Show messages for users if the ROOT_URL is wrong, show JavaScript errors (#18971)
* ROOT_URL issues: some users did wrong to there app.ini config, then:
* The assets can not be loaded (AppSubUrl != "" and users try to access http://host:3000/)
*The ROOT_URL is wrong, then many URLs in Gitea are broken.
Now Gitea show enough information to users.
* JavaScript error issues, there are many users affected by JavaScript errors, some are caused by frontend bugs, some are caused by broken customized templates. If these JS errors can be found at first time, then maintainers do not need to ask about how bug occurs again and again.
* Some people like to modify the `head.tmpl`, so we separate the script part to `head_script.tmpl`, then it's much safer.
* use specialized CSS class "js-global-error", end users still have a chance to hide error messages by customized CSS styles.
2022-03-30 07:52:24 +02:00
|
|
|
// bootstrap module must be the first one to be imported, it handles webpack lazy-loading and global errors
|
|
|
|
|
import './bootstrap.js';
|
2020-02-23 22:34:28 +01:00
|
|
|
|
2021-10-15 04:35:26 +02:00
|
|
|
import {initRepoActivityTopAuthorsChart} from './components/RepoActivityTopAuthors.vue';
|

Redesign Scoped Access Tokens (#24767)
## Changes
- Adds the following high level access scopes, each with `read` and
`write` levels:
- `activitypub`
- `admin` (hidden if user is not a site admin)
- `misc`
- `notification`
- `organization`
- `package`
- `issue`
- `repository`
- `user`
- Adds new middleware function `tokenRequiresScopes()` in addition to
`reqToken()`
- `tokenRequiresScopes()` is used for each high-level api section
- _if_ a scoped token is present, checks that the required scope is
included based on the section and HTTP method
- `reqToken()` is used for individual routes
- checks that required authentication is present (but does not check
scope levels as this will already have been handled by
`tokenRequiresScopes()`
- Adds migration to convert old scoped access tokens to the new set of
scopes
- Updates the user interface for scope selection
### User interface example
<img width="903" alt="Screen Shot 2023-05-31 at 1 56 55 PM"
src="https://github.com/go-gitea/gitea/assets/23248839/654766ec-2143-4f59-9037-3b51600e32f3">
<img width="917" alt="Screen Shot 2023-05-31 at 1 56 43 PM"
src="https://github.com/go-gitea/gitea/assets/23248839/1ad64081-012c-4a73-b393-66b30352654c">
## tokenRequiresScopes Design Decision
- `tokenRequiresScopes()` was added to more reliably cover api routes.
For an incoming request, this function uses the given scope category
(say `AccessTokenScopeCategoryOrganization`) and the HTTP method (say
`DELETE`) and verifies that any scoped tokens in use include
`delete:organization`.
- `reqToken()` is used to enforce auth for individual routes that
require it. If a scoped token is not present for a request,
`tokenRequiresScopes()` will not return an error
## TODO
- [x] Alphabetize scope categories
- [x] Change 'public repos only' to a radio button (private vs public).
Also expand this to organizations
- [X] Disable token creation if no scopes selected. Alternatively, show
warning
- [x] `reqToken()` is missing from many `POST/DELETE` routes in the api.
`tokenRequiresScopes()` only checks that a given token has the correct
scope, `reqToken()` must be used to check that a token (or some other
auth) is present.
- _This should be addressed in this PR_
- [x] The migration should be reviewed very carefully in order to
minimize access changes to existing user tokens.
- _This should be addressed in this PR_
- [x] Link to api to swagger documentation, clarify what
read/write/delete levels correspond to
- [x] Review cases where more than one scope is needed as this directly
deviates from the api definition.
