowEditsForm{}), repo.SetAllowEdits)
|
2019-01-23 19:58:38 +01:00
|
|
|
m.Post("/cleanup", context.RepoMustNotBeArchived(), context.RepoRef(), repo.CleanUpPullRequest)
|
2018-08-06 06:43:22 +02:00
|
|
|
m.Group("/files", func() {
|
2023-07-28 21:18:12 +02:00
|
|
|
m.Get("", context.RepoRef(), repo.SetEditorconfigIfExists, repo.SetDiffViewStyle, repo.SetWhitespaceBehavior, repo.SetShowOutdatedComments, repo.ViewPullFilesForAllCommitsOfPr)
|
|
|
|
|
m.Get("/{sha:[a-f0-9]{7,40}}", context.RepoRef(), repo.SetEditorconfigIfExists, repo.SetDiffViewStyle, repo.SetWhitespaceBehavior, repo.SetShowOutdatedComments, repo.ViewPullFilesStartingFromCommit)
|
|
|
|
|
m.Get("/{shaFrom:[a-f0-9]{7,40}}..{shaTo:[a-f0-9]{7,40}}", context.RepoRef(), repo.SetEditorconfigIfExists, repo.SetDiffViewStyle, repo.SetWhitespaceBehavior, repo.SetShowOutdatedComments, repo.ViewPullFilesForRange)
|
2018-08-06 06:43:22 +02:00
|
|
|
m.Group("/reviews", func() {
|
2021-01-08 22:49:55 +01:00
|
|
|
m.Get("/new_comment", repo.RenderNewCodeCommentForm)
|
2023-06-21 18:08:12 +02:00
|
|
|
m.Post("/comments", web.Bind(forms.CodeCommentForm{}), repo.SetShowOutdatedComments, repo.CreateCodeComment)
|
2022-12-12 09:09:26 +01:00
|
|
|
m.Post("/submit", web.Bind(forms.SubmitReviewForm{}), repo.SubmitReview)
|
2019-01-23 19:58:38 +01:00
|
|
|
}, context.RepoMustNotBeArchived())
|
2018-08-06 06:43:22 +02:00
|
|
|
})
|
2017-09-30 06:04:16 +02:00
|
|
|
}, repo.MustAllowPulls)
|
2017-04-25 09:24:51 +02:00
|
|
|
|
2019-02-12 16:09:43 +01:00
|
|
|
m.Group("/media", func() {
|
|
|
|
|
m.Get("/branch/*", context.RepoRefByType(context.RepoRefBranch), repo.SingleDownloadOrLFS)
|
|
|
|
|
m.Get("/tag/*", context.RepoRefByType(context.RepoRefTag), repo.SingleDownloadOrLFS)
|
|
|
|
|
m.Get("/commit/*", context.RepoRefByType(context.RepoRefCommit), repo.SingleDownloadOrLFS)
|
2021-01-26 16:36:53 +01:00
|
|
|
m.Get("/blob/{sha}", context.RepoRefByType(context.RepoRefBlob), repo.DownloadByIDOrLFS)
|
2019-02-12 16:09:43 +01:00
|
|
|
// "/*" route is deprecated, and kept for backward compatibility
|
|
|
|
|
m.Get("/*", context.RepoRefByType(context.RepoRefLegacy), repo.SingleDownloadOrLFS)
|
|
|
|
|
}, repo.MustBeNotEmpty, reqRepoCodeReader)
|
|
|
|
|
|
2017-10-30 03:04:25 +01:00
|
|
|
m.Group("/raw", func() {
|
|
|
|
|
m.Get("/branch/*", context.RepoRefByType(context.RepoRefBranch), repo.SingleDownload)
|
|
|
|
|
m.Get("/tag/*", context.RepoRefByType(context.RepoRefTag), repo.SingleDownload)
|
|
|
|
|
m.Get("/commit/*", context.RepoRefByType(context.RepoRefCommit), repo.SingleDownload)
|
2021-01-26 16:36:53 +01:00
|
|
|
m.Get("/blob/{sha}", context.RepoRefByType(context.RepoRefBlob), repo.DownloadByID)
|
2017-10-30 03:04:25 +01:00
|
|
|
// "/*" route is deprecated, and kept for backward compatibility
|
|
|
|
|
m.Get("/*", context.RepoRefByType(context.RepoRefLegacy), repo.SingleDownload)
|
2019-01-18 01:01:04 +01:00
|
|
|
}, repo.MustBeNotEmpty, reqRepoCodeReader)
|
2017-10-30 03:04:25 +01:00
|
|
|
|
2022-06-16 05:33:23 +02:00
|
|
|
m.Group("/render", func() {
|
|
|
|
|
m.Get("/branch/*", context.RepoRefByType(context.RepoRefBranch), repo.RenderFile)
|
|
|
|
|
m.Get("/tag/*", context.RepoRefByType(context.RepoRefTag), repo.RenderFile)
|
|
|
|
|
m.Get("/commit/*", context.RepoRefByType(context.RepoRefCommit), repo.RenderFile)
|
|
|
|
|
m.Get("/blob/{sha}", context.RepoRefByType(context.RepoRefBlob), repo.RenderFile)
|
|
|
|
|
}, repo.MustBeNotEmpty, reqRepoCodeReader)
|
|
|
|
|
|
2017-10-30 03:04:25 +01:00
|
|
|
m.Group("/commits", func() {
|
|
|
|
|
m.Get("/branch/*", context.RepoRefByType(context.RepoRefBranch), repo.RefCommits)
|
|
|
|
|
m.Get("/tag/*", context.RepoRefByType(context.RepoRefTag), repo.RefCommits)
|
|
|
|
|
m.Get("/commit/*", context.RepoRefByType(context.RepoRefCommit), repo.RefCommits)
|
|
|
|
|
// "/*" route is deprecated, and kept for backward compatibility
|
|
|
|
|
m.Get("/*", context.RepoRefByType(context.RepoRefLegacy), repo.RefCommits)
|
2019-01-18 01:01:04 +01:00
|
|
|
}, repo.MustBeNotEmpty, reqRepoCodeReader)
|
2017-10-30 03:04:25 +01:00
|
|
|
|
2019-04-20 04:47:00 +02:00
|
|
|
m.Group("/blame", func() {
|
|
|
|
|
m.Get("/branch/*", context.RepoRefByType(context.RepoRefBranch), repo.RefBlame)
|
|
|
|
|
m.Get("/tag/*", context.RepoRefByType(context.RepoRefTag), repo.RefBlame)
|
|
|
|
|
m.Get("/commit/*", context.RepoRefByType(context.RepoRefCommit), repo.RefBlame)
|
|
|
|
|
}, repo.MustBeNotEmpty, reqRepoCodeReader)
|
|
|
|
|
|
2017-04-25 09:24:51 +02:00
|
|
|
m.Group("", func() {
|
|
|
|
|
m.Get("/graph", repo.Graph)
|
2021-02-13 05:35:43 +01:00
|
|
|
m.Get("/commit/{sha:([a-f0-9]{7,40})$}", repo.SetEditorconfigIfExists, repo.SetDiffViewStyle, repo.SetWhitespaceBehavior, repo.Diff)
|
2023-07-27 12:47:41 +02:00
|
|
|
m.Get("/commit/{sha:([a-f0-9]{7,40})$}/load-branches-and-tags", repo.LoadBranchesAndTags)
|
2022-02-09 21:28:55 +01:00
|
|
|
m.Get("/cherry-pick/{sha:([a-f0-9]{7,40})$}", repo.SetEditorconfigIfExists, repo.CherryPick)