- _This should be addressed in this PR_
- For example:
```go
m.Group("/users/{username}/orgs", func() {
m.Get("", reqToken(), org.ListUserOrgs)
m.Get("/{org}/permissions", reqToken(), org.GetUserOrgsPermissions)
}, tokenRequiresScopes(auth_model.AccessTokenScopeCategoryUser,
auth_model.AccessTokenScopeCategoryOrganization),
context_service.UserAssignmentAPI())
```
## Future improvements
- [ ] Add required scopes to swagger documentation
- [ ] Redesign `reqToken()` to be opt-out rather than opt-in
- [ ] Subdivide scopes like `repository`
- [ ] Once a token is created, if it has no scopes, we should display
text instead of an empty bullet point
- [ ] If the 'public repos only' option is selected, should read
categories be selected by default
Closes #24501
Closes #24799
Co-authored-by: Jonathan Tran <jon@allspice.io>
Co-authored-by: Kyle D <kdumontnu@gmail.com>
Co-authored-by: silverwind <me@silverwind.io>
2023-06-04 20:57:16 +02:00
|
|
|
import {initScopedAccessTokenCategories} from './components/ScopedAccessTokenSelector.vue';
|
2023-03-14 05:09:06 +01:00
|
|
|
import {initDashboardRepoList} from './components/DashboardRepoList.vue';
|
2021-10-15 04:35:26 +02:00
|
|
|
|
2022-12-23 17:03:11 +01:00
|
|
|
import {initGlobalCopyToClipboardListener} from './features/clipboard.js';
|
|
|
|
|
import {initContextPopups} from './features/contextpopup.js';
|
|
|
|
|
import {initRepoGraphGit} from './features/repo-graph.js';
|
|
|
|
|
import {initHeatmap} from './features/heatmap.js';
|
|
|
|
|
import {initImageDiff} from './features/imagediff.js';
|
|
|
|
|
import {initRepoMigration} from './features/repo-migration.js';
|
|
|
|
|
import {initRepoProject} from './features/repo-projects.js';
|
|
|
|
|
import {initTableSort} from './features/tablesort.js';
|
2022-10-17 01:29:26 +02:00
|
|
|
import {initAdminUserListSearchForm} from './features/admin/users.js';
|
|
|
|
|
import {initAdminConfigs} from './features/admin/config.js';
|
2021-05-07 10:43:41 +02:00
|
|
|
import {initMarkupAnchors} from './markup/anchors.js';
|
2021-10-16 19:28:04 +02:00
|
|
|
import {initNotificationCount, initNotificationsTable} from './features/notification.js';
|
2021-11-09 10:27:25 +01:00
|
|
|
import {initRepoIssueContentHistory} from './features/repo-issue-content.js';
|
2021-01-21 15:51:52 +01:00
|
|
|
import {initStopwatch} from './features/stopwatch.js';
|
2022-06-09 13:15:08 +02:00
|
|
|
import {initFindFileInRepo} from './features/repo-findfile.js';
|
2021-10-16 19:28:04 +02:00
|
|
|
import {initCommentContent, initMarkupContent} from './markup/content.js';
|
2023-05-29 14:10:00 +02:00
|
|
|
import {initPdfViewer} from './render/pdf.js';
|
2021-10-16 19:28:04 +02:00
|
|
|
|
|
|
|
|
import {initUserAuthLinkAccountView, initUserAuthOauth2} from './features/user-auth.js';
|
|
|
|
|
import {
|
|
|
|
|
initRepoIssueDue,
|
|
|
|
|
initRepoIssueReferenceRepositorySearch,
|
|
|
|
|
initRepoIssueTimeTracking,
|
|
|
|
|
initRepoIssueWipTitle,
|
|
|
|
|
initRepoPullRequestMergeInstruction,
|
2022-04-28 17:45:33 +02:00
|
|
|
initRepoPullRequestAllowMaintainerEdit,
|
2023-05-10 17:50:58 +02:00
|
|
|
initRepoPullRequestReview, initRepoIssueSidebarList
|
2021-10-16 19:28:04 +02:00
|
|
|
} from './features/repo-issue.js';
|
2022-04-26 21:09:46 +02:00
|
|
|
import {
|
|
|
|
|
initRepoEllipsisButton,
|
|
|
|
|
initRepoCommitLastCommitLoader,
|
|
|
|
|
initCommitStatuses,
|
|
|
|
|
} from './features/repo-commit.js';
|
2021-10-16 19:28:04 +02:00
|
|
|
import {
|
|
|
|
|
initFootLanguageMenu,
|
|
|
|
|
initGlobalButtonClickOnEnter,
|
|
|
|
|
initGlobalButtons,
|
|
|
|
|
initGlobalCommon,
|
|
|
|
|
initGlobalDropzone,
|
|
|
|
|
initGlobalEnterQuickSubmit,
|
|
|
|
|
initGlobalFormDirtyLeaveConfirm,
|
|
|
|
|
initGlobalLinkActions,
|
|
|
|
|
initHeadNavbarContentToggle,
|
|
|
|
|
} from './features/common-global.js';
|
|
|
|
|
import {initRepoTopicBar} from './features/repo-home.js';
|
2022-10-17 01:29:26 +02:00
|
|
|
import {initAdminEmails} from './features/admin/emails.js';
|
|
|
|
|
import {initAdminCommon} from './features/admin/common.js';
|
2021-10-16 19:28:04 +02:00
|
|
|
import {initRepoTemplateSearch} from './features/repo-template.js';
|
|
|
|
|
import {initRepoCodeView} from './features/repo-code.js';
|
|
|
|
|
import {initSshKeyFormParser} from './features/sshkey-helper.js';
|
|
|
|
|
import {initUserSettings} from './features/user-settings.js';
|
|
|
|
|
import {initRepoArchiveLinks} from './features/repo-common.js';
|
|
|
|
|
import {initRepoMigrationStatusChecker} from './features/repo-migrate.js';
|
|
|
|
|
import {
|
|
|
|
|
initRepoSettingGitHook,
|
|
|
|
|
initRepoSettingsCollaboration,
|
|
|
|
|
initRepoSettingSearchTeamBox,
|
|
|
|
|
} from './features/repo-settings.js';
|
2023-04-09 15:11:02 +02:00
|
|
|
import {initRepoDiffView} from './features/repo-diff.js';
|
2021-10-16 19:28:04 +02:00
|
|
|
import {initOrgTeamSearchRepoBox, initOrgTeamSettings} from './features/org-team.js';
|
2022-01-14 16:03:31 +01:00
|
|
|
import {initUserAuthWebAuthn, initUserAuthWebAuthnRegister} from './features/user-auth-webauthn.js';
|
2023-03-10 17:42:38 +01:00
|
|
|
import {initRepoRelease, initRepoReleaseNew} from './features/repo-release.js';
|
2021-10-16 19:28:04 +02:00
|
|
|
import {initRepoEditor} from './features/repo-editor.js';
|
2021-11-09 10:27:25 +01:00
|
|
|
import {initCompSearchUserBox} from './features/comp/SearchUserBox.js';
|
2021-10-16 19:28:04 +02:00
|
|
|
import {initInstall} from './features/install.js';
|
2021-11-09 10:27:25 +01:00
|
|
|
import {initCompWebHookEditor} from './features/comp/WebHookEditor.js';
|
2021-10-16 19:28:04 +02:00
|
|
|
import {initRepoBranchButton} from './features/repo-branch.js';
|
|
|
|
|
import {initCommonOrganization} from './features/common-organization.js';
|
|
|
|
|
import {initRepoWikiForm} from './features/repo-wiki.js';
|
|
|
|
|
import {initRepoCommentForm, initRepository} from './features/repo-legacy.js';
|
2022-11-21 10:59:42 +01:00
|
|
|
import {initCopyContent} from './features/copycontent.js';
|
2023-02-05 08:29:03 +01:00
|
|
|
import {initCaptcha} from './features/captcha.js';
|

Implement actions (#21937)
Close #13539.