|
2019-01-18 01:01:04 +01:00
|
|
|
}, repo.MustBeNotEmpty, context.RepoRef(), reqRepoCodeReader)
|
2017-07-27 11:23:38 +02:00
|
|
|
|
2023-04-26 04:53:44 +02:00
|
|
|
m.Get("/rss/branch/*", context.RepoRefByType(context.RepoRefBranch), feedEnabled, feed.RenderBranchFeed)
|
|
|
|
|
m.Get("/atom/branch/*", context.RepoRefByType(context.RepoRefBranch), feedEnabled, feed.RenderBranchFeed)
|
2023-04-25 16:08:29 +02:00
|
|
|
|
2017-10-30 03:04:25 +01:00
|
|
|
m.Group("/src", func() {
|
|
|
|
|
m.Get("/branch/*", context.RepoRefByType(context.RepoRefBranch), repo.Home)
|
|
|
|
|
m.Get("/tag/*", context.RepoRefByType(context.RepoRefTag), repo.Home)
|
|
|
|
|
m.Get("/commit/*", context.RepoRefByType(context.RepoRefCommit), repo.Home)
|
|
|
|
|
// "/*" route is deprecated, and kept for backward compatibility
|
|
|
|
|
m.Get("/*", context.RepoRefByType(context.RepoRefLegacy), repo.Home)
|
|
|
|
|
}, repo.SetEditorconfigIfExists)
|
|
|
|
|
|
2017-07-27 11:23:38 +02:00
|
|
|
m.Group("", func() {
|
2017-04-25 09:24:51 +02:00
|
|
|
m.Get("/forks", repo.Forks)
|
2018-11-28 12:26:14 +01:00
|
|
|
}, context.RepoRef(), reqRepoCodeReader)
|
2023-04-27 08:06:45 +02:00
|
|
|
m.Get("/commit/{sha:([a-f0-9]{7,40})}.{ext:patch|diff}", repo.MustBeNotEmpty, reqRepoCodeReader, repo.RawDiff)
|
2021-04-10 02:26:08 +02:00
|
|
|
}, ignSignIn, context.RepoAssignment, context.UnitTypes())
|
2021-10-08 15:08:22 +02:00
|
|
|
|
|
|
|
|
m.Post("/{username}/{reponame}/lastcommit/*", ignSignInAndCsrf, context.RepoAssignment, context.UnitTypes(), context.RepoRefByType(context.RepoRefCommit), reqRepoCodeReader, repo.LastCommit)
|
|
|
|
|
|
2021-01-26 16:36:53 +01:00
|
|
|
m.Group("/{username}/{reponame}", func() {
|
2017-04-25 09:24:51 +02:00
|
|
|
m.Get("/stars", repo.Stars)
|
|
|
|
|
m.Get("/watchers", repo.Watchers)
|
2018-11-28 12:26:14 +01:00
|
|
|
m.Get("/search", reqRepoCodeReader, repo.Search)
|
2021-04-10 02:26:08 +02:00
|
|
|
}, ignSignIn, context.RepoAssignment, context.RepoRef(), context.UnitTypes())
|
2017-04-25 09:24:51 +02:00
|
|
|
|
2021-01-26 16:36:53 +01:00
|
|
|
m.Group("/{username}", func() {
|
|
|
|
|
m.Group("/{reponame}", func() {
|
2017-04-25 09:24:51 +02:00
|
|
|
m.Get("", repo.SetEditorconfigIfExists, repo.Home)
|
2021-05-09 23:50:06 +02:00
|
|
|
}, ignSignIn, context.RepoAssignment, context.RepoRef(), context.UnitTypes())
|
2017-04-25 09:24:51 +02:00
|
|
|
|
2021-01-26 16:36:53 +01:00
|
|
|