Co-authored by: @lunny @appleboy @fuxiaohei and others.
Related projects:
- https://gitea.com/gitea/actions-proto-def
- https://gitea.com/gitea/actions-proto-go
- https://gitea.com/gitea/act
- https://gitea.com/gitea/act_runner
### Summary
The target of this PR is to bring a basic implementation of "Actions",
an internal CI/CD system of Gitea. That means even though it has been
merged, the state of the feature is **EXPERIMENTAL**, and please note
that:
- It is disabled by default;
- It shouldn't be used in a production environment currently;
- It shouldn't be used in a public Gitea instance currently;
- Breaking changes may be made before it's stable.
**Please comment on #13539 if you have any different product design
ideas**, all decisions reached there will be adopted here. But in this
PR, we don't talk about **naming, feature-creep or alternatives**.
### ⚠️ Breaking
`gitea-actions` will become a reserved user name. If a user with the
name already exists in the database, it is recommended to rename it.
### Some important reviews
- What is `DEFAULT_ACTIONS_URL` in `app.ini` for?
- https://github.com/go-gitea/gitea/pull/21937#discussion_r1055954954
- Why the api for runners is not under the normal `/api/v1` prefix?
- https://github.com/go-gitea/gitea/pull/21937#discussion_r1061173592
- Why DBFS?
- https://github.com/go-gitea/gitea/pull/21937#discussion_r1061301178
- Why ignore events triggered by `gitea-actions` bot?
- https://github.com/go-gitea/gitea/pull/21937#discussion_r1063254103
- Why there's no permission control for actions?
- https://github.com/go-gitea/gitea/pull/21937#discussion_r1090229868
### What it looks like
<details>
#### Manage runners
<img width="1792" alt="image"
src="https://user-images.githubusercontent.com/9418365/205870657-c72f590e-2e08-4cd4-be7f-2e0abb299bbf.png">
#### List runs
<img width="1792" alt="image"
src="https://user-images.githubusercontent.com/9418365/205872794-50fde990-2b45-48c1-a178-908e4ec5b627.png">
#### View logs
<img width="1792" alt="image"
src="https://user-images.githubusercontent.com/9418365/205872501-9b7b9000-9542-4991-8f55-18ccdada77c3.png">
</details>
### How to try it
<details>
#### 1. Start Gitea
Clone this branch and [install from
source](https://docs.gitea.io/en-us/install-from-source).
Add additional configurations in `app.ini` to enable Actions:
```ini
[actions]
ENABLED = true
```
Start it.
If all is well, you'll see the management page of runners:
<img width="1792" alt="image"
src="https://user-images.githubusercontent.com/9418365/205877365-8e30a780-9b10-4154-b3e8-ee6c3cb35a59.png">
#### 2. Start runner
Clone the [act_runner](https://gitea.com/gitea/act_runner), and follow
the
[README](https://gitea.com/gitea/act_runner/src/branch/main/README.md)
to start it.
If all is well, you'll see a new runner has been added:
<img width="1792" alt="image"
src="https://user-images.githubusercontent.com/9418365/205878000-216f5937-e696-470d-b66c-8473987d91c3.png">
#### 3. Enable actions for a repo
Create a new repo or open an existing one, check the `Actions` checkbox
in settings and submit.