m.Group("/{reponame}", func() {
|
|
|
|
|
m.Group("/info/lfs", func() {
|
2021-06-06 01:59:27 +02:00
|
|
|
m.Post("/objects/batch", lfs.CheckAcceptMediaType, lfs.BatchHandler)
|
|
|
|
|
m.Put("/objects/{oid}/{size}", lfs.UploadHandler)
|
|
|
|
|
m.Get("/objects/{oid}/{filename}", lfs.DownloadHandler)
|
|
|
|
|
m.Get("/objects/{oid}", lfs.DownloadHandler)
|
|
|
|
|
m.Post("/verify", lfs.CheckAcceptMediaType, lfs.VerifyHandler)
|
2017-11-28 21:58:37 +01:00
|
|
|
m.Group("/locks", func() {
|
|
|
|
|
m.Get("/", lfs.GetListLockHandler)
|
|
|
|
|
m.Post("/", lfs.PostLockHandler)
|
|
|
|
|
m.Post("/verify", lfs.VerifyLockHandler)
|
2021-01-26 16:36:53 +01:00
|
|
|
m.Post("/{lid}/unlock", lfs.UnLockHandler)
|
2021-06-06 01:59:27 +02:00
|
|
|
}, lfs.CheckAcceptMediaType)
|
2017-04-25 09:24:51 +02:00
|
|
|
m.Any("/*", func(ctx *context.Context) {
|
2018-01-10 22:34:17 +01:00
|
|
|
ctx.NotFound("", nil)
|
2017-04-25 09:24:51 +02:00
|
|
|
})
|
2021-06-06 01:59:27 +02:00
|
|
|
}, ignSignInAndCsrf, lfsServerEnabled)
|
2021-01-26 16:36:53 +01:00
|
|
|
|
2023-11-02 15:14:33 +01:00
|
|
|
gitHTTPRouters(m)
|
2017-04-25 09:24:51 +02:00
|
|
|
})
|
|
|
|
|
})
|
|
|
|
|
// ***** END: Repository *****
|
|
|
|
|
|
|
|
|
|
m.Group("/notifications", func() {
|
|
|
|
|
m.Get("", user.Notifications)
|
2022-09-29 21:09:14 +02:00
|
|
|
m.Get("/subscriptions", user.NotificationSubscriptions)
|
|
|
|
|
m.Get("/watching", user.NotificationWatching)
|
2017-04-25 09:24:51 +02:00
|
|
|
m.Post("/status", user.NotificationStatusPost)
|
2017-12-07 06:52:57 +01:00
|
|
|
m.Post("/purge", user.NotificationPurgePost)
|
2022-04-07 20:59:56 +02:00
|
|
|
m.Get("/new", user.NewAvailable)
|
2017-04-25 09:24:51 +02:00
|
|
|
}, reqSignIn)
|
|
|
|
|
|
2018-07-28 02:19:01 +02:00
|
|
|
if setting.API.EnableSwagger {
|
2021-06-09 01:33:54 +02:00
|
|
|
m.Get("/swagger.v1.json", SwaggerV1Json)
|
2019-08-26 13:33:06 +02:00
|
|
|
}
|
2023-04-03 12:06:57 +02:00
|
|
|
|
|
|
|
|
if !setting.IsProd {
|
|
|
|
|
m.Any("/devtest", devtest.List)
|
2023-06-14 10:01:37 +02:00
|
|
|
m.Any("/devtest/fetch-action-test", devtest.FetchActionTest)
|
2023-04-03 12:06:57 +02:00
|
|
|
m.Any("/devtest/{sub}", devtest.Tmpl)
|
|
|
|
|
}
|
|
|
|
|
|
2021-12-22 11:39:28 +01:00
|
|
|
m.NotFound(func(w http.ResponseWriter, req *http.Request) {
|
2023-05-23 03:29:15 +02:00
|
|
|
ctx := context.GetWebContext(req)
|
2021-12-22 11:39:28 +01:00
|
|
|
ctx.NotFound("", nil)
|
|
|
|
|
})
|
2017-04-25 09:24:51 +02:00
|
|
|
}
|