<img width="1792" alt="image"
src="https://user-images.githubusercontent.com/9418365/205879705-53e09208-73c0-4b3e-a123-2dcf9aba4b9c.png">
<img width="1792" alt="image"
src="https://user-images.githubusercontent.com/9418365/205879383-23f3d08f-1a85-41dd-a8b3-54e2ee6453e8.png">
If all is well, you'll see a new tab "Actions":
<img width="1792" alt="image"
src="https://user-images.githubusercontent.com/9418365/205881648-a8072d8c-5803-4d76-b8a8-9b2fb49516c1.png">
#### 4. Upload workflow files
Upload some workflow files to `.gitea/workflows/xxx.yaml`, you can
follow the [quickstart](https://docs.github.com/en/actions/quickstart)
of GitHub Actions. Yes, Gitea Actions is compatible with GitHub Actions
in most cases, you can use the same demo:
```yaml
name: GitHub Actions Demo
run-name: ${{ github.actor }} is testing out GitHub Actions 🚀
on: [push]
jobs:
Explore-GitHub-Actions:
runs-on: ubuntu-latest
steps:
- run: echo "🎉 The job was automatically triggered by a ${{ github.event_name }} event."
- run: echo "🐧 This job is now running on a ${{ runner.os }} server hosted by GitHub!"
- run: echo "🔎 The name of your branch is ${{ github.ref }} and your repository is ${{ github.repository }}."
- name: Check out repository code
uses: actions/checkout@v3
- run: echo "💡 The ${{ github.repository }} repository has been cloned to the runner."
- run: echo "🖥️ The workflow is now ready to test your code on the runner."
- name: List files in the repository
run: |
ls ${{ github.workspace }}
- run: echo "🍏 This job's status is ${{ job.status }}."
```
If all is well, you'll see a new run in `Actions` tab:
<img width="1792" alt="image"
src="https://user-images.githubusercontent.com/9418365/205884473-79a874bc-171b-4aaf-acd5-0241a45c3b53.png">
#### 5. Check the logs of jobs
Click a run and you'll see the logs:
<img width="1792" alt="image"
src="https://user-images.githubusercontent.com/9418365/205884800-994b0374-67f7-48ff-be9a-4c53f3141547.png">
#### 6. Go on
You can try more examples in [the
documents](https://docs.github.com/en/actions/using-workflows/workflow-syntax-for-github-actions)
of GitHub Actions, then you might find a lot of bugs.
Come on, PRs are welcome.
</details>
See also: [Feature Preview: Gitea
Actions](https://blog.gitea.io/2022/12/feature-preview-gitea-actions/)
---------
Co-authored-by: a1012112796 <1012112796@qq.com>
Co-authored-by: Lunny Xiao <xiaolunwen@gmail.com>
Co-authored-by: delvh <dev.lh@web.de>
Co-authored-by: ChristopherHX <christopher.homberger@web.de>
Co-authored-by: John Olheiser <john.olheiser@gmail.com>
2023-01-31 02:45:19 +01:00
|
|
|
import {initRepositoryActionView} from './components/RepoActionView.vue';
|

Use a general approach to show tooltip, fix temporary tooltip bug (#23574)
## TLDR
* Improve performance: lazy creating the tippy instances.
* Transparently support all "tooltip" elements, no need to call
`initTooltip` again and again.
* Fix a temporary tooltip re-entrance bug, which causes showing temp
content forever.
* Upgrade vue3-calendar-heatmap to 2.0.2 with lazy tippy init
(initHeatmap time decreases from 100ms to 50ms)
## Details
### The performance
Creating a lot of tippy tooltip instances is expensive. This PR doesn't
create all tippy tooltip instances, instead, it only adds "mouseover"
event listener to necessary elements, and then switches to the tippy
tooltip
### The general approach for all tooltips
Before, dynamically generated tooltips need to be called with
`initTooltip`.
After, use MutationObserver to:
* Attach the event listeners to newly created tooltip elements, work for
Vue (easier than before)
* Catch changed attributes and update the tooltip content (better than
before)
It does help a lot, eg:
https://github.com/go-gitea/gitea/blob/1a4efa0ee9a49d48549be7479a46be133b9bc260/web_src/js/components/PullRequestMergeForm.vue#L33-L36
### Temporary tooltip re-entrance bug
To reproduce, on try.gitea.io, click the "copy clone url" quickly, then
the tooltip will be "Copied!" forever.
After this PR, with the help of `attachTippyTooltip`, the tooltip
content could be reset to the default correctly.
### Other changes
* `data-tooltip-content` is preferred from now on, the old
`data-content` may cause conflicts with other modules.
* `data-placement` was only used for tooltip, so it's renamed to
`data-tooltip-placement`, and removed from `createTippy`.
2023-03-23 10:56:15 +01:00
|
|
|
import {initGlobalTooltips} from './modules/tippy.js';
|

Fine tune more downdrop settings, use SVG for labels, improve Repo Topic Edit form (#23626)
Although it seems that some different purposes are mixed in this PR,
however, they are all related, and can be tested together, so I put them
together to save everyone's time.
Diff: `+79 −84`, everything becomes much better.
### Improve the dropdown settings.
Move all fomantic-init related code into our `fomantic.js`
Fine-tune some dropdown global settings, see the comments.
Also help to fix the first problem in #23625 , cc: @yp05327
The "language" menu has been simplified, and it works with small-height
window better.
### Use SVG instead of `<i class="delete icon">`
It's also done by `$.fn.dropdown.settings.templates.label` , cc:
@silverwind
### Remove incorrect `tabable` CSS class
It doesn't have CSS styles, and it was only in Vue. So it's totally
unnecessary, remove it by the way.
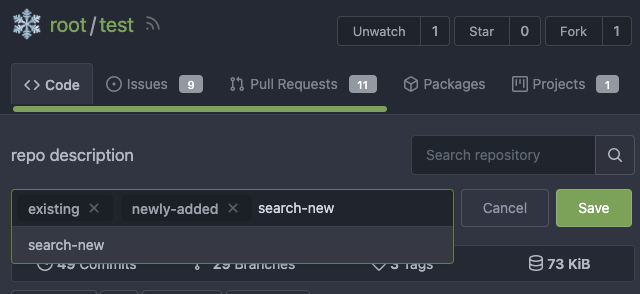
### Improve the Repo Topic Edit form
* Simplify the code
* Add a "Cancel" button
* Align elements
Before:
<details>
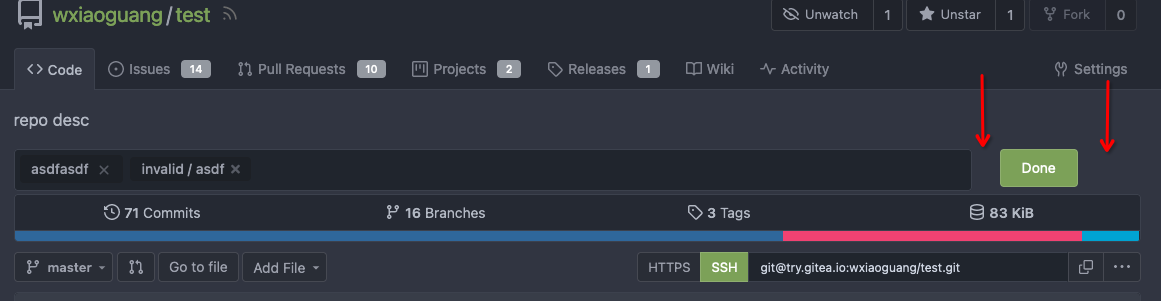
</details>
After:
2023-03-26 13:31:26 +02:00
|
|
|
import {initGiteaFomantic} from './modules/fomantic.js';
|
2023-04-02 00:40:22 +02:00
|
|
|
import {onDomReady} from './utils/dom.js';
|
2023-04-07 02:11:02 +02:00
|
|
|
import {initRepoIssueList} from './features/repo-issue-list.js';
|
2023-05-10 17:50:58 +02:00
|
|
|
import {initCommonIssueListQuickGoto} from './features/common-issue-list.js';
|
2022-06-12 14:08:23 +02:00
|
|
|
|

Fine tune more downdrop settings, use SVG for labels, improve Repo Topic Edit form (#23626)
Although it seems that some different purposes are mixed in this PR,
however, they are all related, and can be tested together, so I put them
together to save everyone's time.
Diff: `+79 −84`, everything becomes much better.
### Improve the dropdown settings.
Move all fomantic-init related code into our `fomantic.js`
Fine-tune some dropdown global settings, see the comments.
Also help to fix the first problem in #23625 , cc: @yp05327
The "language" menu has been simplified, and it works with small-height
window better.
### Use SVG instead of `<i class="delete icon">`
It's also done by `$.fn.dropdown.settings.templates.label` , cc:
@silverwind
### Remove incorrect `tabable` CSS class
It doesn't have CSS styles, and it was only in Vue. So it's totally
unnecessary, remove it by the way.
### Improve the Repo Topic Edit form
* Simplify the code
* Add a "Cancel" button
* Align elements
Before:
<details>

</details>
After:

2023-03-26 13:31:26 +02:00
|
|
|
// Init Gitea's Fomantic settings
|
|
|
|
|
initGiteaFomantic();
|
2019-11-14 22:39:51 +01:00
|
|
|
|
2023-04-02 00:40:22 +02:00
|
|
|
onDomReady(() => {
|
2021-10-16 19:28:04 +02:00
|
|
|
initGlobalCommon();
|
2021-11-09 10:27:25 +01:00
|
|
|
|
2022-08-09 14:37:34 +02:00
|
|
|
initGlobalTooltips();
|
2021-11-09 10:27:25 +01:00
|
|
|
initGlobalButtonClickOnEnter();
|
|
|
|
|
initGlobalButtons();
|
|
|
|
|
initGlobalCopyToClipboardListener();
|
2021-10-16 19:28:04 +02:00
|
|
|
initGlobalDropzone();
|
2021-11-09 10:27:25 +01:00
|
|
|
initGlobalEnterQuickSubmit();
|
|
|
|
|
initGlobalFormDirtyLeaveConfirm();
|
2021-10-16 19:28:04 +02:00
|
|
|
initGlobalLinkActions();
|
2021-11-09 10:27:25 +01:00
|
|
|
|
|
|
|
|
initCommonOrganization();
|
2023-05-10 17:50:58 +02:00
|
|
|
initCommonIssueListQuickGoto();
|
2019-11-14 22:39:51 +01:00
|
|
|
|
2021-11-09 10:27:25 +01:00
|
|
|
initCompSearchUserBox();
|
|
|
|
|
initCompWebHookEditor();
|
2019-11-14 22:39:51 +01:00
|
|
|
|
|
|
|
|
initInstall();
|
2021-11-09 10:27:25 +01:00
|
|
|
|
|
|
|
|
initHeadNavbarContentToggle();
|
|
|
|
|
initFootLanguageMenu();
|
|
|
|
|
|
|
|
|
|
initCommentContent();
|
|
|
|
|
initContextPopups();
|
|
|
|
|
initHeatmap();
|
|
|
|
|
initImageDiff();
|
|
|
|
|
initMarkupAnchors();
|
|
|
|
|
initMarkupContent();
|
|
|
|
|
initSshKeyFormParser();
|
|
|
|
|
initStopwatch();
|
|
|
|
|
initTableSort();
|
2022-06-09 13:15:08 +02:00
|
|
|
initFindFileInRepo();
|
2022-11-21 10:59:42 +01:00
|
|
|
initCopyContent();
|
2021-11-09 10:27:25 +01:00
|
|
|
|
2021-10-16 19:28:04 +02:00
|
|
|
initAdminCommon();
|
2021-11-09 10:27:25 +01:00
|
|
|
initAdminEmails();
|
|
|
|
|
initAdminUserListSearchForm();
|
2022-10-17 01:29:26 +02:00
|
|
|
initAdminConfigs();
|
2021-11-09 10:27:25 +01:00
|
|
|
|
2021-10-15 04:35:26 +02:00
|
|
|
initDashboardRepoList();
|
2021-11-09 10:27:25 +01:00
|
|
|
|
|
|
|
|
initNotificationCount();
|
|
|
|
|
initNotificationsTable();
|
|
|
|
|
|
|
|
|
|
initOrgTeamSearchRepoBox();
|
2021-10-16 19:28:04 +02:00
|
|
|
initOrgTeamSettings();
|
2021-11-09 10:27:25 +01:00
|
|
|
|
|
|
|
|
initRepoActivityTopAuthorsChart();
|
|
|
|
|
initRepoArchiveLinks();
|
|
|
|
|
initRepoBranchButton();
|
|
|
|
|
initRepoCodeView();
|
|
|
|
|
initRepoCommentForm();
|
2021-11-23 03:44:38 +01:00
|
|
|
initRepoEllipsisButton();
|
2021-11-09 10:27:25 +01:00
|
|
|
initRepoCommitLastCommitLoader();
|
|
|
|
|
initRepoEditor();
|
|
|
|
|
initRepoGraphGit();
|
|
|
|
|
initRepoIssueContentHistory();
|
|
|
|
|
initRepoIssueDue();
|
2021-10-16 19:28:04 +02:00
|
|
|
initRepoIssueList();
|
2023-04-07 02:11:02 +02:00
|
|
|
initRepoIssueSidebarList();
|
2021-11-09 10:27:25 +01:00
|
|
|
initRepoIssueReferenceRepositorySearch();
|
2021-10-16 19:28:04 +02:00
|
|
|
initRepoIssueTimeTracking();
|
|
|
|
|
initRepoIssueWipTitle();
|
2021-11-09 10:27:25 +01:00
|
|
|
initRepoMigration();
|
2021-10-16 19:28:04 +02:00
|
|
|
initRepoMigrationStatusChecker();
|
2021-11-09 10:27:25 +01:00
|
|
|
initRepoProject();
|
2021-10-16 19:28:04 +02:00
|
|
|
initRepoPullRequestMergeInstruction();
|
2022-04-28 17:45:33 +02:00
|
|
|
initRepoPullRequestAllowMaintainerEdit();
|
2021-11-09 10:27:25 +01:00
|
|
|
initRepoPullRequestReview();
|
2021-10-16 19:28:04 +02:00
|
|
|
initRepoRelease();
|
2023-03-10 17:42:38 +01:00
|
|
|
initRepoReleaseNew();
|
2021-11-09 10:27:25 +01:00
|
|
|
initRepoSettingGitHook();
|
|
|
|
|
initRepoSettingSearchTeamBox();
|
2021-10-16 19:28:04 +02:00
|
|
|
initRepoSettingsCollaboration();
|
2021-11-09 10:27:25 +01:00
|
|
|
initRepoTemplateSearch();
|
|
|
|
|
initRepoTopicBar();
|
|
|
|
|
initRepoWikiForm();
|
|
|
|
|
initRepository();
|

Implement actions (#21937)
Close #13539.
Co-authored by: @lunny @appleboy @fuxiaohei and others.
Related projects:
- https://gitea.com/gitea/actions-proto-def
- https://gitea.com/gitea/actions-proto-go
- https://gitea.com/gitea/act
- https://gitea.com/gitea/act_runner
### Summary
The target of this PR is to bring a basic implementation of "Actions",
an internal CI/CD system of Gitea. That means even though it has been
merged, the state of the feature is **EXPERIMENTAL**, and please note
that:
- It is disabled by default;
- It shouldn't be used in a production environment currently;
- It shouldn't be used in a public Gitea instance currently;
- Breaking changes may be made before it's stable.
**Please comment on #13539 if you have any different product design
ideas**, all decisions reached there will be adopted here. But in this
PR, we don't talk about **naming, feature-creep or alternatives**.
### ⚠️ Breaking
`gitea-actions` will become a reserved user name. If a user with the
name already exists in the database, it is recommended to rename it.
### Some important reviews
- What is `DEFAULT_ACTIONS_URL` in `app.ini` for?
- https://github.com/go-gitea/gitea/pull/21937#discussion_r1055954954
- Why the api for runners is not under the normal `/api/v1` prefix?
- https://github.com/go-gitea/gitea/pull/21937#discussion_r1061173592
- Why DBFS?
- https://github.com/go-gitea/gitea/pull/21937#discussion_r1061301178
- Why ignore events triggered by `gitea-actions` bot?
- https://github.com/go-gitea/gitea/pull/21937#discussion_r1063254103
- Why there's no permission control for actions?
- https://github.com/go-gitea/gitea/pull/21937#discussion_r1090229868
### What it looks like
<details>
#### Manage runners
<img width="1792" alt="image"
src="https://user-images.githubusercontent.com/9418365/205870657-c72f590e-2e08-4cd4-be7f-2e0abb299bbf.png">
#### List runs
<img width="1792" alt="image"
src="https://user-images.githubusercontent.com/9418365/205872794-50fde990-2b45-48c1-a178-908e4ec5b627.png">
#### View logs
<img width="1792" alt="image"
src="https://user-images.githubusercontent.com/9418365/205872501-9b7b9000-9542-4991-8f55-18ccdada77c3.png">
</details>
### How to try it
<details>
#### 1. Start Gitea
Clone this branch and [install from
source](https://docs.gitea.io/en-us/install-from-source).
Add additional configurations in `app.ini` to enable Actions:
```ini
[actions]
ENABLED = true
```
Start it.
If all is well, you'll see the management page of runners:
<img width="1792" alt="image"
src="https://user-images.githubusercontent.com/9418365/205877365-8e30a780-9b10-4154-b3e8-ee6c3cb35a59.png">
#### 2. Start runner
Clone the [act_runner](https://gitea.com/gitea/act_runner), and follow
the
[README](https://gitea.com/gitea/act_runner/src/branch/main/README.md)
to start it.
If all is well, you'll see a new runner has been added:
<img width="1792" alt="image"
src="https://user-images.githubusercontent.com/9418365/205878000-216f5937-e696-470d-b66c-8473987d91c3.png">
#### 3. Enable actions for a repo
Create a new repo or open an existing one, check the `Actions` checkbox
in settings and submit.
<img width="1792" alt="image"
src="https://user-images.githubusercontent.com/9418365/205879705-53e09208-73c0-4b3e-a123-2dcf9aba4b9c.png">
<img width="1792" alt="image"
src="https://user-images.githubusercontent.com/9418365/205879383-23f3d08f-1a85-41dd-a8b3-54e2ee6453e8.png">
If all is well, you'll see a new tab "Actions":
<img width="1792" alt="image"
src="https://user-images.githubusercontent.com/9418365/205881648-a8072d8c-5803-4d76-b8a8-9b2fb49516c1.png">
#### 4. Upload workflow files
Upload some workflow files to `.gitea/workflows/xxx.yaml`, you can
follow the [quickstart](https://docs.github.com/en/actions/quickstart)
of GitHub Actions. Yes, Gitea Actions is compatible with GitHub Actions
in most cases, you can use the same demo:
```yaml
name: GitHub Actions Demo
run-name: ${{ github.actor }} is testing out GitHub Actions 🚀
on: [push]
jobs:
Explore-GitHub-Actions:
runs-on: ubuntu-latest
steps:
- run: echo "🎉 The job was automatically triggered by a ${{ github.event_name }} event."
- run: echo "🐧 This job is now running on a ${{ runner.os }} server hosted by GitHub!"
- run: echo "🔎 The name of your branch is ${{ github.ref }} and your repository is ${{ github.repository }}."
- name: Check out repository code
uses: actions/checkout@v3
- run: echo "💡 The ${{ github.repository }} repository has been cloned to the runner."
- run: echo "🖥️ The workflow is now ready to test your code on the runner."
- name: List files in the repository
run: |
ls ${{ github.workspace }}
- run: echo "🍏 This job's status is ${{ job.status }}."
```
If all is well, you'll see a new run in `Actions` tab:
<img width="1792" alt="image"
src="https://user-images.githubusercontent.com/9418365/205884473-79a874bc-171b-4aaf-acd5-0241a45c3b53.png">
#### 5. Check the logs of jobs
Click a run and you'll see the logs:
<img width="1792" alt="image"
src="https://user-images.githubusercontent.com/9418365/205884800-994b0374-67f7-48ff-be9a-4c53f3141547.png">
#### 6. Go on
You can try more examples in [the
documents](https://docs.github.com/en/actions/using-workflows/workflow-syntax-for-github-actions)
of GitHub Actions, then you might find a lot of bugs.
Come on, PRs are welcome.
</details>
See also: [Feature Preview: Gitea
Actions](https://blog.gitea.io/2022/12/feature-preview-gitea-actions/)
---------
Co-authored-by: a1012112796 <1012112796@qq.com>
Co-authored-by: Lunny Xiao <xiaolunwen@gmail.com>
Co-authored-by: delvh <dev.lh@web.de>
Co-authored-by: ChristopherHX <christopher.homberger@web.de>
Co-authored-by: John Olheiser <john.olheiser@gmail.com>
2023-01-31 02:45:19 +01:00
|
|
|
initRepositoryActionView();
|
2019-11-14 22:39:51 +01:00
|
|
|
|
2022-04-26 21:09:46 +02:00
|
|
|
initCommitStatuses();
|
2023-02-05 08:29:03 +01:00
|
|
|
initCaptcha();
|
2022-04-26 21:09:46 +02:00
|
|
|
|
2021-11-09 10:27:25 +01:00
|
|
|
initUserAuthLinkAccountView();
|
|
|
|
|
initUserAuthOauth2();
|
2022-01-14 16:03:31 +01:00
|
|
|
initUserAuthWebAuthn();
|
|
|
|
|
initUserAuthWebAuthnRegister();
|
2021-11-09 10:27:25 +01:00
|
|
|
initUserSettings();
|
2023-04-09 15:11:02 +02:00
|
|
|
initRepoDiffView();
|
2023-05-29 14:10:00 +02:00
|
|
|
initPdfViewer();
|

Redesign Scoped Access Tokens (#24767)
## Changes
- Adds the following high level access scopes, each with `read` and
`write` levels:
- `activitypub`
- `admin` (hidden if user is not a site admin)
- `misc`
- `notification`
- `organization`
- `package`
- `issue`
- `repository`
- `user`
- Adds new middleware function `tokenRequiresScopes()` in addition to
`reqToken()`
- `tokenRequiresScopes()` is used for each high-level api section
- _if_ a scoped token is present, checks that the required scope is
included based on the section and HTTP method
- `reqToken()` is used for individual routes
- checks that required authentication is present (but does not check
scope levels as this will already have been handled by
`tokenRequiresScopes()`
- Adds migration to convert old scoped access tokens to the new set of
scopes
- Updates the user interface for scope selection
### User interface example
<img width="903" alt="Screen Shot 2023-05-31 at 1 56 55 PM"
src="https://github.com/go-gitea/gitea/assets/23248839/654766ec-2143-4f59-9037-3b51600e32f3">
<img width="917" alt="Screen Shot 2023-05-31 at 1 56 43 PM"
src="https://github.com/go-gitea/gitea/assets/23248839/1ad64081-012c-4a73-b393-66b30352654c">
## tokenRequiresScopes Design Decision
- `tokenRequiresScopes()` was added to more reliably cover api routes.
For an incoming request, this function uses the given scope category
(say `AccessTokenScopeCategoryOrganization`) and the HTTP method (say
`DELETE`) and verifies that any scoped tokens in use include
`delete:organization`.
- `reqToken()` is used to enforce auth for individual routes that
require it. If a scoped token is not present for a request,
`tokenRequiresScopes()` will not return an error
## TODO
- [x] Alphabetize scope categories
- [x] Change 'public repos only' to a radio button (private vs public).
Also expand this to organizations
- [X] Disable token creation if no scopes selected. Alternatively, show
warning
- [x] `reqToken()` is missing from many `POST/DELETE` routes in the api.
`tokenRequiresScopes()` only checks that a given token has the correct
scope, `reqToken()` must be used to check that a token (or some other
auth) is present.
- _This should be addressed in this PR_
- [x] The migration should be reviewed very carefully in order to
minimize access changes to existing user tokens.
- _This should be addressed in this PR_
- [x] Link to api to swagger documentation, clarify what
read/write/delete levels correspond to
- [x] Review cases where more than one scope is needed as this directly
deviates from the api definition.
- _This should be addressed in this PR_
- For example:
```go
m.Group("/users/{username}/orgs", func() {
m.Get("", reqToken(), org.ListUserOrgs)
m.Get("/{org}/permissions", reqToken(), org.GetUserOrgsPermissions)
}, tokenRequiresScopes(auth_model.AccessTokenScopeCategoryUser,
auth_model.AccessTokenScopeCategoryOrganization),
context_service.UserAssignmentAPI())
```
## Future improvements
- [ ] Add required scopes to swagger documentation
- [ ] Redesign `reqToken()` to be opt-out rather than opt-in
- [ ] Subdivide scopes like `repository`
- [ ] Once a token is created, if it has no scopes, we should display
text instead of an empty bullet point
- [ ] If the 'public repos only' option is selected, should read
categories be selected by default
Closes #24501
Closes #24799
Co-authored-by: Jonathan Tran <jon@allspice.io>
Co-authored-by: Kyle D <kdumontnu@gmail.com>
Co-authored-by: silverwind <me@silverwind.io>
2023-06-04 20:57:16 +02:00
|
|
|
initScopedAccessTokenCategories();
|
2019-11-14 22:39:51 +01:00
|
|
|
});
|